ui
 ui copied to clipboard
ui copied to clipboard
Can enable project network isolation for imported clusters
This PR addresses https://github.com/rancher/dashboard/issues/4574 by adding radio buttons to allow enabling project network isolation for imported clusters.
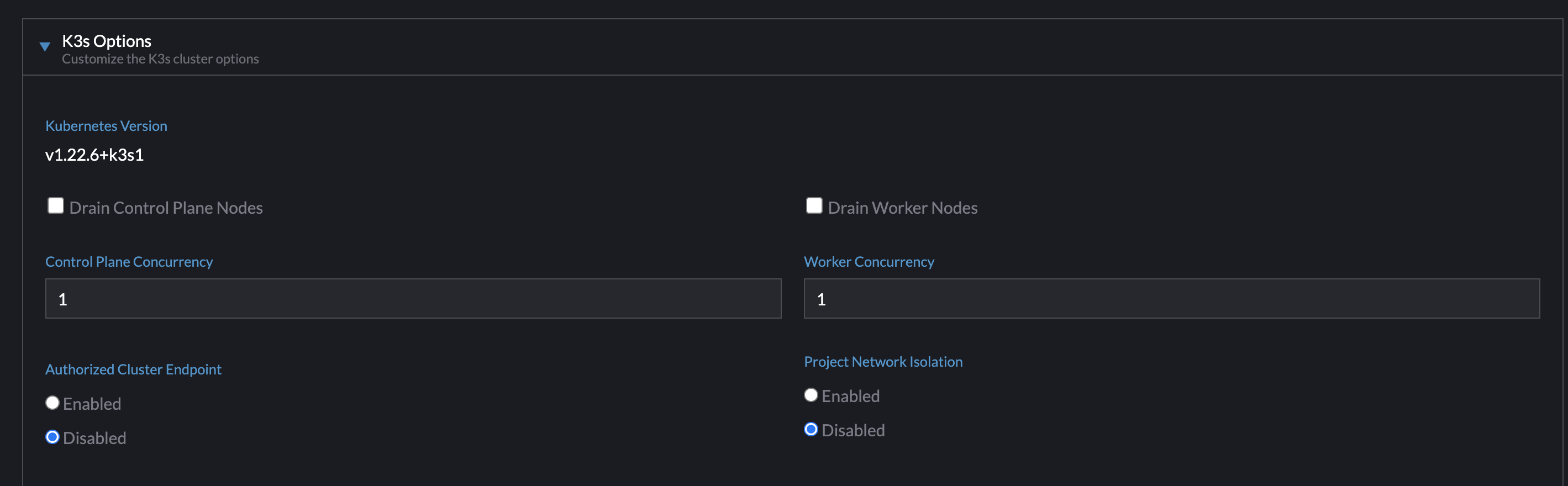
Currently this input is going to always be displayed because for imported clusters, we don't know if the cluster has a CNI that supports project network isolation. (Ryan Sanna to confirm.)
When PNI is enabled, we show the same warning that is used when the option is enabled for RKE1 clusters:
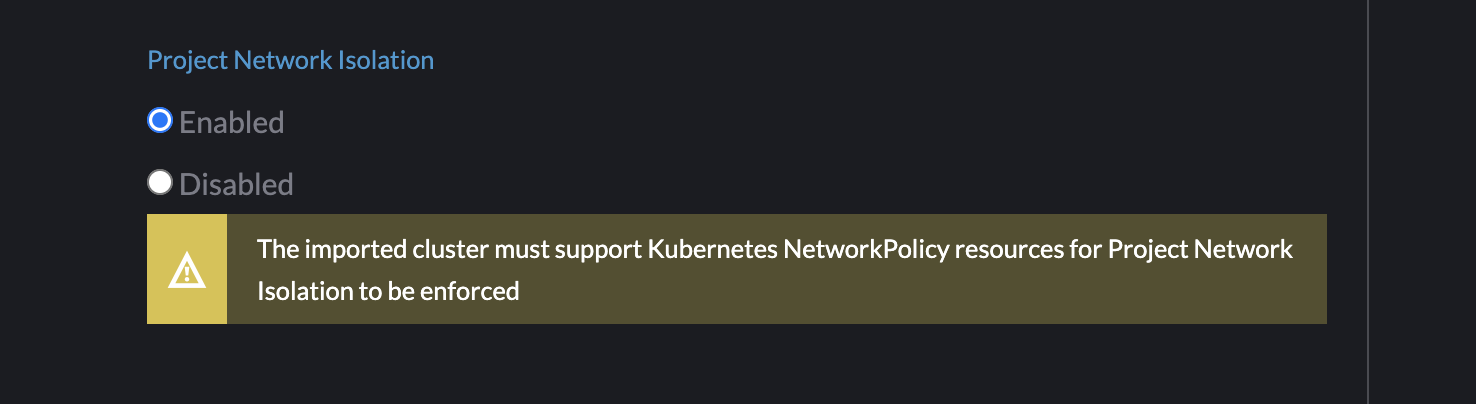
Testing
To test this PR,
- I imported a K3s cluster (I tested the same steps on both K3s and RKE2 clusters)
- In Cluster Management, I went to the imported cluster and clicked Edit Config
- Went to Project Network Isolation and clicked Enabled
- Clicked Save
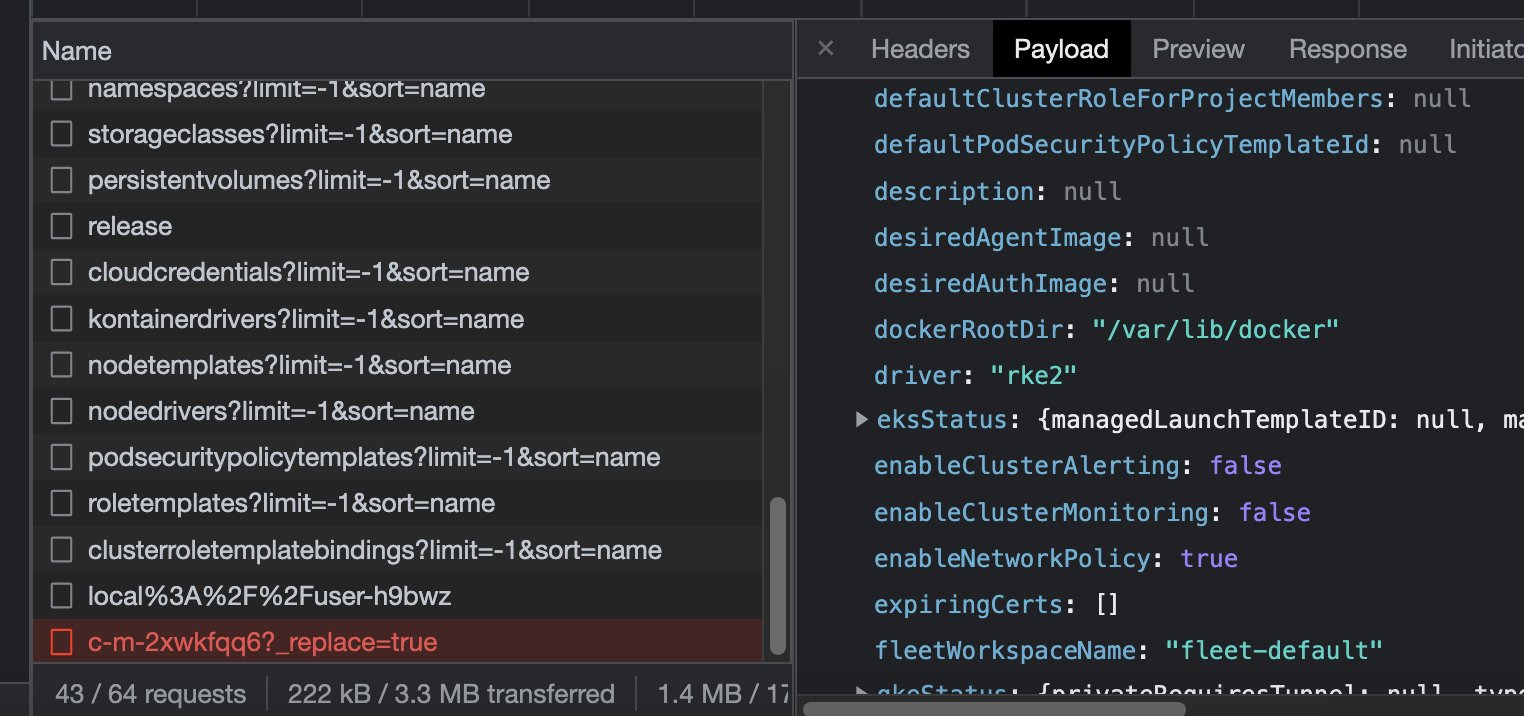
Verified that for both K3s and RKE2, enabledNetworkPolicy was set to true in the cluster data in the network request
Outstanding Questions
Which Kubernetes distro(s) do we want to support? On both K3s and RKE2 clusters, when you save the changes, you get the API error that says it is not a valid option to set enableNetworkPolicy to true:
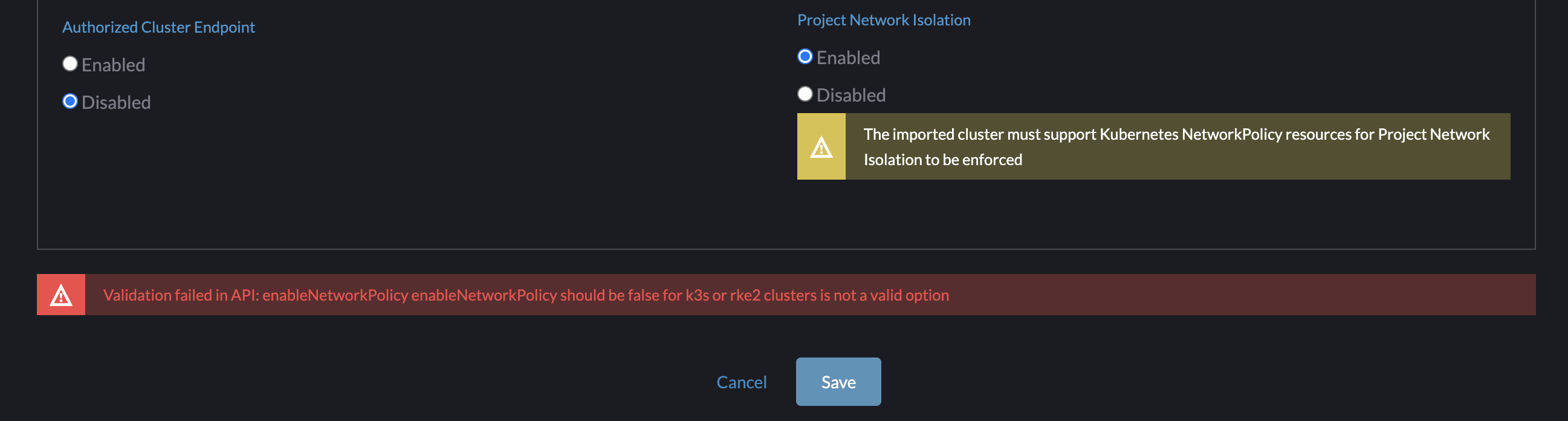
Also, Cody noticed that the form for K3s clusters already exposes an option for enabling PNI under advanced options, even though the API throws the above error if you enable it. Should this option be exposed under Advanced Options for both K3s and RKE2? Currently the form for RKE2 doesn't have an advanced options section.
Here are the existing advanced options for imported K3s clusters:
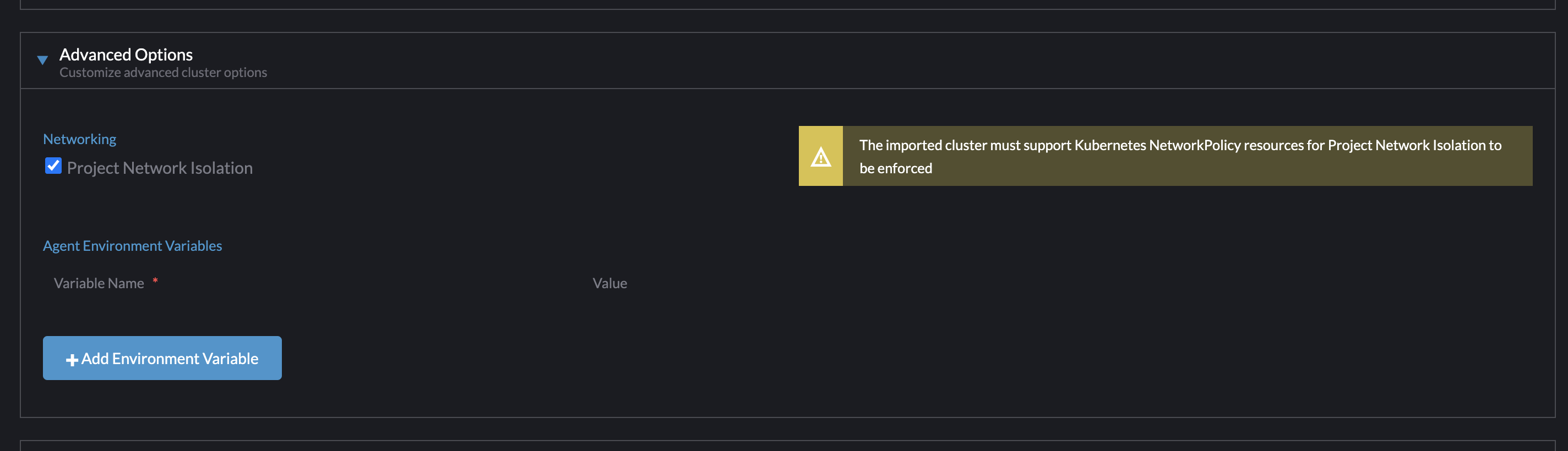
@catherineluse Is this still draft and needed for 2.6.4?
Yes, it's still in draft. I assumed this was one of the RKE2 cluster provisioning features but it's not. Ryan clarified that this change is supposed to affect RKE1, AKS and GKE clusters only, so I'll need to change it to affect those clusters.
Also the K3s has a PNI option but that should actually be removed because the feature is not supported for K3s. I was going to take care of that in the same PR as well.
As to whether the feature is needed for v2.6.4, I would say yes because the backend part is still in the v2.6.4 milestone.
Closing as stale