Johnny Wang
Johnny Wang
maybe this PR would help: https://github.com/openresty/lua-nginx-module/pull/1861
Hi @kiss291323003, the PR #1861 is already merged.
According to [rfc 7578 section 4.1](https://datatracker.ietf.org/doc/html/rfc7578#section-4.1), the boundary must: > constructed using CRLF, "--", and the value of the "boundary" parameter It looks like it is not meeting the standard
@suikabreaker could you modify the code style by referring to another PR (#63) and rebase the latest master
I found there may be an overflow in python, and my `payload.bin` file is more than 4GB
Hi @chilicrepe, It will most likely be included in the next release: since openresty every release will follow the current mainline of nginx
Hi @thibaultcha, May I ask if we need to keep this PR or close it?
> > > 2022-7-29 17:00 据说nginx > > > > > 先明确下 这个漏洞到底是怎么引起的 在看下 是不是 nginx 的问题,这个 漏洞的编号 可以提供下 > > 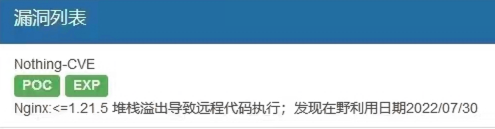 Is there a link for this RCE vulnerability?...
Thanks for the report, we can send a minor update if necessary
Hi @samhaque, We have made preparations for the release of the version, it should be released within the next week