android
 android copied to clipboard
android copied to clipboard
confusing preference setting for TLS
hello team,
i just wanted to point out something that confused me while setting up owntracks.
Enabling TLS in the app seems to refer to TLS client certificates and not just a regular TLS connection.
my setup looks like this:
android app
- preferences -> connection: MQTT
- preferences -> connection -> host: myhost.tld
- preferences -> connection -> port: 443
- preferences -> connection -> identification: user and password i set up in
mosquitto.password - preferences -> connection -> security: TLS == DISABLED
mosquitto-eclipse docker deployment
mosquitto.conf
log_type all
log_facility 5
allow_anonymous false
password_file /mosquitto/config/mosquitto.password
listener 80
protocol websockets
docker-compose
services:
mqtt:
image: eclipse-mosquitto
container_name: otr_mqtt
labels:
traefik.enable: true
traefik.network: traefik
traefik.http.routers.otr_mqtt_websocket.rule: Host(`myhost.tld`)
traefik.http.routers.otr_mqtt_websocket.entrypoints: websecure
traefik.http.services.otr_mqtt.loadbalancer.server.port: 80
volumes:
- ./config:/mosquitto/config/
networks:
- traefik
so my traefik deployment takes care of TLS on the websecure endpoint and enabling the "preferences -> connection -> security: TLS " property in the android app will lead to errors which is a little bit confusing since my MQTT deployment isn't even available without TLS.
I am therefor assuming that this setting just refers to the use of client certificates?
Would it make sense to rename "TLS" in the security settings of the app to "Client Certificates" since the app seems to able to distinguish between HTTP and HTTPS connections without any explicit configuration?
I'm having difficulty reproducing what you've described. The TLS toggle absolutely refers to whether or not the OT client should attempt to connect to the server over TLS, and not whether or not to use client certs. Client certs are used if they're specified, and not if they're not.
The relavent bit of the code is here:
https://github.com/owntracks/android/blob/cf60435c65ff374c7db18ce95e3845bf89488a3d/project/app/src/main/java/org/owntracks/android/services/MessageProcessorEndpointMqtt.java#L205-L214
If I spin up a local mosquitto broker and point the emulator at it:
$ docker run --rm --name mosquitto -p 80:80 -v $(pwd)/mosquitto.conf:/mosquitto/config/mosquitto.conf:ro -v $(pwd)/mosquitto.passwd:/mosquitto/config/mosquitto.password:ro eclipse-mosquitto:2.0.15-openssl
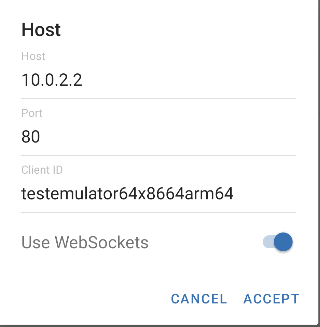
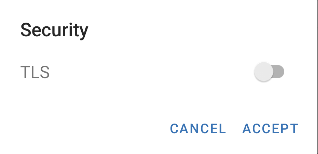
In the OT debug log, I can see the connection string it's building:
2022-08-22 14:01:42.026 4881-5017/org.owntracks.android.debug D/MessageProcessorEndpointMqtt/buildMqttClient/219: client id :testemulator64x8664arm64, connect string: ws://10.0.2.2:80
(N.B. the ws://, meaning plain-text websockets)
and it connects fine. If I enable TLS in the OT app, the log now says:
2022-08-22 14:04:05.301 4881-5017/org.owntracks.android.debug D/MessageProcessorEndpointMqtt/buildMqttClient/219: client id :testemulator64x8664arm64, connect string: wss://10.0.2.2:80
Along with a bunch of errors:
2022-08-22 14:04:06.844 4881-5017/org.owntracks.android.debug E/MessageProcessorEndpointMqtt/reconnect/518: Failed to reconnect to MQTT broker
org.owntracks.android.services.MqttConnectionException: MqttException (0) - javax.net.ssl.SSLException: Unable to parse TLS packet header
which is expected, because the mosquitto endpoint is not TLS.
This smells a lot like your traefik config is not actually doing any TLS. What happens if you try and connect using the s_client on openssl?
$ openssl s_client -connect your-mosquitto-host:443