RFC: View web as specific user or member of specific group
For web administrator will be useful to have possibility view site as someone else and avoid to create test accounts. @sbwalker is it possible or it requires huge changes? What do you thing about this feature?
I believe this could be done. The best approach, as I see it would be to build the functionality into a theme as you wouldn't want this in the foundation framework.
DNN had this feature. It was available in the User Management area. You would locate a user in the main list and click Edit.. and in the detailed User UI there was a button for "Impersonate User". There was a lot of debate of whether this button should be visible to only Host users or also Site Administrators - as obviously it has security implications. When this button was clicked, the auth cookie was replaced for the current user with the auth cookie for the selected user - including their role specification. So if you were logged in as a Host user and you impersonated a different user, you would no longer have any Host privileges - you would need to log out and log back in as the Host user if you wanted to restore your privileges. There may be additional technical challenges in implementing this in Oqtane as it is a client/server application and needs to support both Server and WebAssembly scenarios ( which was one of the more tricky aspects to deal with when it comes to auth ). It also may complicate future support for other auth schemes such as OAuth.
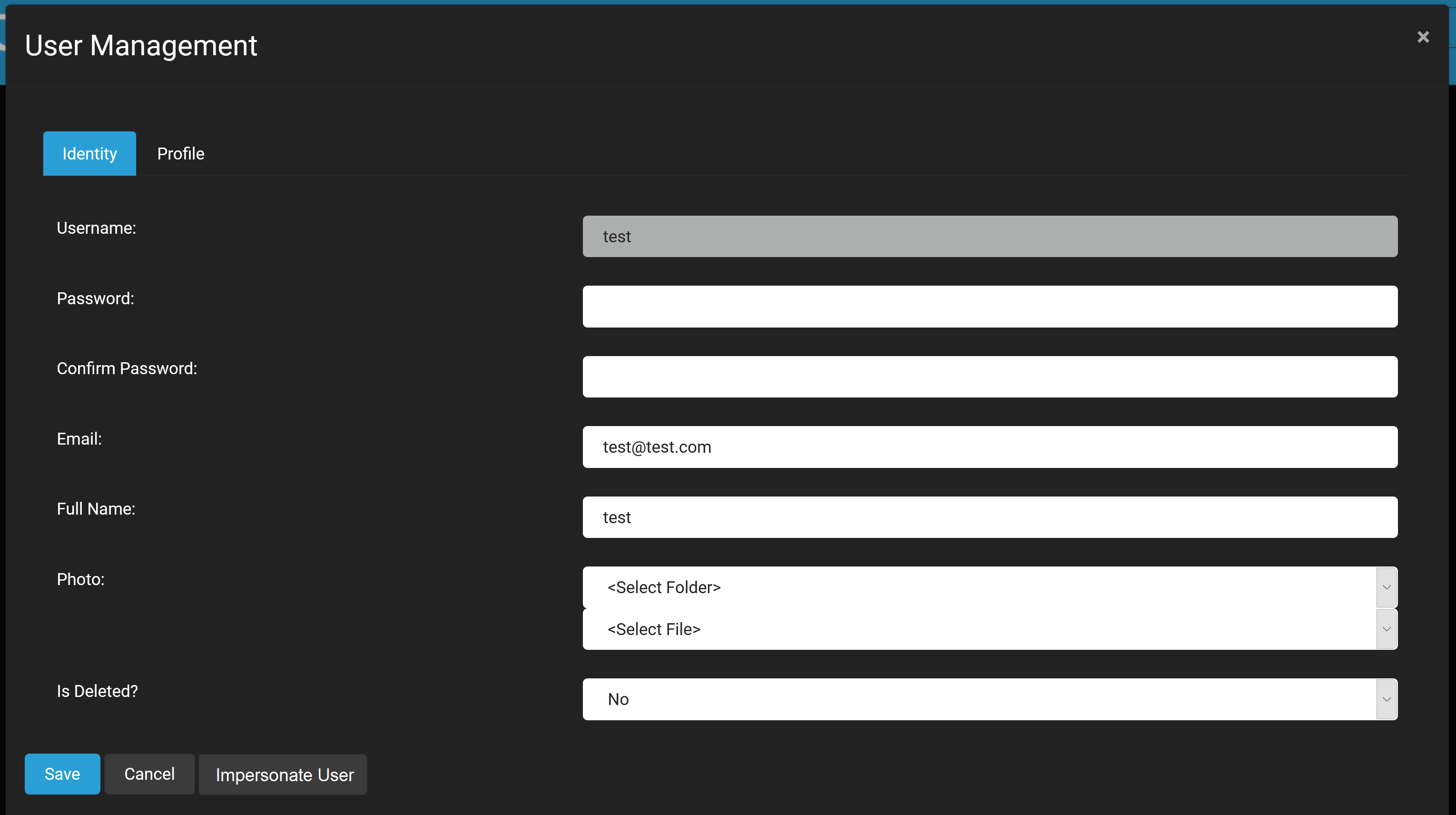
Ok, I see now security implications, test account will be best solution. @sbwalker thank you for answer.
@chlupac to be clear... I actually think this is a very useful feature - I was just trying to point out some of the technical challenges in implementation. If we are able to solve these challenges, I think it would be a good enhancement.
If we are able to solve these challenges
What are the challenges Shaun?
User impersonation is a common feature in many CMSs like: Umbraco, DNN .. ect, I already implemented in OC, I'm not sure what the security implication that @chlupac refer to?
@hishamco the technical challenges of supporting authentication in Blazor for both Server and WebAssembly hosting models is described in this blog: https://www.oqtane.org/Resources/Blog/PostId/527/exploring-authentication-in-blazor. The client/server nature of the framework combined with the behavior of SignalR makes it trickier than expected to deal with auth cookies. A user impersonation feature would need to handle these same issues.
@chlupac @sbwalker I have come across this chapter https://www.thereformedprogrammer.net/adding-user-impersonation-to-an-asp-net-core-web-application/