grails-console
 grails-console copied to clipboard
grails-console copied to clipboard
A web-based Groovy console for interactive runtime application management and debugging
Summary
A web-based Groovy console for interactive runtime application management and debugging
Installation
The 1.X version is for Grails 2.
The 2.0.X version is for Grails 3.0 - 3.2.
The 2.1.X version is for Grails 3.3+.
Grails 2
Add a dependency in BuildConfig.groovy:
grails.project.dependency.resolution = {
// ...
plugins {
runtime ':console:1.5.12'
// ...
}
}
Grails 3+
Note: If using Grails 3.0.4, you need to update the asset-pipeline dependency in build.gradle to 3.0.6 or greater. 3.0.5 is used by default and has a bug that prevents the console page from rendering.
Note: If using Grails 3.0.12, you will need to add this to your configuration: grails.resources.pattern = '/**'. There is a bug related to resource paths.
Add a dependency in build.gradle
runtime 'org.grails.plugins:grails-console:2.1.1'
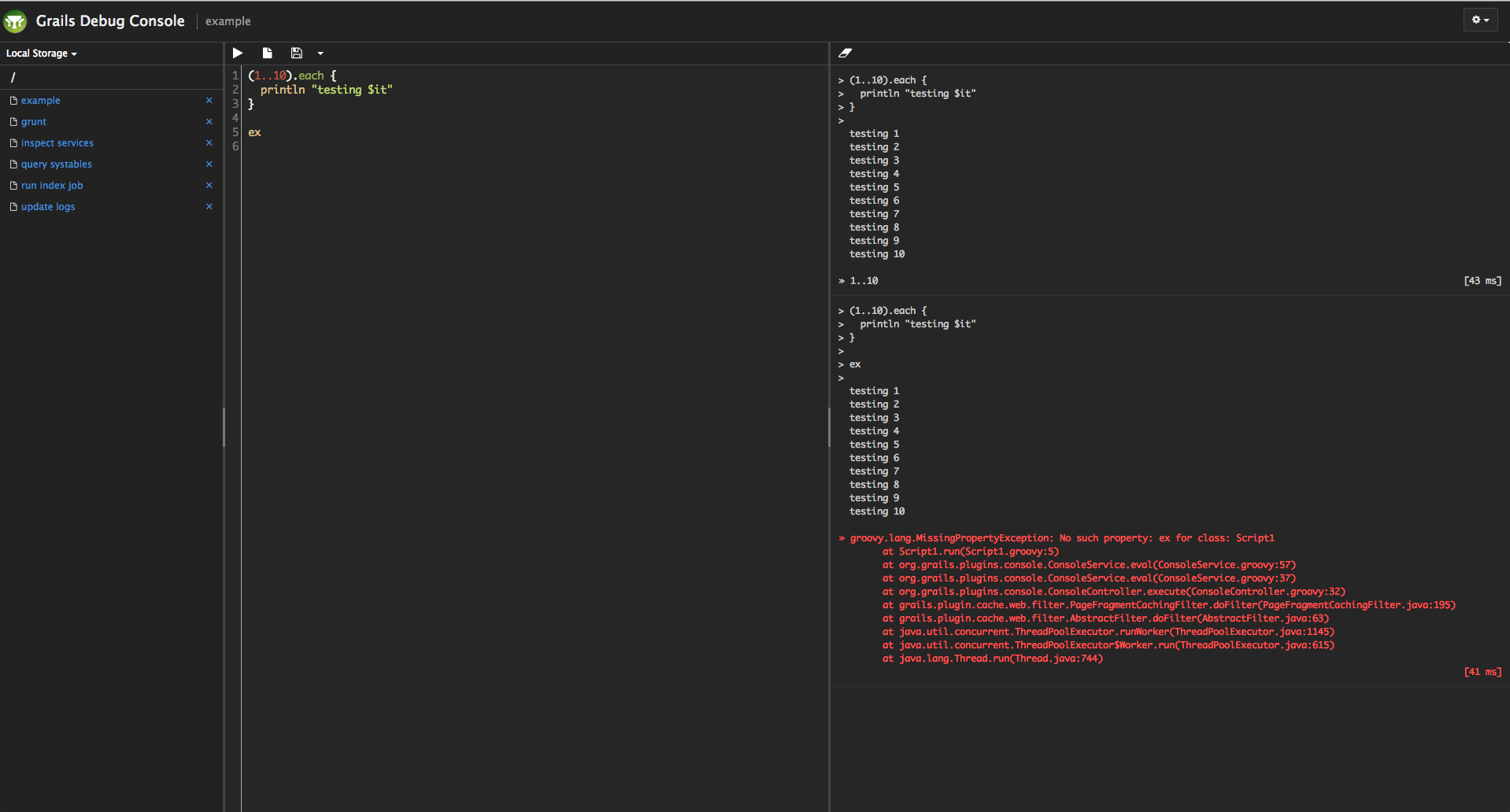
Usage
Use a browser to navigate to the /console page of your running app, e.g. http://localhost:8080/{app-name}/console
Type any Groovy commands in the console text area, then click on the execute button. The console plugin relies on Groovy Shell. Lookup Groovy Shell documentation for more information. The Groovy Shell uses the Grails classloader, so you can access any class or artifact (e.g. domain classes, services, etc.) just like in your application code.
Saving/loading scripts
Click on the Save button to save the current script.
Use the Storage pane to navigate existing files. Click on a file to load it into the editor.
There are currently two storage options available:
Local Storage
Local Storage uses HTML5 Web Storage. The files are serialized and stored in the browser as a map under the key gconsole.files.
Remote Storage
Remote Storage uses the filesystem of the server on which the application is running.
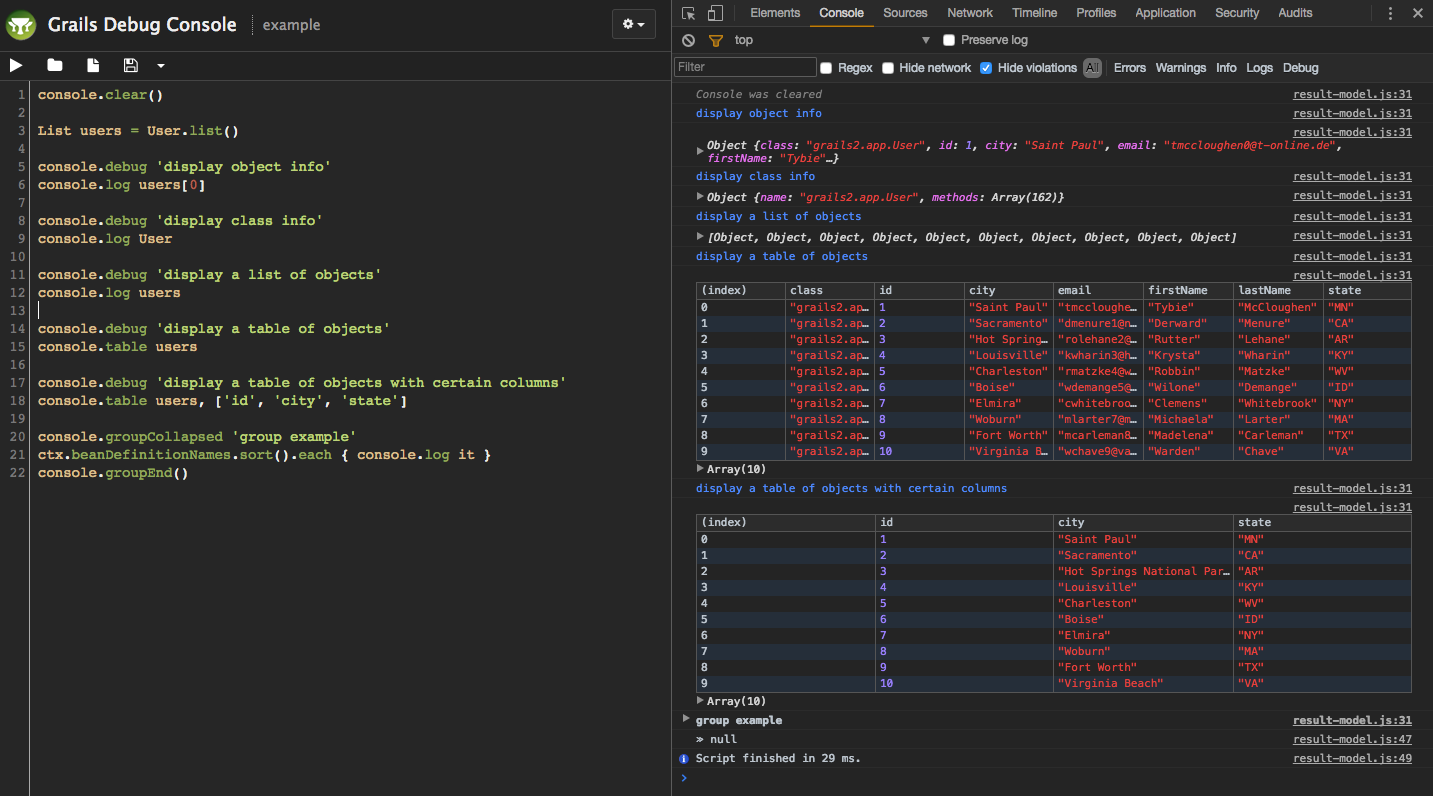
Writing to the browser console
Calls made to the implicit console variable will be executed on the browser's console.
The arguments are serialized as JSON and the calls are queued to run after the script completes.
Example:
Implicit variables
The following implicit variables are available:
-
ctx- the Spring ApplicationContext -
grailsApplication- the GrailsApplication instance -
config- the Grails configuration -
request- the current HTTP request -
session- the current HTTP session -
out- the output PrintStream
See Script Examples for example usage.
Keyboard Shortcuts
| Key | Command |
|---|---|
| Ctrl-Enter / ⌘-Enter | Execute |
| Ctrl-S / ⌘-S | Save |
| Esc | Clear output |
Configuration
The following configuration options are available:
| Property | Description |
|---|---|
grails.plugin.console.enabled |
Whether to enable the plugin. Default is true for the development environment, false otherwise. |
grails.plugin.console.baseUrl |
Base URL for the console controller. Can be a String or a List of Strings if having multiple URLs is desired. Default uses createLink(). |
grails.plugin.console.fileStore.remote.enabled |
Whether to include the remote file store functionality. Default is true. |
grails.plugin.console.fileStore.remote.defaultPath |
Default path when browsing remote files. Default is /. |
grails.plugin.console.layout |
Used to override the plugin's GSP layout. |
grails.plugin.console.newFileText |
Text to display as a template for new files. Can be used to add frequently used imports, environment specific warnings, etc... Defaults to empty. |
grails.plugin.console.tabSize |
The width of a tab character. Defaults to 4. |
grails.plugin.console.indentWithTabs |
Whether indents should use tabs rather than spaces. Default is false. |
grails.plugin.console.indentUnit |
How many spaces a block should be indented. Default is 4. |
grails.plugin.console.csrfProtection.enabled |
Whether to enable CSRF protection. Default is true. |
Security
By default (as of v1.5.0) the console plugin is only enabled in the development environment. You can enable or disable it for any environment with
the grails.plugin.console.enabled config option in Config.groovy / application.groovy (Grails 3). If the plugin is enabled in non-development environments, be sure to guard access using a security plugin like Spring Security Core or Shiro. For Grails 2.x, the paths /console/** and /plugins/console*/** should be secured. For Grails 3.x, the paths /console/** and /static/console/** should be secured.
Spring Security Core example:
grails.plugin.springsecurity.controllerAnnotations.staticRules = [
[pattern:"/console/**", access:['ROLE_ADMIN']],
[pattern:"/plugins/console*/**", access:['ROLE_ADMIN']], // Grails 2.x
[pattern:"/static/console/**", access:['ROLE_ADMIN']], // Grails 3.x
]
Another example restricting access to localhost IPs:
grails.plugin.springsecurity.controllerAnnotations.staticRules = [
[pattern:"/console/**", access:["hasRole('ROLE_ADMIN') && (hasIpAddress('127.0.0.1') || hasIpAddress('::1'))"]],
[pattern:"/plugins/console*/**", access:["hasRole('ROLE_ADMIN') && (hasIpAddress('127.0.0.1') || hasIpAddress('::1'))"]], // Grails 2.x
[pattern:"/static/console/**", access:["hasRole('ROLE_ADMIN') && (hasIpAddress('127.0.0.1') || hasIpAddress('::1'))"]], // Grails 3.x
]
Authors
Development
Please see CONTRIBUTING.md