Bubble
Results
1
issues of
Bubble
# analysis The location of the vulnerability is line 55 in \taocms\include\Model\File.php and we can see that the path parameter is passed directly to file_get_contents function without filtering  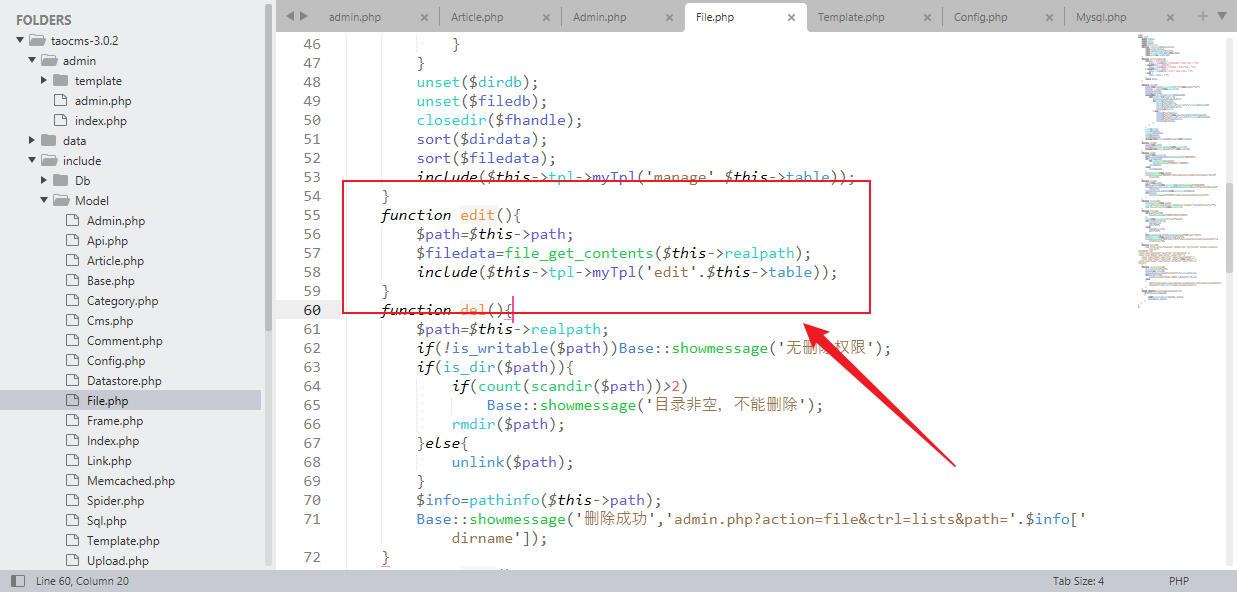...
