O1 implementation for handlers signal
Premises
- matcher is the one that will look all or part of the traffic and call InputEventProxy
send_metadata - matcher needs to implement call logic and validate its key metadata
- match is the one that will be called only if its key value pair matches (O(1))
- match handler will only be created if there is a matcher registered with same key
- match and matcher must have the same schema (e.g. "dns")
- match is code agnostic. It allows to connect custom handlers matchers with standard handlers match as long as they have the same schema and key metadata.
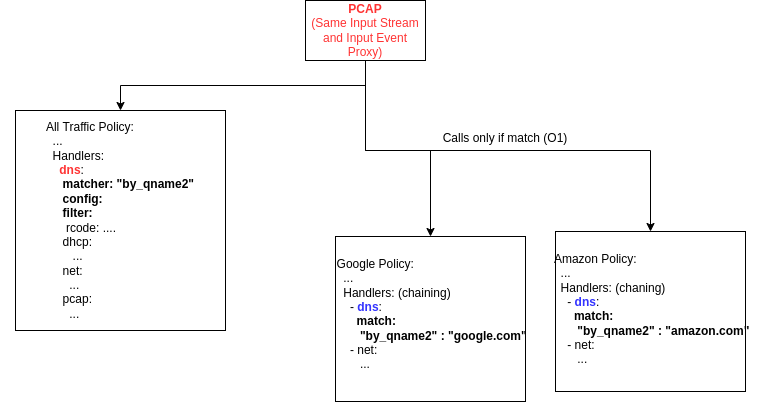
Based on image above we have the call hierarchy for DNS UDP traffic:
- All Traffic Policy DNS Handler will be the matcher, so it register itself as any other module to PcapInputEventProxy
udp_signal. - Google Policy and Amazon Policy DNS Handler are matches, so instead of registering to
udp_signal, they performPcapInputEventProxy::register_udp_predicate_signalto register a callback to be called when the match occurs. - When a packet arrives and it is UDP packet,
PcapInputEventProxy::process_udp_packet_cbis called and it callsudp_signalwhich will trigger All Traffic Policy DNS Handler call. - As All Traffic Policy Policy DNS Handler is a matcher, it will call
PcapInputEventProxy::send_metadatathat will enable the flag_any_match - After
udp_signalfinishes calling all registered signals,PcapInputEventProxy::process_udp_packet_cbmethod will check if there is any match and if so, it will call the matches registered callbacks (O(1))
-process_udp_packet_cb
---udp_signal starts
-----send_metadata
-------udp_signal ends
---------any_match?
------------predicate_udp_signals find
---------------specific signal call
is this still dependent on the order of the policies? i also cannot wrap my head around the names of the concepts here, i will try to think of different names that might be more intuitive.
is this still dependent on the order of the policies? i also cannot wrap my head around the names of the concepts here, i will try to think of different names that might be more intuitive.
It still. @rboucher-ns1 would propose something at Handler level and not policy level. So we should discuss that
@weyrick Just noticed that with that approach we loose the feature to track filtered out counter because the function that track it is never called
@weyrick Just noticed that with that approach we loose the feature to track
filtered out counterbecause the function that track it is never called
That's a small (and acceptable) price to pay
@weyrick Just noticed that with that approach we loose the feature to track
filtered out counterbecause the function that track it is never calledThat's a small (and acceptable) price to pay
Cool ok let's accept losing it for now then. I think there may be options in the future to add it back (based on failing predicates) but adds complication so let's avoid if we can.