pipelines-as-code
 pipelines-as-code copied to clipboard
pipelines-as-code copied to clipboard
Pipelines-as-Code for Tekton
Discussion: https://docs.google.com/document/d/1uZAC5GAGOd9-fu3S_EWadrlFYs8oxxqAk5D5mpx7gY0/edit?disco=AAAAhSNojQo ``` $ tkn-pac create repo ? Enter the Git repository url containing the pipelines (default: https://github.com/tektoncd/triggers): ? Please enter the namespace where the pipeline should run (default: triggers-pipelines):...
## Why is this useful * Users wouldn't know the webhook-secret created for the git provider if they don't create a Repository CR. We solve this issue by providing `--webhook-secret`...
# Changes As of now pipeline-as-code runs on amd64 platform. This PR will Add support for ppc64le, s390x platform. # Submitter Checklist - [ ] ♽ Run `make test lint`...
When creating the webhook token with the CLI we can instead use fine grained personal access token for github webook ; https://github.blog/2022-10-18-introducing-fine-grained-personal-access-tokens-for-github/
cf: 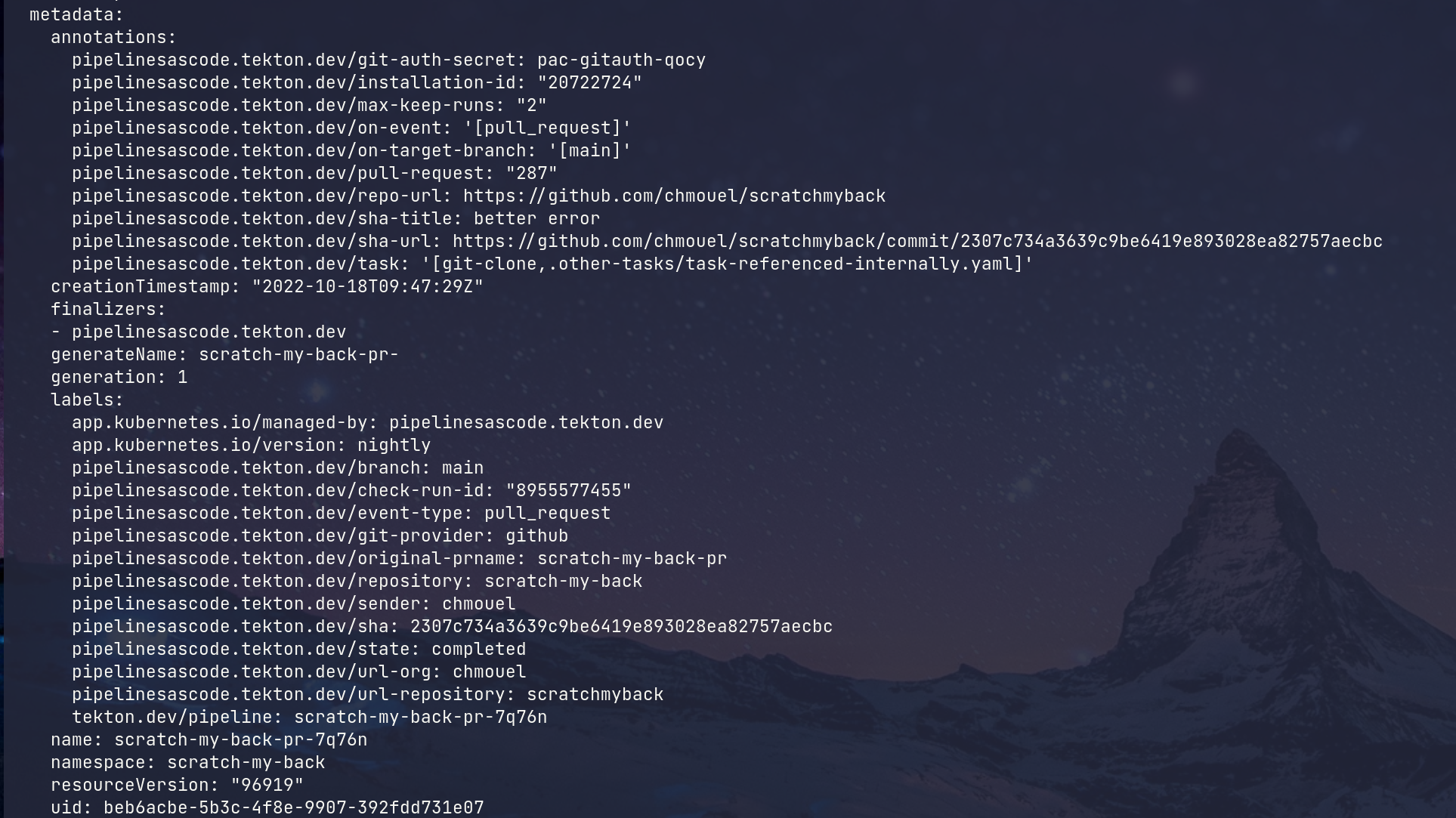 while the status has it :  cc @sm43
we show the last merge commit in UI/pac describe :  storing it in the labels from the controller when creating the pipelinerun but merge commit are not very interesting...
As mentioned here https://github.com/openshift-pipelines/pipelines-as-code/blob/cfdd8f2331d12bfd0e3cf6028de993f24b3197fc/pkg/provider/github/github.go#L23-L28 We are only supporting public raw github url, we need to handle it in GHE. I believe detecting if it's a raw.${GHE_URL} in this condition https://github.com/openshift-pipelines/pipelines-as-code/blob/cfdd8f2331d12bfd0e3cf6028de993f24b3197fc/pkg/provider/github/github.go#L48...
Lets say I set up PAC for a repo with associated Kubernetes namespace. Aside from careful PR review policies, what's to stop someone modifying the PipelineRun in `.tekton` to include...
https://github.com/openshift-pipelines/pipelines-as-code/blob/1fdf133637a34c781fa2f44269a6e8e01eb15a0d/.github/workflows/kind-e2e-tests.yaml#L65
We generate a secret automatically, but if the user didn't create a repo she/he would not know which secret that has been setup on the github interface (it's hidden). Let...
