uzlonewolf
uzlonewolf
Parallel-socket theory of operation: There are 3 different types of sockets: force-scan connection attempts, broadcast-discovered status polling, and the UDP broadcast receiver. All 3 are stuffed into either the "waiting...
It is. I've basically rewritten it yet again since that last commit but haven't pushed it yet as it's not done. I got passive broadcast listening working again so I'll...
With 10 devices in my devices.json file (all online), `python3 -m tinytuya devices` now takes ~6 seconds and `snapshot`/`json` are under 2 seconds. If there are offline devices then `devices`...
Hmm, that response is command 8 (STATUS) despite the request being command 7 (CONTROL). It also seems to decode properly with the real key to `b'{"devId":"03200160ecfabc8d9700","dps":{"4":162},"t":1663207186,"s":84738}'` so I suspect it...
I actually went hunting for some right after I made that post, so hopefully I have some on the way. If they show up without v3.1 on them I'll take...
Force scanning now (mostly) works. Device identification for v3.1 devices is not fully implemented yet. For v3.3 devices it provokes an encrypted error message and then starts trying to decrypt...
Can you change scanner.py line 940 and change `debug_ips = []` to `debug_ips = ["10.0.1.36"]` and let me know what it's saying about that mis-identifying device?
I haven't pushed it yet but I added a filter for 127.\*.\*.\* and made it prompt "Y/n" for each network when verbose=True. 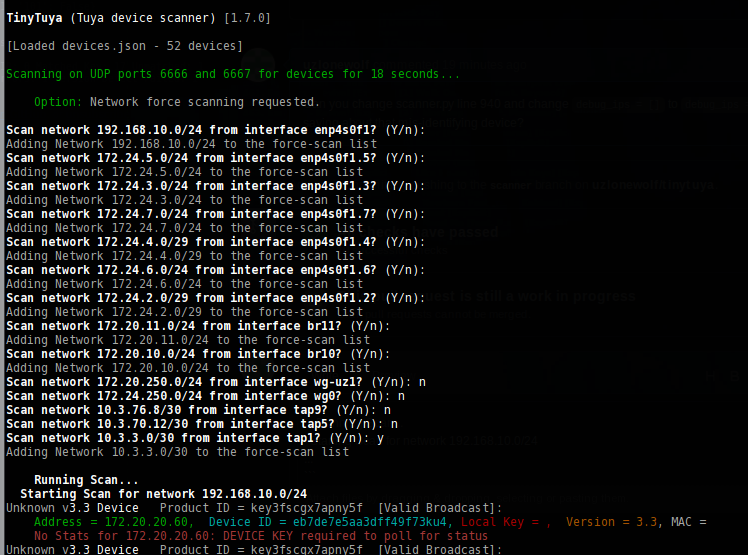
Hmm, that debug output is interesting. It is working, it just doesn't print much for individual devices (your screen would be absolutely flooded if it was enabled for every device...
That does help - it looks like the force-scan and broadcast-poll are fighting for control over the device. For now I'll make it so broadcasts are ignored when a device...