pulumi-aws
 pulumi-aws copied to clipboard
pulumi-aws copied to clipboard
python typing for `resources` in `GetPolicyDocumentStatementArgs` doesn't support `Output`s
In the following code:
# Policies for sagemaker execution training job
sagemaker_s3_policy_document = aws.iam.get_policy_document(statements=[
aws.iam.GetPolicyDocumentStatementArgs(
sid="1",
actions=[
"s3:*"
],
resources=[
training_bucket.arn.apply(lambda arn: arn),
training_bucket.arn.apply(lambda arn: f"{arn}/*"),
]
)
])
There is a typing warning (in PyCharm) on the resources line:
Expected type 'Optional[Sequence[str]]', got 'list[Union[Output, Output[str]]]' instead
It looks like it should be something like List[Union[str, Awaitable[str], Output[str]] instead
Hmm, that's not what I see in the API docs, so I'm not sure why you're getting that type hint. There are two forms of the getter; you're using the synchronous version, which should not be an Output type.
Could you update this issue with the information of pulumi about so we can see if there might be a problem with the version of the provider that you're using?
Sorry for the delay. Info as requested
poetry run pulumi about
CLI
Version 3.46.0
Go Version go1.19.2
Go Compiler gc
Plugins
NAME VERSION
aws 5.19.0
python unknown
Host
OS debian
Version 11.5
Arch x86_64
This project is written in python: executable='<home>/dist/export/python/virtualenvs/python-default/3.9.2/bin/python3' version='3.9.2
'
Current Stack: <redacted>/dev
TYPE URN
pulumi:pulumi:Stack urn:pulumi:dev::<redacted>-tellme-trainer::pulumi:pulumi:Stack::<redacted>-tellme-trainer-dev
pulumi:providers:aws urn:pulumi:dev::<redacted>-tellme-trainer::pulumi:providers:aws::default
pulumi:providers:aws urn:pulumi:dev::<redacted>-tellme-trainer::pulumi:providers:aws::default_5_16_2
aws:kms/key:Key urn:pulumi:dev::<redacted>-tellme-trainer::aws:kms/key:Key::training-output-bucket-key
aws:kms/key:Key urn:pulumi:dev::<redacted>-tellme-trainer::aws:kms/key:Key::training-input-bucket-key
aws:iam/role:Role urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/role:Role::<redacted>-tellme-sagemaker-execute
aws:s3/bucketV2:BucketV2 urn:pulumi:dev::<redacted>-tellme-trainer::aws:s3/bucketV2:BucketV2::<redacted>-training-input
aws:s3/bucketV2:BucketV2 urn:pulumi:dev::<redacted>-tellme-trainer::aws:s3/bucketV2:BucketV2::<redacted>-training-output
aws:s3/bucketAclV2:BucketAclV2 urn:pulumi:dev::<redacted>-tellme-trainer::aws:s3/bucketAclV2:BucketAclV2::<redacted>--input-acl
aws:s3/bucketServerSideEncryptionConfigurationV2:BucketServerSideEncryptionConfigurationV2 urn:pulumi:dev::<redacted>-tellme-trainer::aws:s3/bucketServerSideEncryptionConfigurationV2:BucketServerSideEncryptionConfigurationV2::training-input-bucket-encryption
aws:s3/bucketAclV2:BucketAclV2 urn:pulumi:dev::<redacted>-tellme-trainer::aws:s3/bucketAclV2:BucketAclV2::<redacted>--output-acl
aws:iam/rolePolicy:RolePolicy urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicy:RolePolicy::s3-restricted-access
aws:iam/rolePolicyAttachment:RolePolicyAttachment urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicyAttachment:RolePolicyAttachment::sagemaker-full-access
aws:kms/grant:Grant urn:pulumi:dev::<redacted>-tellme-trainer::aws:kms/grant:Grant::aitool-sagemaker-exec-kms-grant-output-bucket
aws:iam/role:Role urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/role:Role::<redacted>-tellme-sf-exec-role
aws:kms/grant:Grant urn:pulumi:dev::<redacted>-tellme-trainer::aws:kms/grant:Grant::aitool-sagemaker-exec-kms-grant-input-bucket
aws:iam/role:Role urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/role:Role::<redacted>-tellme-lambda-role
aws:iam/rolePolicy:RolePolicy urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicy:RolePolicy::lambda-role-access-policy
aws:kms/grant:Grant urn:pulumi:dev::<redacted>-tellme-trainer::aws:kms/grant:Grant::aitool-trainer-lambda-kms-grant
aws:lambda/function:Function urn:pulumi:dev::<redacted>-tellme-trainer::aws:lambda/function:Function::aitool-trainer-process-zendesk
aws:cloudwatch/logGroup:LogGroup urn:pulumi:dev::<redacted>-tellme-trainer::aws:cloudwatch/logGroup:LogGroup::aitool-trainer-process-zendesk-lambda
aws:iam/rolePolicy:RolePolicy urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicy:RolePolicy::aitool-trainer-process-zendesk-lamda-logs
aws:iam/rolePolicy:RolePolicy urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicy:RolePolicy::lambdaInvokeRolePolicyAttachment
aws:iam/rolePolicy:RolePolicy urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicy:RolePolicy::smInvoke
aws:iam/rolePolicyAttachment:RolePolicyAttachment urn:pulumi:dev::<redacted>-tellme-trainer::aws:iam/rolePolicyAttachment:RolePolicyAttachment::cloudWatchFullAccess
aws:s3/bucketServerSideEncryptionConfigurationV2:BucketServerSideEncryptionConfigurationV2 urn:pulumi:dev::<redacted>-tellme-trainer::aws:s3/bucketServerSideEncryptionConfigurationV2:BucketServerSideEncryptionConfigurationV2::training-output-bucket-encryption
aws:sfn/stateMachine:StateMachine urn:pulumi:dev::<redacted>-tellme-trainer::aws:sfn/stateMachine:StateMachine::<redacted>-trainer
Found no pending operations associated with <redacted>/dev
Dependencies:
NAME VERSION
pip 20.3.4
pkg-resources 0.0.0
pulumi-aws 5.19.0
setuptools 44.1.1
Pulumi locates its logs in /tmp by default
Thanks for the update!
I'd like to redact some of the identifiable information from the above if it's not needed please :)
Done. :)
Oh, I think I misunderstood the problem originally. My first answer was about the result type for the function, but you're talking about the resources arg:
resources=[
training_bucket.arn.apply(lambda arn: arn),
training_bucket.arn.apply(lambda arn: f"{arn}/*"),
]
The apply methods are returning an Output[str], but the synchronous getter is expecting a str. I think it should work if you use get_policy_document_output instead.
Thank you for getting back to me and for redacting :)
I may have misunderstood your suggestion.
I've tried with get_policy_document_output instead of get_policy_document but have the same issue.
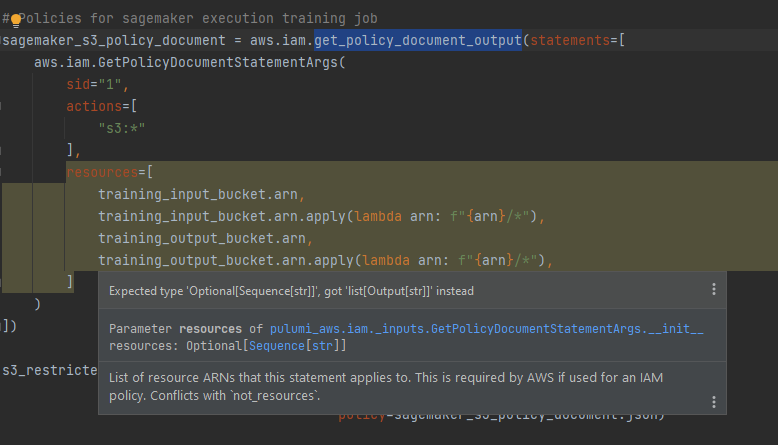
I am not sure how that could fix it since the error is in the constructor of aws.iam.GetPolicyDocumentStatementArg
@pulumi.input_type
class GetPolicyDocumentStatementArgs:
def __init__(__self__, *,
actions: Optional[Sequence[str]] = None,
conditions: Optional[Sequence['GetPolicyDocumentStatementConditionArgs']] = None,
effect: Optional[str] = None,
not_actions: Optional[Sequence[str]] = None,
not_principals: Optional[Sequence['GetPolicyDocumentStatementNotPrincipalArgs']] = None,
not_resources: Optional[Sequence[str]] = None,
principals: Optional[Sequence['GetPolicyDocumentStatementPrincipalArgs']] = None,
resources: Optional[Sequence[str]] = None,
sid: Optional[str] = None):
I did try using aws.iam.get_policy_document_output in the place of aws.iam.GetPolicyDocumentStatementArg, but it definitely didn't like that!
Oh, sure enough. Ok, since the resources arg is not typed as an Input, you would need to wrap the get inside an apply like this:
pulumi.Output.all("arn1", "arn2", "arn3", "etc").apply(lambda args: aws.iam.get_policy_document(statements=[
aws.iam.GetPolicyDocumentStatementArgs(
resources=args,
)
])
https://www.pulumi.com/docs/intro/concepts/inputs-outputs/#all
Does it not make more sense to update aws.iam.GetPolicyDocumentStatementArg? i.e.
resources: Optional[Sequence[str|Output[str]]] = None,
Yes, that would be ideal. Unfortunately, the types are auto-generated from the underlying terraform provider schema, so it's not a simple change.
Ah! That sucks! I think I'll just ignore the type warning then and keep it a wee bit more readable.
Thank you for your help :D It's much appreciated :D
Sure thing! I'll go ahead and close this out since it looks like you got the info you need.