oci_core_security_list rule ordering
When creating an oci_core_security_list, the resource appears sensitive to the ordering of the rules. Each time I run the plan in terraform, I get a change operation that removes and re-adds the various rules pointlessly.
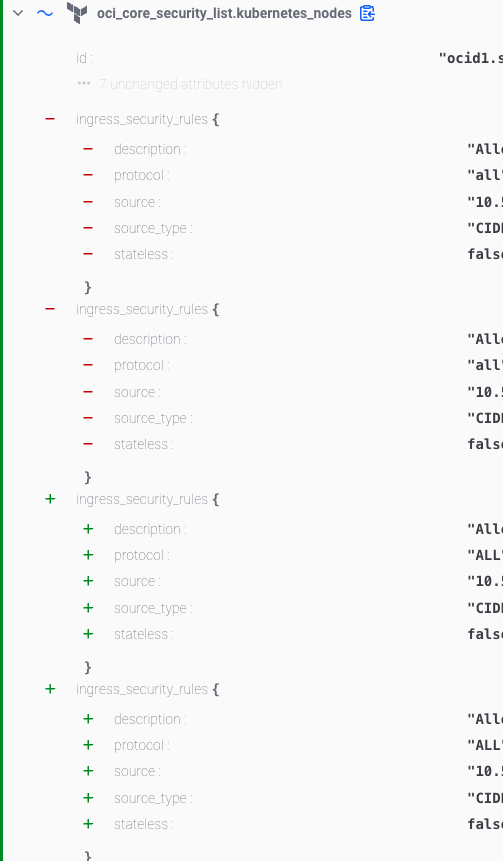
Whilst it's possible to re-arrange the plan to align to the order it prefers, it seems pretty moot and fragile to do it - and temporarily removing access/re-adding it seems inherently disruptive.
Hi @steve-gray thanks for reporting this issue, if possible can yo share config file to debug it further? I used https://github.com/oracle/terraform-provider-oci/blob/master/examples/always_free/main.tf to re-create this issue but I do not see diff in terraform plan output.
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.
Hey @sagarp337 - Unfortunately I can't share our specific configuration, but what I can advise is:
- Modify the demo list so that there's at least 8 rules in the list for both ingress and egress. You can just make up random addresses/ports on the rules.
I believe the issue is probably related to Go's randomisation behaviour, and so because that demo list only has one rule for egress and only a few for the ingress, it's probably not enough records for it to kick in and start randomising. It might be because something internally is using a map.
@ravinitp - Found the issue. The all is case sensitive in the prototype type, so if you set protocols "ALL", it gets replaced with "all" each type, and the OCI API's permit both but consistently report back "all". This means terraform does a pointless state cycle each time. I think you can avoid this by lowercasing the input to prevent the mutation (you can't enforce one case or the other now, as I imagine lots of people have this in their configs)
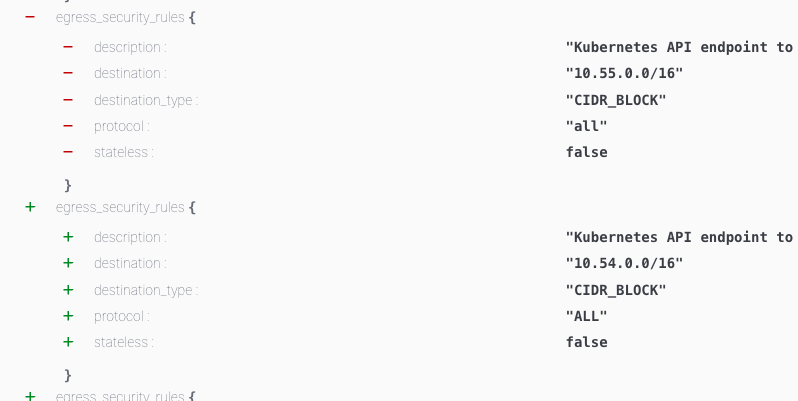
Thank you for reporting the issue. We have raised an internal ticket to track this. Our service engineers will get back to you.