Kenneth
Kenneth
Very interested in this, it would be a great addition to external-secrets.
I'd like to have this functionality as well. In the meantime, there's a workaround that provides similar functionality by using a custom variable: 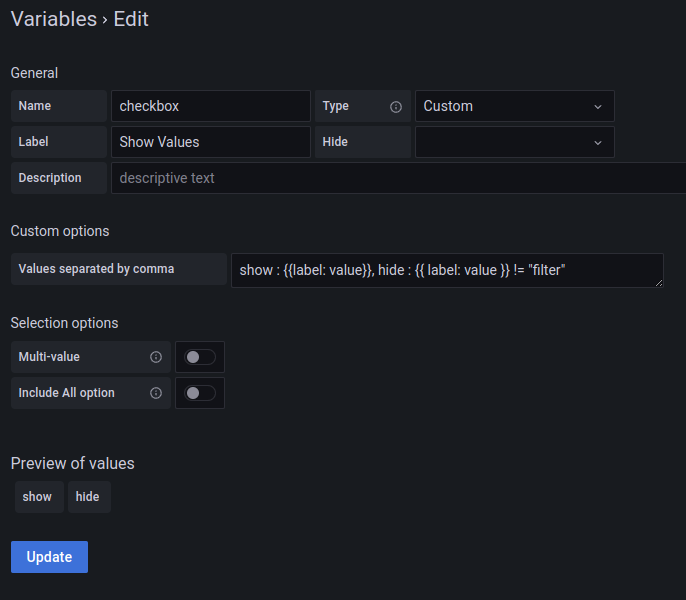
@faizanahmad055 If you're generating k8s manifests using `helm template`, the `.Capabilities.APIVersions.Has` function won't work. There are many use cases for `helm template`, including applying the changes to an external cluster...
~~Was this actually released? The release page for `1.17.0` says not to use it, and even on `1.18.0` there is no `delete` command for `tcl namespace`.~~ Namespaces can be deleted...
> job that regularly renews the credentials and puts them in the secrets engine for use by external-secrets operator. @ajpauwels what's the benefit of doing this vs having the job...
I believe this could be solved by replacing this: ``` {{- print "password" -}} ``` With something like: ``` {{- $storeConfig.sql.secretKey -}} ```
The initial list looks great! One thing I would add to it is avoiding the use of a default admin password, maybe making it a required environment variable or requesting...
This is still relevant. We are using an external script to create the playlists as a workaround, but it would be nice to use the same mechanism as dashboards.
Here is my workaround script: https://gist.github.com/kenske/d10f34de0e63e4cf2efa225724baef20