Error occurs when loading API Policies view for Read-Only user
Description
Following error appears when logged in to the publisher portal as a read only (internal/observer) user and click on the 'Policies' on left menu.
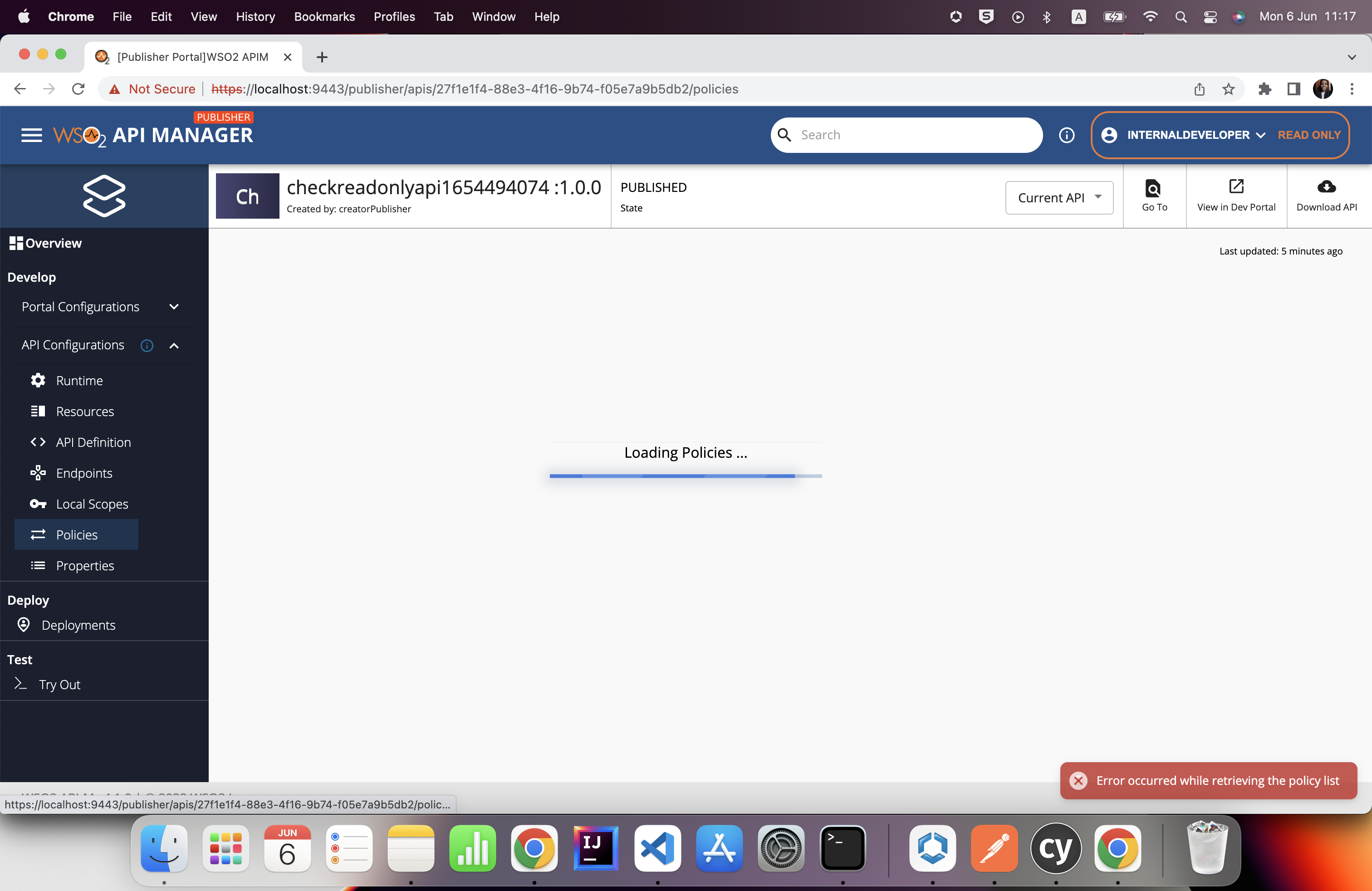
Steps to Reproduce
- Sign in to the WSO2 Management Console (https://<APIM_host>:<APIM_port>/carbon) as the admin
- Create a REST API
- Create a user and assign the observer default role.
- Login to the Publisher portal as the newly created observer user
- Select the previously created API -> Policies
Affected Component
APIM
Version
4.1.0
Environment Details (with versions)
Mac Book Pro M1 chip OS version 12.4
Relevant Log Output
No response
Related Issues
No response
Suggested Labels
react
Investigated the API responses at the login phase. Readonly user has assigned the following scopes:
"scope" : "apim:api_view apim:publisher_settings openid"
For the Admin, there was "common_operation_policy_view" as a scope and Read Only user had not. When Manually added that particular scope for the Internal/Observer role (the corresponding role for read-only user), this issue could be solved.
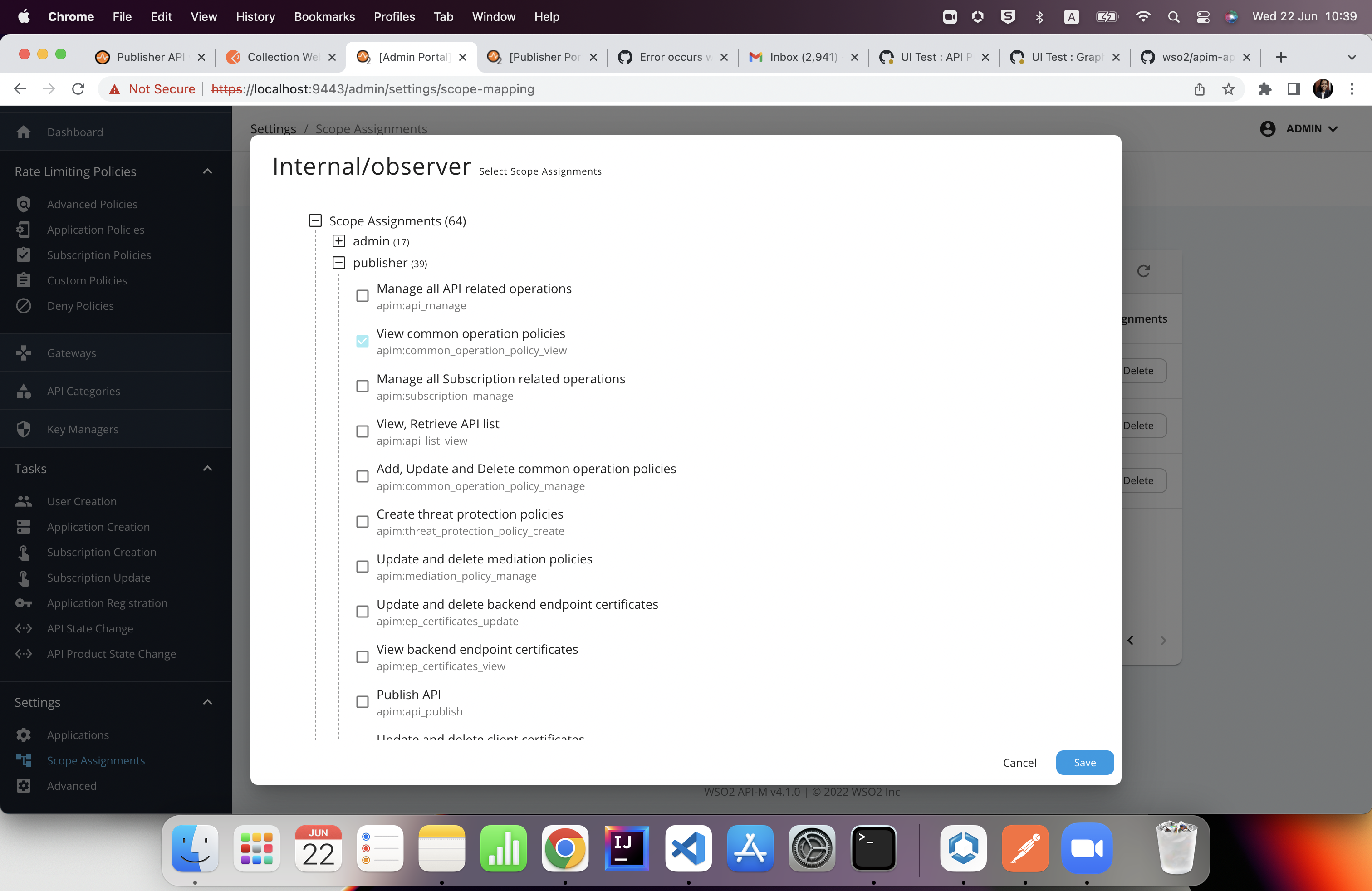
Seems this policy view scope is not included within api_view scope.
Fixed in WSO2 API Manager 4.6.0
This issue has been fixed in WSO2 API Manager 4.6.0. Observer role users can now successfully access the Policies section in Publisher portal without errors.
Issue Summary
In APIM 4.1.0, when a read-only user (Internal/observer role) logged into the Publisher portal and attempted to access the Policies section, an error occurred preventing the view from loading.
Root Cause: The Internal/observer role lacked the required "common_operation_policy_view" scope. This scope was not included within the api_view scope, creating a permission gap that prevented observers from viewing policies.
Fix Details
Fix: PR #11297 in carbon-apimgt, PR #281 in apim-apps
What Changed:
The Internal/observer role was granted the following policy-related scopes:
{
"Name": "apim:common_operation_policy_view",
"Roles": "admin,Internal/creator,Internal/publisher,Internal/observer"
}
{
"Name": "apim:gateway_policy_view",
"Roles": "admin,Internal/creator,Internal/publisher,Internal/observer"
}
File: tenant-conf.json
-
Line 341-342: Added
Internal/observertoapim:common_operation_policy_view -
Line 369-370: Added
Internal/observertoapim:gateway_policy_view
Testing
Test Method: Configuration verification + REST API endpoint testing
Configuration Check:
1. apim:common_operation_policy_view
Roles: admin,Internal/creator,Internal/publisher,Internal/observer
✓ Internal/observer HAS access
2. apim:gateway_policy_view
Roles: admin,Internal/creator,Internal/publisher,Internal/observer
✓ Internal/observer HAS access
Endpoint Test:
URL: /api/am/publisher/v4/operation-policies
Scopes: apim:api_view apim:common_operation_policy_view
Status Code: 200 ✓
Policies found: 50
Result: ✅ FIXED
Observer role users can successfully access policy endpoints with the appropriate scopes. The operation policies endpoint returned HTTP 200 with policy data.
Verification
The fix ensures that:
- ✅ Internal/observer role has
apim:common_operation_policy_viewscope - ✅ Internal/observer role has
apim:gateway_policy_viewscope - ✅ Observer users can view operation policies without errors
- ✅ Observer users can view gateway policies without errors
- ✅ Policies section loads properly in Publisher portal for read-only users
Conclusion
The issue with observer role users being unable to access the Policies section has been fixed. The required scopes have been properly configured in the tenant configuration, allowing read-only users to view policies without encountering permission errors.
For Observer Role Users:
- Can now view API policies in Publisher portal
- Can access operation policies endpoint
- Can access gateway policies endpoint
- All policy-related views work correctly with read-only permissions
Tested on: WSO2 API Manager 4.6.0 Status: ✅ Fixed Fix: PR #11297 (carbon-apimgt), PR #281 (apim-apps) Test Method: Configuration verification + REST API testing