easy-vm
 easy-vm copied to clipboard
easy-vm copied to clipboard
VM can be escaped
This module claims to help "running securely untrusted code" and it looks like the wexond-package-manager uses this module to run its code.
easy-vm mainly uses NodeJS's vm module which has been known to be easily escapable for some time now, to the point where the NodeJS documentation states that "The vm module is not a security mechanism. Do not use it to run untrusted code." (https://nodejs.org/api/vm.html). Due to this, easy-vm and its sandbox can be easily escaped using well-known methods.
To show this vulnerability, I quickly created this gist: https://gist.github.com/vantezzen/1b78d42c8e5698e727f5703a432190b5
Running the script in NodeJS reveals that we have no problems accessing resources outside the sandbox.
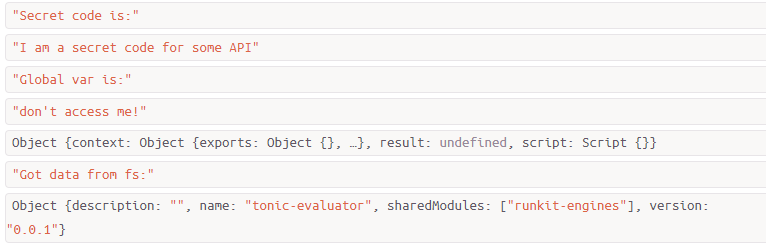
I suggest anyone that actually wants to run untrusted code to switch to modules like vm2 as they seem to have more advanced security mechanisms in place.
I don't use wexond-package-manager, so this package isn't maintained for now. But maybe in the future I will spend more time on this, since I plan to implement wexond-package-manager in wexond. Thank you for your time on discovering the security vulnerability though.