fscan
 fscan copied to clipboard
fscan copied to clipboard
RDP 爆破时崩溃
可能是没有验证3389端口是不是rdp服务就直接上爆破了 也可能是别的原因?比如无NLA的一些win 7, win 2003/XP, 存在360 远程桌面保护, unix:Xrdp??? 0.0?
fscan是最新的, 自己下载源码编译的
cmd: fscan.exe -h 172.18.0.0/16 -debug 30 -np -p 3389 -time 6 -t 256 -o debug_fscan_3389.txt
start vulscan 已完成 0/103 [-] rdp 172.18.18.13:3389 administrator 123456 read tcp 172.18.18.200:23634->172.18.18.13:3389: use of closed network connection panic: runtime error: invalid memory address or nil pointer dereference [signal 0xc0000005 code=0x0 addr=0x10 pc=0xb95aa9]
goroutine 1174868 [running]: github.com/tomatome/grdp/protocol/sec.(*Client).sendClientRandom(0xc000bd84b0) github.com/tomatome/[email protected]/protocol/sec/sec.go:630 +0x1a9 github.com/tomatome/grdp/protocol/sec.(*Client).connect(0xc000bd84b0, 0xc0007eb700, 0x3, 0x4, 0xc001f23fa0, 0x2, 0x2, 0xc0003303ea, 0xc00003ae70, 0x2, ...) github.com/tomatome/[email protected]/protocol/sec/sec.go:463 +0x4f3 reflect.Value.call(0xfd6c60, 0xc000bd6640, 0x13, 0x10db46a, 0x4, 0xc0011defc0, 0x4, 0x4, 0x4, 0x30, ...) reflect/value.go:476 +0x907 reflect.Value.Call(0xfd6c60, 0xc000bd6640, 0x13, 0xc0011defc0, 0x4, 0x4, 0x2, 0x4, 0x0) reflect/value.go:337 +0xc5 github.com/tomatome/grdp/emission.(*Emitter).callListeners.func1(0xc00099fe74, 0xc001630300, 0xfac980, 0x1417e10, 0xc0007eb740, 0x4, 0x4, 0xfd6c60, 0xc000bd6640, 0x13) github.com/tomatome/[email protected]/emission/emitter.go:226 +0x4a9 created by github.com/tomatome/grdp/emission.(*Emitter).callListeners github.com/tomatome/[email protected]/emission/emitter.go:201 +0x118
我更新了一下grdp库的版本,师傅试试看看还有这个bug嘛?
看起来OK了,不过我还有一些问题 以下都用自编译windows版测出的问题
1: 中文等字符乱码问题, 计算机中文名, web标题(在notepad++里面,有些ANSI就乱码, 有些UTF-8就乱码) , __MSBROWSE__左右两侧字符乱码等
2:web 标题获取不当 例如出现 iBMC Login <link href="/bmc/resources/css/cmn.css?resource_id=15341742802018" rel="st 你比如说vmware vcenter 网页源代码里是 fscan结果: title:" + ID_VC_Welcome + " 实际上浏览器获取到为: 欢迎使用 VMware vSphere 而ID_VC_Welcome 是在/zh-CN/welcomeRes.js里定义了
3:CVE-2020-0796 这个检测不好 建议看github.com/chompie1337/SMBGhost_RCE_PoC/blob/master/exploit.py 只用do_rce函数内的find_low_stub(ip, port), find_pml4_selfref(ip, port) find_low_stub成功有50%机会, 在前一次成功的基础上,若find_pml4_selfref成功, 几乎100%存在 剩下的不用了,只用这两个函数当检测又准又稳, 就是可能慢了点,多发点包。
4: 小建议,对win版本探测: github.com/FeigongSec/NTLMINFO github.com/JKme/cube 支持smb2 wmi winrm
5: 结果输出文件参考github.com/i11us0ry/goon 的格式 运行时无所谓,主要是扫描完成后可以稍微整理一下, WebTitle,ms17 010,NetInfo ,ftp,InfoScan 全混在一起挺难受的
好像又不行了...不知道为什么 命令没变 我系统性能肯定没问题的 panic: runtime error: invalid memory address or nil pointer dereference [signal 0xc0000005 code=0x0 addr=0x2 pc=0x51c4c1]
goroutine 1175288 [running]: github.com/tomatome/grdp/protocol/t125.(*MCSClient).recvChannelJoinConfirm(0xc000938c80, {0xc000438673, 0x8, 0x8}) github.com/tomatome/[email protected]/protocol/t125/mcs.go:513 +0x561 reflect.Value.call({0x95f100, 0xc001c629a0, 0x18}, {0xa7aed4, 0x4}, {0xc000933008, 0x1, 0x0}) reflect/value.go:556 +0x845 reflect.Value.Call({0x95f100, 0xc001c629a0, 0xb}, {0xc000933008, 0x1, 0x1}) reflect/value.go:339 +0xc5 github.com/tomatome/grdp/emission.(*Emitter).callListeners.func1({0x95f100, 0xc001c629a0, 0xc00043865a}) github.com/tomatome/[email protected]/emission/emitter.go:226 +0x439 created by github.com/tomatome/grdp/emission.(*Emitter).callListeners github.com/tomatome/[email protected]/emission/emitter.go:201 +0x20f
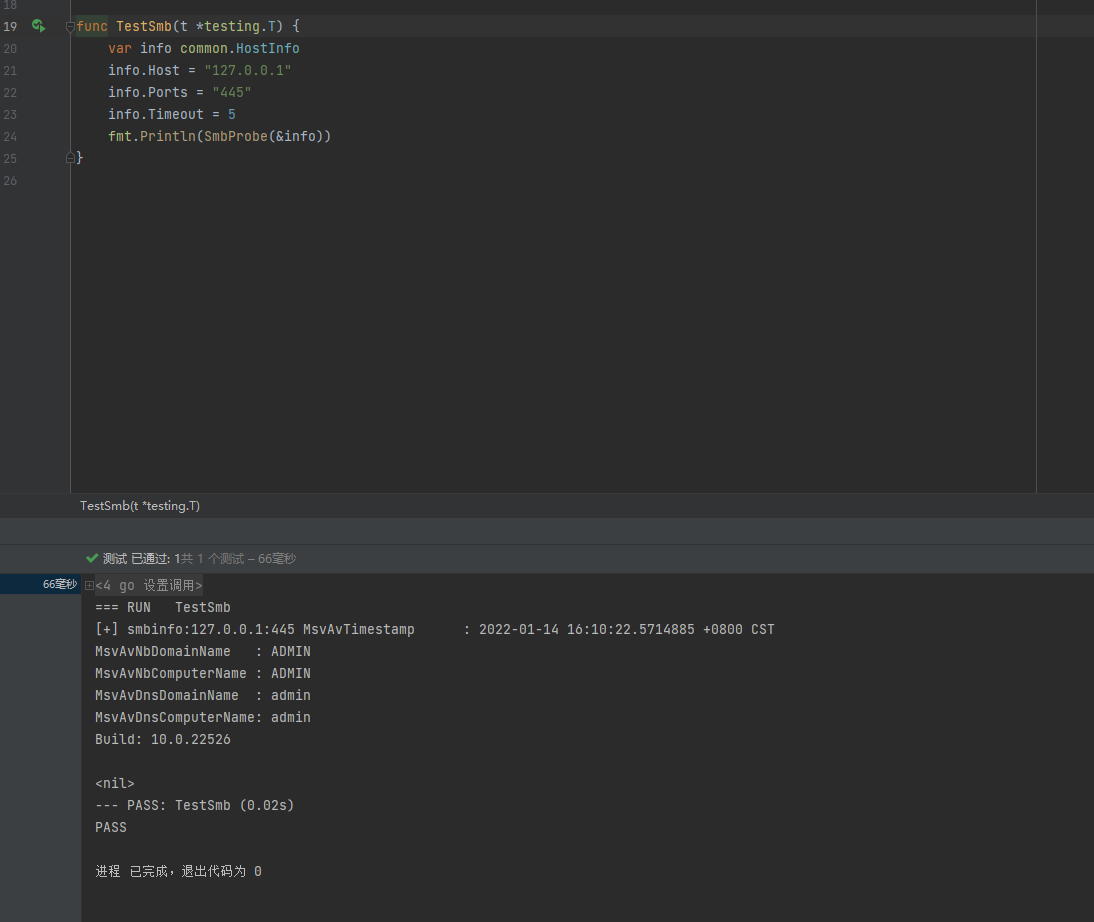
github.com/JKme/cube的smb2和wmi,都是获取机器名?
web 标题获取不当 例如出现 iBMC Login <link href="/bmc/resources/css/cmn.css?resource_id=15341742802018" rel="st 你比如说vmware vcente。 这个只能用浏览器解析去获取,比如github.com/chromedp/chromedp。但不适合于内网
获取Build 版本号