jinny
jinny
Version:3.4.0 Payload: app.alert('xss'); Insert xss malicious code in pdf with pdf editor  Access the file upload function of GetSimpleCMS, upload a malicious pdf, and get the uploaded file path...
Version:3.4.0a Payload: '"> At Snippets, click on ADD SNIPPEN and edit Snippets to XSS. 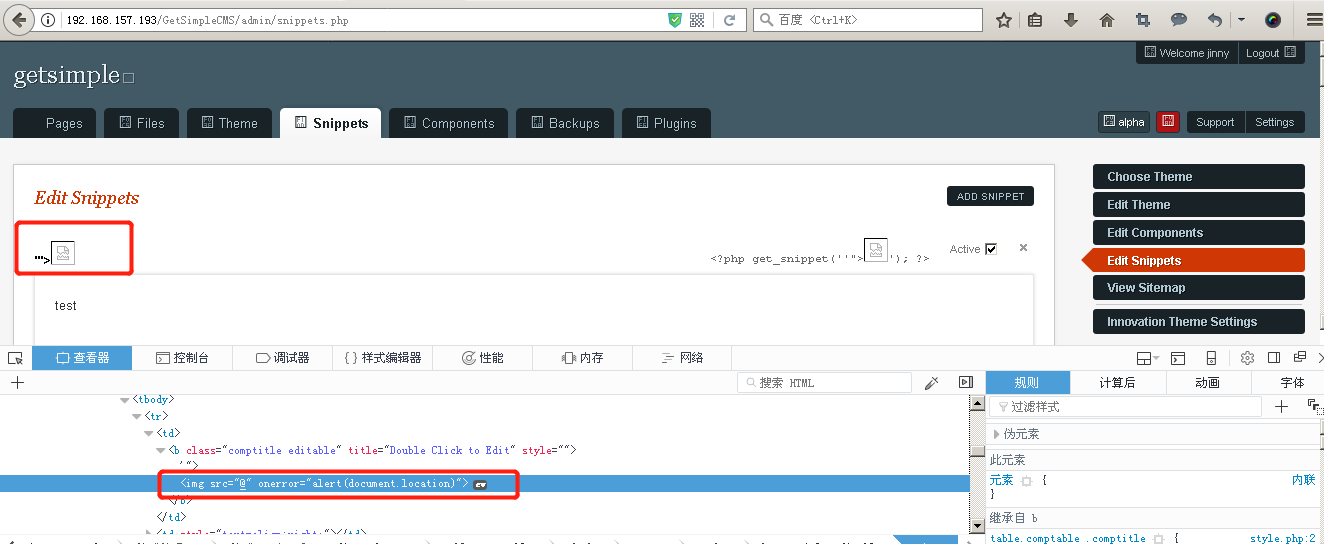 Click Save Snippets to save and refresh the trigger XSS 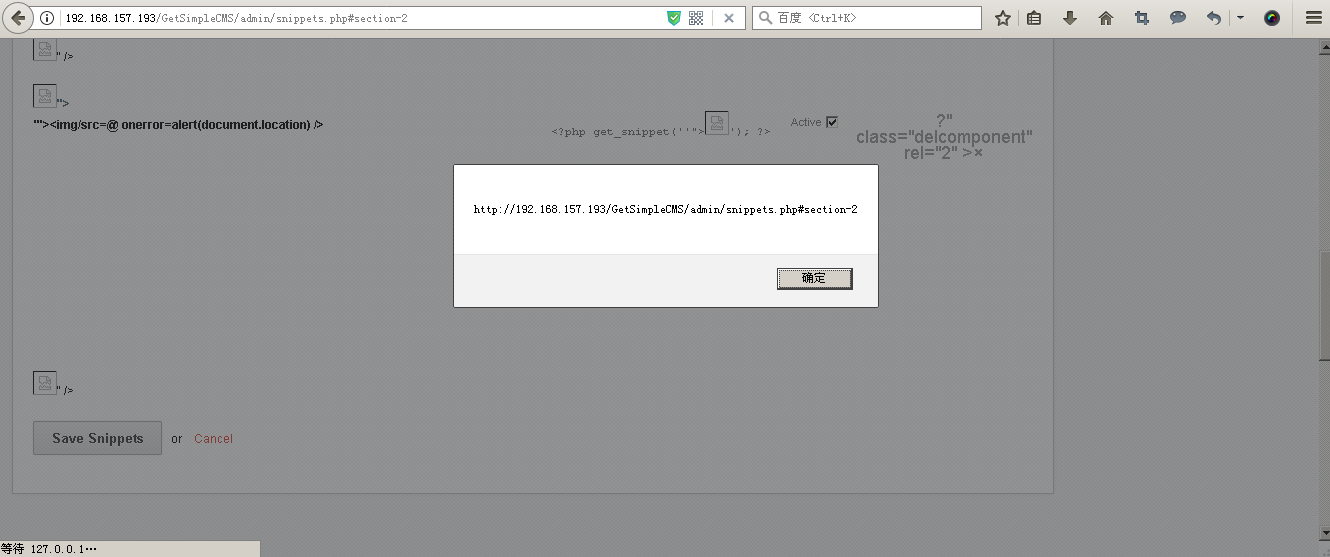
Version 1.5.x-dev CSRF vulnerability in employee management Before CSRF  Click 'Add' and edit employee information  Grab the packet and construct the payload of CSRF, and save it as...
图片问题

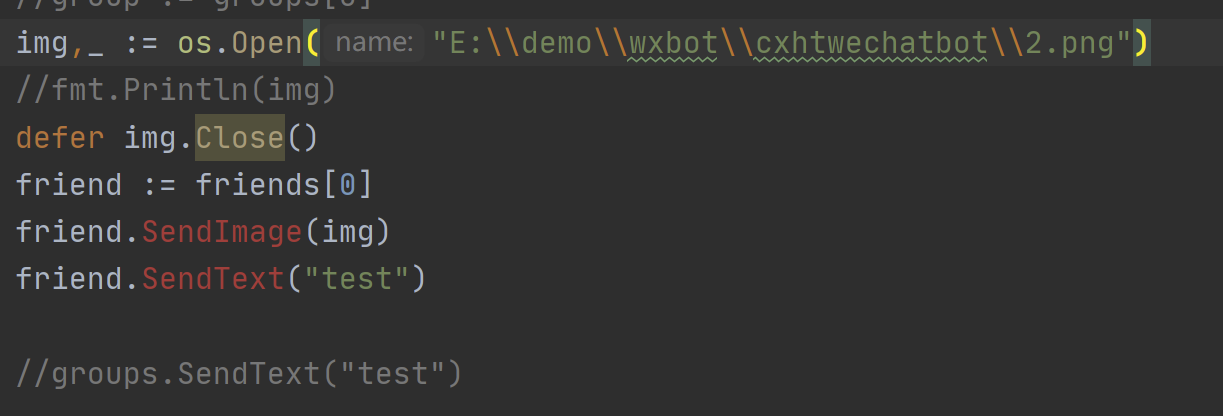 没有报错,但图片就是发不出去
图片问题

无法发生图片
 打印报错直接显示upload failed 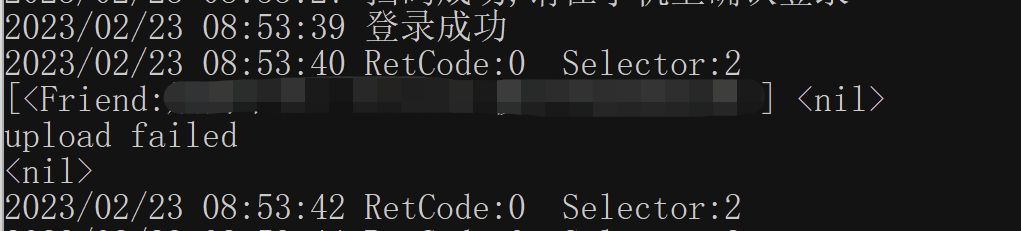
Confirms: [None, None, None, None] Confirms: [None, None, None, None] Confirms: [None, None, None, None] Confirms: [None, None, None, None] Transaction did not land help!!!