Windows-Optimize-Harden-Debloat
 Windows-Optimize-Harden-Debloat copied to clipboard
Windows-Optimize-Harden-Debloat copied to clipboard
Enhance the security and privacy of your Windows 10 and Windows 11 deployments with our fully optimized, hardened, and debloated script. Adhere to industry best practices and Department of Defense STI...
Optimize, Harden, and Debloat Windows 10 and Windows 11 Deployments
Warning: This script should work for most, if not all, systems without issue. While @SimeonOnSecurity creates, reviews, and tests each repo intensively, we can not test every possible configuration nor does @SimeonOnSecurity take any responsibility for breaking your system. If something goes wrong, be prepared to submit an issue. Do not run this script if you don't understand what it does. It is your responsibility to review and test the script before running it.
Introduction:
Windows 10 and Windows 11 are invasive and insecure operating system out of the box. Organizations like PrivacyTools.io, Microsoft, Cyber.mil, the Department of Defense, and the National Security Agency have recommended configuration changes to lockdown, harden, and secure the operating system. These changes cover a wide range of mitigations including blocking telemetry, macros, removing bloatware, and preventing many digital and physical attacks on a system. This script aims to automate the configurations recommended by those organizations.
Notes:
- This script is designed for operation in primarily Personal Use environments. With that in mind, certain enterprise configuration settings are not implemented. This script is not designed to bring a system to 100% compliance. Rather it should be used as a stepping stone to complete most, if not all, the configuration changes that can be scripted while skipping past issues like branding and banners where those should not be implemented even in a hardened personal use environment.
- This script is designed in such a way that the optimizations, unlike some other scripts, will not break core windows functionality.
- Features like Windows Update, Windows Defender, the Windows Store, and Cortona have been restricted, but are not in a dysfunctional state like most other Windows 10 Privacy scripts.
- If you seek a minimized script targeted only to commercial environments, please see this GitHub Repository
Requirements:
- [x] Windows 10/1 Enterprise (Preferred) or Windows 10 Professional
- Windows 10/11 Home does not support GPO configurations.
- Window "N" Editions are not tested.
- [x] Standards for a highly secure Windows 10 device
- [x] System is fully up to date and supported
- Run the Windows Upgrade Assistant to update and verify latest major release.
- [x] Bitlocker must be suspended or turned off prior to implementing this script, it can be enabled again after rebooting.
- Follow-up runs of this script can be run without disabling bitlocker.
- [x] Hardware Requirements
Recommended reading material:
- System Guard Secure Launch
- System Guard Root of Trust
- Hardware-based Isolation
- Memory integrity
- Windows Defender Application Guard
- Windows Defender Credential Guard
Additions, notable changes, and bugfixes:
This script adds, removes, and changes settings on your system. Please review the script before running it.
Browsers:
- Browsers will have additional extentions installed to aid in privacy and security.
- See here for additional information.
- Due to the DoD STIGs implemented for browsers, extension management and other enterprise settings are set. For instructions on how to see these options, you'll need to look at the GPO instructions below.
Powershell Modules:
- To aid in automating Windows Updates the PowerShell PSWindowsUpdate module will be added to your system.
Fixing Microsoft Account, Store, or Xbox Services:
This is because we block signing into microsoft accounts. Microsoft's telemetry and identity association is frowned upon. However, if you still wish to use these services see the following issue tickets for the resolution:
- https://github.com/simeononsecurity/Windows-Optimize-Debloat/issues/1
- https://github.com/simeononsecurity/Windows-Optimize-Harden-Debloat/issues/16
- https://github.com/simeononsecurity/Windows-Optimize-Harden-Debloat/issues/22
Editing policies in Local Group Policy after the fact:
If you need to modify or change a setting, they are most likely configurable via GPO:
-
Import the ADMX Policy definitions from this repo into C:\windows\PolicyDefinitions on the system you're trying to modify.
-
Open
gpedit.mscon on the system you're trying to modify.
A list of scripts and tools this collection utilizes:
First Party:
- .NET-STIG-Script
- Automate-Sysmon
- FireFox-STIG-Script
- JAVA-STIG-Script
- Standalone-Windows-STIG-Script
- Windows-Defender-STIG-Script
- Windows-Optimize-Debloat
Third Party:
- Cyber.mil - Group Policy Objects
- Microsoft Security Compliance Toolkit 1.0
- Microsoft Sysinternals - Sysmon
STIGS/SRGs Applied:
- Adobe Acrobat Pro DC Continuous V2R1
- Adobe Acrobat Reader DC Continuous V2R1
- Firefox V5R2
- Google Chrome V2R4
- Internet Explorer 11 V1R19
- Microsoft Edge V1R2
- Microsoft .Net Framework 4 V1R9
- Microsoft Office 2013 V2R1
- Microsoft Office 2016 V2R1
- Microsoft Office 2019/Office 365 Pro Plus V2R3
- Microsoft OneDrive STIG V2R1
- Oracle JRE 8 V1R5
- Windows 10 V2R2
- Windows Defender Antivirus V2R2
- Windows Firewall V1R7
Additional configurations were considered from:
- BuiltByBel - PrivateZilla
- CERT - IE Scripting Engine Memory Corruption
- Dirteam - SSL Hardening
- MelodysTweaks - Basic Tweaks
- Microsoft - Managing Windows 10 Telemetry and Callbacks
- Microsoft - Reduce attack surfaces with attack surface reduction rules
- Microsoft - Recommended block rules
- Microsoft - Recommended driver block rules
- Microsoft - Specture and Meltdown Mitigations
- Microsoft - Windows 10 Privacy
- Microsoft - Windows 10 VDI Recomendations
- Microsoft - Windows Defender Application Control
- Mirinsoft - SharpApp
- Mirinsoft - debotnet
- NSACyber - Application Whitelisting Using Microsoft AppLocker
- NSACyber - Bitlocker Guidance
- NSACyber - Hardware-and-Firmware-Security-Guidance
- NSACyber - Windows Secure Host Baseline
- UnderGroundWires - Privacy.S**Y
- Sycnex - Windows10Debloater
- The-Virtual-Desktop-Team - Virtual-Desktop-Optimization-Tool
- TheVDIGuys - Windows 10 VDI Optimize
- VectorBCO - windows-path-enumerate
- W4H4WK - Debloat Windows 10
- Whonix - Disable TCP Timestamps
How to run the script:
Manual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the GitHub Repository
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
Get-ChildItem -Recurse *.ps1 | Unblock-File
powershell.exe -ExecutionPolicy ByPass -File ./sos-optimize-windows.ps1
Automated Install:
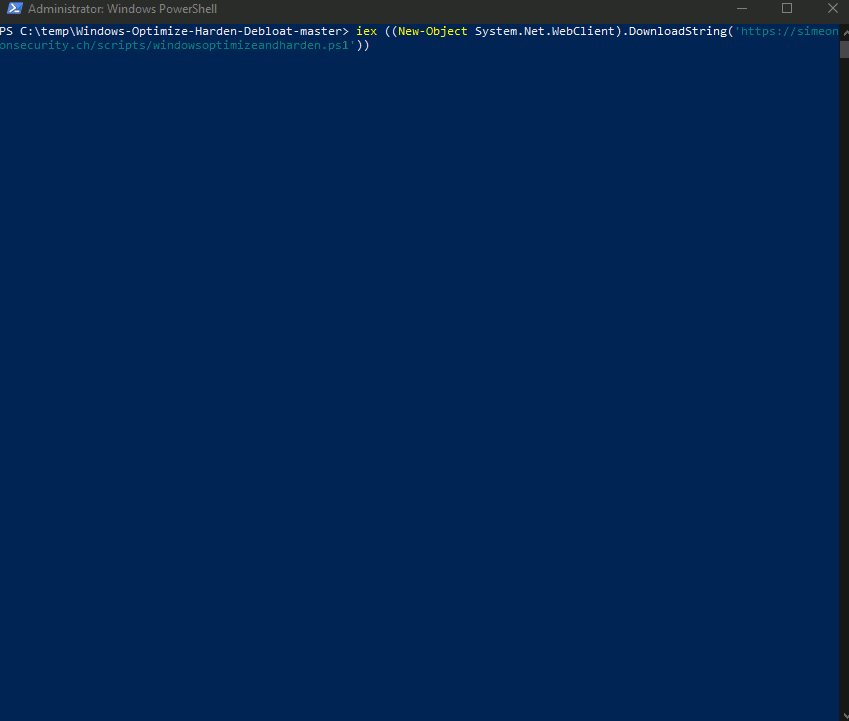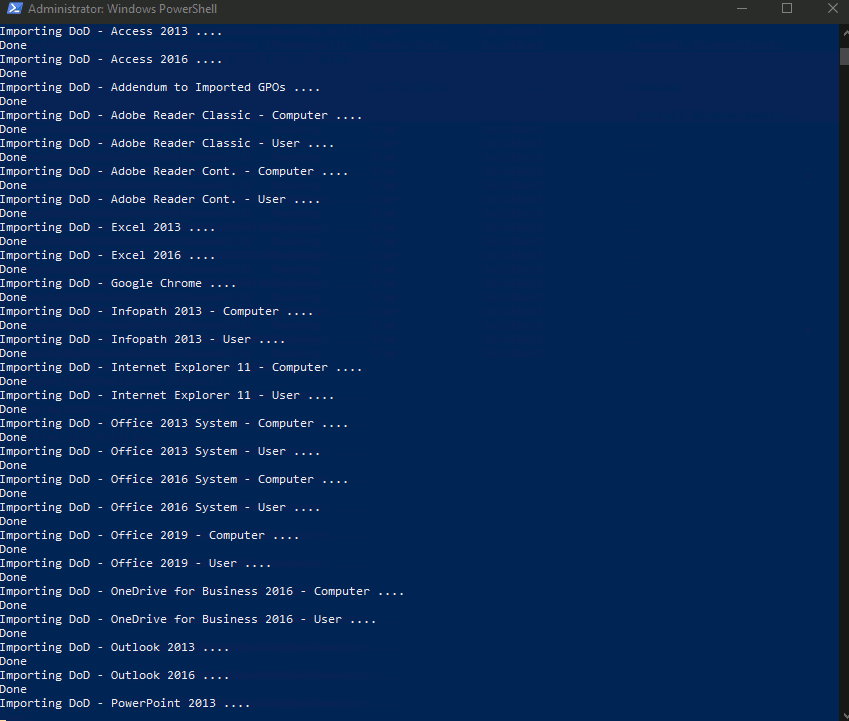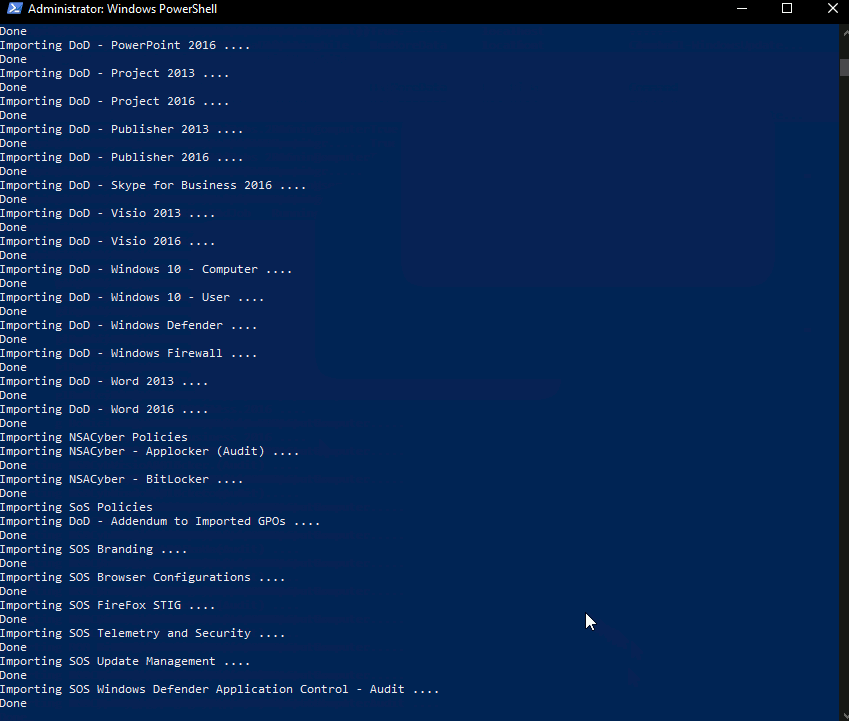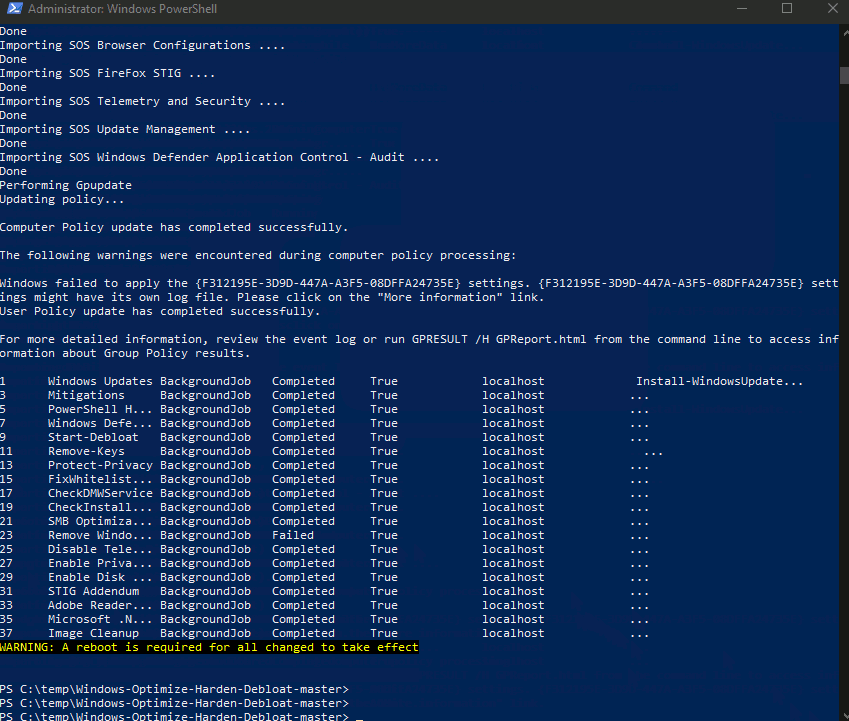
Use this one-liner to automatically download, unzip all supporting files, and run the latest version of the script.
iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iex