ViCrack
ViCrack
Like this: [https://stackoverflow.com/a/19536667](https://stackoverflow.com/a/19536667) [https://stackoverflow.com/a/21138900](https://stackoverflow.com/a/21138900) Can automatically convert bool argument in fabric
发现有时候更新的话 , 数据库结构可能不兼容 , 看文档里面是说要删掉数据库文件重新生成才行 , 我想数据库这部分是否可以搞一个版本化管理的 , 每次升级不兼容的版本能够进行增量更新 , 而不是得手工删掉重来 好像python这边有个SQLAlchemy Alembic等工具可用于数据库迁移 , 不知道有没有比较好的方式处理 
Sort numbers (and files size) Modify potentially duplicate file name (DELIMITER) 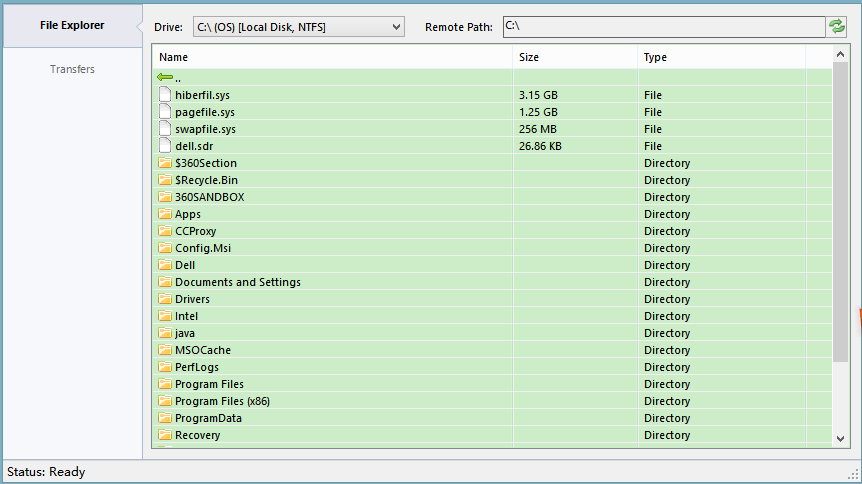  #618
我在这个地方本来是要点击编辑的,不小心点到了删除,脚本没了... 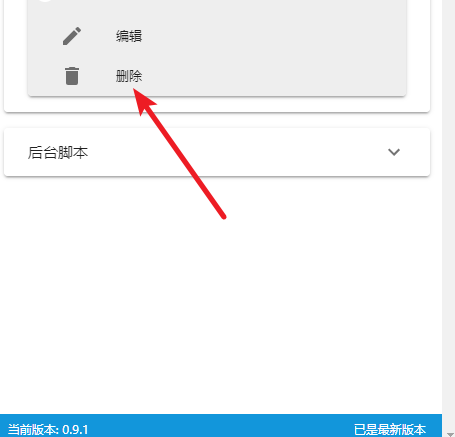
> eclipse.buildId=4.14.0.I20191210-0610 > java.version=1.8.0_202 > java.vendor=Oracle Corporation > BootLoader constants: OS=win32, ARCH=x86_64, WS=win32, NL=zh_CN > Framework arguments: -product org.eclipse.epp.package.jee.product > Command-line arguments: -os win32 -ws win32 -arch x86_64 -product org.eclipse.epp.package.jee.product...
Closes #9328 config location: $env:AppData/Antares - [x] I have read the [Contributing Guide](https://github.com/ScoopInstaller/.github/blob/main/.github/CONTRIBUTING.md).
Closes #9277 config location: $env:LocalAppData/nvim-data - [x] I have read the [Contributing Guide](https://github.com/ScoopInstaller/.github/blob/main/.github/CONTRIBUTING.md).
Closes #[7158 ](https://github.com/ScoopInstaller/Extras/issues/7158) - [x] I have read the [Contributing Guide](https://github.com/ScoopInstaller/.github/blob/main/.github/CONTRIBUTING.md). > the sourceforge package is still 0.9.11 out of date
### Template / PR Information Update xstream template - Fixed CVE-2013-7285 / Updated CVE-2020-26217 / Updated CVE-2021-21345 / Updated CVE-2021-39144 - References: ### Template Validation I've validated this template locally?...
POC优化请求

1、调整危害级别 没看到poc文件中哪里能设置危害级别,poc-yaml-dedecms-cve-2018-6910这个poc比较鸡肋好像现在是高危级别,应该降低为低危 还有几个看起来是弱的 poc-yaml-yonyou-nc-service-info-leak(现在是critical,但实际上只能列下接口信息?) poc-yaml-exchange-cve-2021-26855-ssrf(poc-yaml-microsoft-exchange-ssrf-cve-2021-26885) poc-yaml-yonyou-nc-uapws-db-info-leak poc-yaml-zoho-cve-2022-23779-info-leak poc-yaml-thinkphp-cve-2022-25481-info-leak (现在是高危,一个信息泄漏不至于是高危吧) poc-yaml-go-pprof-leak ***-info-leak 的应该还有其他类似的 2、容易有误报 poc-yaml-thinkphp5023-method-rce `_method=__construct&filter[]=printf&method=GET&server[REQUEST_METHOD]=xxxxxxxx` 直接查找print的字符串,如果目标地址报错的时候会把参数打印出来,或者它正好是一个phpinfo页面,就会误报 poc-yaml-php-cgi-cve-2012-1823-rce 加法数字过短,需要在 800000000 和 1000000000 之间   