tincho
tincho
Oyente still reports the vulnerability Callstack Depth Attack. 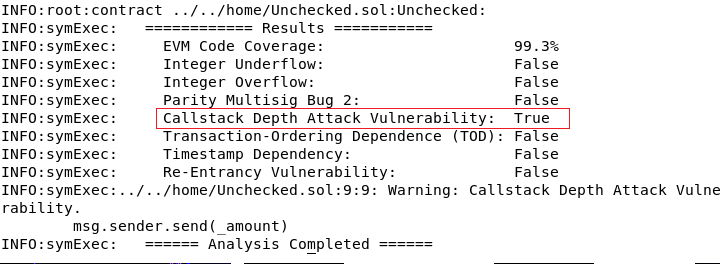 However, according to the following sources, this vulnerability does not longer exist: - https://consensys.github.io/smart-contract-best-practices/known_attacks/#call-depth-attack-deprecated - https://ethereum.stackexchange.com/questions/26105/are-solidity-contracts-still-vulnerable-to-callstack-exploits - https://github.com/ethereum/EIPs/blob/master/EIPS/eip-150.md I believe it...
Hey folks! These days I'm reviewing the `v4.8.0-rc.0` release candidate. I'll drop in this issue my concerns and comments and questions about the [`ERC721Consecutive` contract](https://github.com/OpenZeppelin/openzeppelin-contracts/blob/v4.8.0-rc.0/contracts/token/ERC721/extensions/ERC721Consecutive.sol) and the related functions in...
Hey folks, while reviewing the `Oracles` contract I started digging into the data signed by oracles and how it's being verified. Overall, my main concern was to understand the extent...
Hey there. I wanted to raise a potential oversight in the way the deposits queue is implemented in the `_stake` function of the `Pool` contract. I'm aware that nowadays this...
`approve` should not check for balances. See: https://github.com/sec-bit/awesome-buggy-erc20-tokens/blob/master/ERC20_token_issue_list.md#a19-approve-with-balance-verify
In the library `Allowance`, neither `updateAll` nor `updateAmountAndExpiration` check that the `expiration` passed is not in the past. That means it's possible to set an approval expiration timestamp that ends...
I was just checking the newish `OffchainDNSResolver` contract, and there seems to be an unhandled failure in the `OffchainDNSResolver` when a user includes an invalid resolver address as part of...
Hey folks, I think there's a case of an unhandled exception that might lead to unexpectedly halting the oracle service. It doesn't look worrisome, so I'm reporting it publicly here...
