Saumeya Katyal
Saumeya Katyal
closes #9752 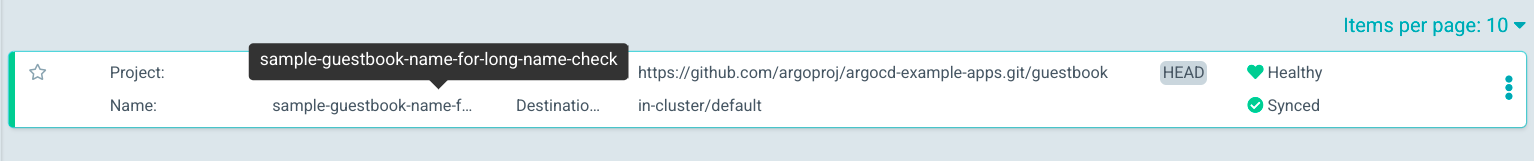 Signed-off-by: saumeya Note on DCO: If the DCO action in the integration test fails, one or more of your commits are not signed off....
View steps to test in the upstream ticket Upstream ticket - https://github.com/argoproj/argo-cd/pull/9703 The main logic for creating the theme map is in this file - https://github.com/argoproj/argo-ui/pull/245/files#diff-9be47d1a6668e34bf14bd39d2c830ecd572725cac9912f2bcd5e9b6d512ec0f1 In this approach, it...
Signed-off-by: saumeya **What type of PR is this?** /kind enhancement **What does this PR do / why we need it**: This PR adds default nodeSelector for running argoCD pod only...
closes #4722 Dependent on argo-ui PR - https://github.com/argoproj/argo-ui/pull/245 Steps to build and run, checkout to `argo-ui` **PR branch** in your local. Run `yalc publish` Then in this argocd branch `cd...
Signed-off-by: saumeya **What type of PR is this?** /kind documentation **What does this PR do / why we need it**: **Have you updated the necessary documentation?** * [x] Documentation update...
Signed-off-by: saumeya **What type of PR is this?** > Uncomment only one ` /kind` line, and delete the rest. > For example, `> /kind bug` would simply become: `/kind bug`...
# Summary As mentioned in this issue https://github.com/argoproj/argo-cd/issues/3113 the CLI option to skip verification for helm repos is missing the checkbox in the UI. This already exists for the Git...
Signed-off-by: saumeya **What type of PR is this?** > Uncomment only one ` /kind` line, and delete the rest. > For example, `> /kind bug` would simply become: `/kind bug`...
### Bug report CVE-2024-4068 - Upgrade micromatch to 4.0.7 - it is already addressed in http-proxy-middleware. Upgrading that should fix this. ### Actual Behavior ### Expected Behavior ### How Do...
Micromatch version to be upgraded to 4.0.7 to address this CVE
