attack_range
 attack_range copied to clipboard
attack_range copied to clipboard
A tool that allows you to create vulnerable instrumented local or cloud environments to simulate attacks against and collect the data into Splunk
Bumps [oauthlib](https://github.com/oauthlib/oauthlib) from 3.2.0 to 3.2.1. Release notes Sourced from oauthlib's releases. 3.2.1 In short OAuth2.0 Provider: #803 : Metadata endpoint support of non-HTTPS CVE-2022-36087 OAuth1.0: #818 : Allow IPv6...
When trying to run a simulation on a stopped AR, it would be nice to provide a more user-friendly message. 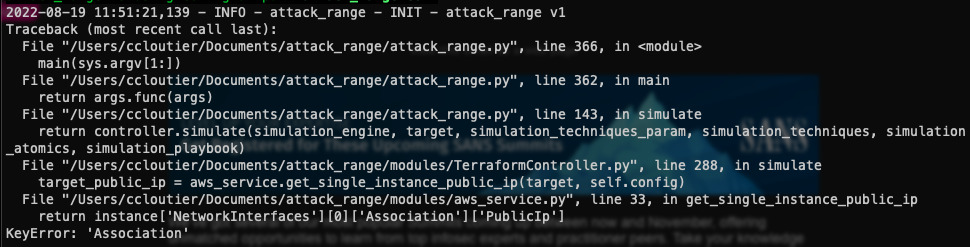 Also, cosmetic only, but the messages about the AR...
We should look into deploying [TA-aurora](https://github.com/NextronSystems/TA-aurora) as part of Attack Range when the Aurora EDR agent is configured (`install_aurora_agent = 1`). Deploying it after the fact manually is not as...
tiny thing were the cli args are not considered for replay
Trying to run build but erroring out with error: What is the path, as the .deb is installed under attack_range directory and present. The Vagrant executable cannot be found. Please...
I had three issues with Phantom when installing locally. This ticket tracks the issues and some solutions I had, and is more for reference purposes than a request for help:...
Hey there When I try to stop the local attack range with `python attack_range.py stop`, the following error occurs: Traceback (most recent call last): File "/home/....../git_tools/attack_range/attack_range.py", line 235, in main(sys.argv[1:])...
When i try to install the Carbon Black Cloud Sensor, the following error occurs: [nlGIPlpZdTh5oTssCWn](fatal: [ar-win-attack-range-key-pair-ar-0]: FAILED! => {"changed": true, "checksum": "150b873cd32aa24516fd36c2dee72075b24a0331", "dest": "C:\\Temp\\WindowsSensor.msi", "msg": "failed to copy file /home/....../git_tools/attack_range/apps/installer_vista_win7_win8-64-4.0.0.1292.msi:...
I am getting an error everytime I try running the default Purplesharp playbook. I have currently configured the range in a local installation The command I am running is as...
This blog post https://www.splunk.com/en_us/blog/security/attack-range-v3-0.html talks about using vmware fusion (and I would assume vmware workstation as well), but I do not see anywhere on how to do that. Anyone know...
