core
 core copied to clipboard
core copied to clipboard
Feature request: Firewall aliases support BGP AS based queries
Important notices
Before you add a new report, we ask you kindly to acknowledge the following:
- [X] I have read the contributing guide lines at https://github.com/opnsense/core/blob/master/CONTRIBUTING.md
- [X] I am convinced that my issue is new after having checked both open and closed issues at https://github.com/opnsense/core/issues?q=is%3Aissue
Is your feature request related to a problem? Please describe.
On creating dynamic filters like GeoIP-based country filters I see use for BGP AS-network based filters which could be resolved via whois-services to IP-address ranges, similar to GeoIP. This way I could set up for example my ISPs AS that I want to allow WAN-interface some traffic, or my workplace AS to access home-Opnsense.
Describe the solution you like
For example Cloudfare (DNS server 1.1.1.1), I would like to enter BGP AS -alias with AS13335. Opnsense alias-engine should resolve this to subnets registered to AS13335, like using query for 1.1.1.1
% Information related to '1.1.1.0/24AS13335'
route: 1.1.1.0/24 origin: AS13335 descr: APNIC Research and Development 6 Cordelia St mnt-by: MAINT-AU-APNIC-GM85-AP last-modified: 2018-03-16T16:58:06Z source: APNIC
and resolve AS to "route: 1.1.1.0/24" and other routes involved with AS13335. Here is full list of IPv4 prefixes by bgp.he.net -service. https://bgp.he.net/AS13335#_prefixes
For example if Opnsense admin needs to block Facebook, enter AS63293 for alias and define block rule.
Describe alternatives you considered
Alternative way is to manually maintain alias-lists by adding IP-blocks when something goes to non-working, ok I use whois with my new wan-IP to check additional network block and program it. It is very manual and error prone, automated solution would be nice. Very similar to GeoIP automation.
Additional context
Add any other context or screenshots about the feature request here or links to relevant forum thread or similar
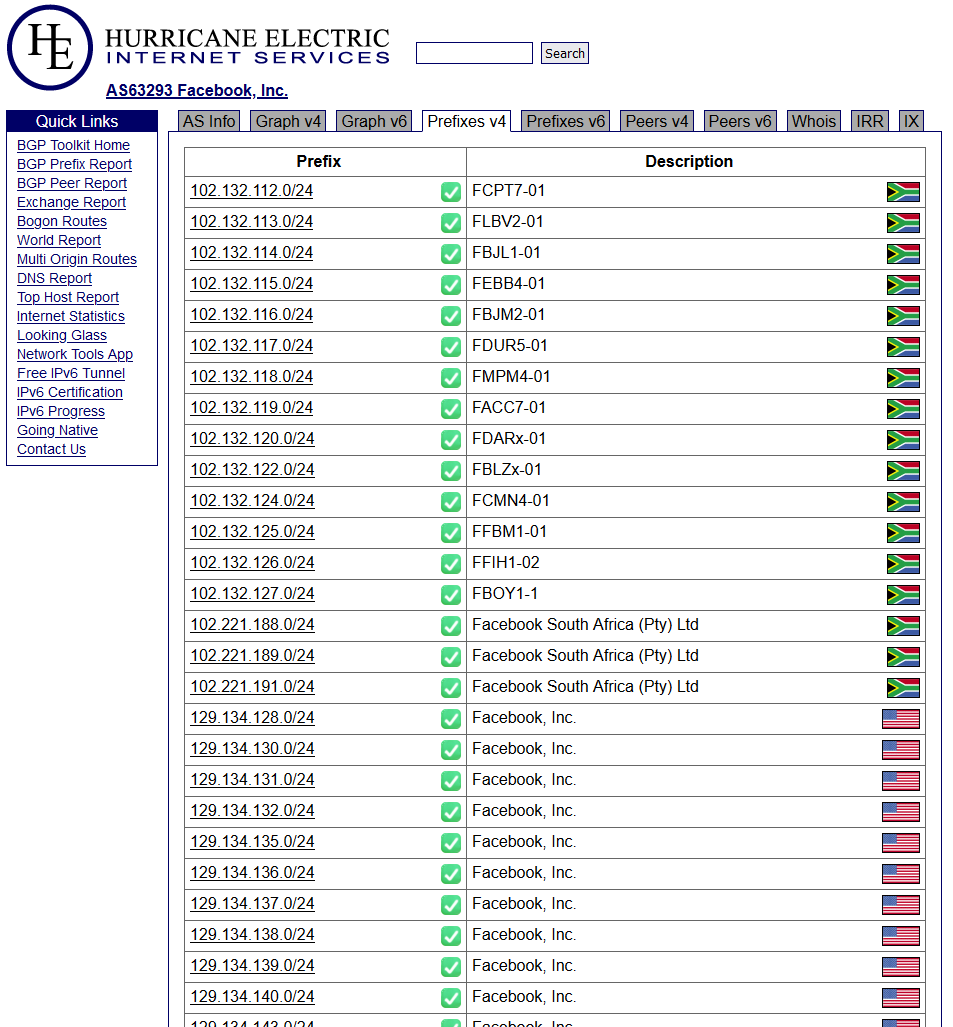
Example screenshot of Facebook AS63293
question appears from time to time, but as far as I know there is no open / free to use list we can safely hook onto and we don't want to risk using someone else's service and be left with empty hands if it disappears. Using other sources is already relatively simple by the way https://forum.opnsense.org/index.php?topic=16585.0
Thank you, did not know this option available via blawk.net.
you're welcome, if someone does know an open and stable source for ASN's, I would still like to add this. It's not very complicated
I do not know which solutions you have already evaluated.
Well for database access either CLI tool "whois" (on Linux side yum install whois) could be used, or RIPE-NCC REST API Search. https://github.com/RIPE-NCC/whois/wiki/WHOIS-REST-API-search
I am not sure if inetnum queries could be returned on one go with AS-number, but probably via AS=>ORG then ORG=>inetnum could be doable. Unfortunately output is not CIDR-notation.
Taken from Ripe-NCC github REST API example: http://rest.db.ripe.net/search?inverse-attribute=org&type-filter=inetnum&source=ripe&query-string=ORG-RIEN1-RIPE
<object type="inetnum"> <link xlink:type="locator" xlink:href="https://rest.db.ripe.net/ripe/inetnum/93.175.159.0 - 93.175.159.255"/> <source id="ripe"/> <primary-key> <attribute name="inetnum" value="93.175.159.0 - 93.175.159.255"/> </primary-key> <attributes> <attribute name="inetnum" value="93.175.159.0 - 93.175.159.255"/> <attribute name="netname" value="NL-RIPENCC-ADMINDNS"/> <attribute name="country" value="SE"/>
I'm not sure how this helps to be honest, given the example for AS13335 how would this return the registered networks? a list that could be prefetched would be most practical to handle, but I don't think it exists (from an open source)
The query returns all networks, so task for Opnsense would just be parsing the output..
`
curl -s "http://rest.db.ripe.net/search?inverse-attribute=org&flags=no-referenced&type-filter=inetnum&source=ripe&query-string=ORG-RIEN1-RIPE" | xq '."whois-resources".objects.object[]."primary-key".attribute."@value"'
"193.0.0.0 - 193.0.23.255" "193.0.0.0 - 193.0.7.255" "84.205.64.0 - 84.205.95.255" "93.175.144.0 - 93.175.158.255" "93.175.159.0 - 93.175.159.255" `
then maybe running like and storing to create list on Opnsense drive: https://www.unix.com/shell-programming-and-scripting/233825-convert-ip-ranges-cidr-netblocks.html
Also I see ntopng is resolving AS-number but in reverse to our need (IP => AS, we need AS => IP-blocks). But perhaps ntopng source code could the checked for their solution for API. CLI whois-client has been for decades so maybe that is the best most stable API.
Ntopng forwards external url to https://stats.ripe.net/ASxxxx so maybe it is using RIPE as AS-source too.
converting addresses isn't the challenge, if you believe we could parse output (I don't see how), maybe best explain step by step how to retrieve ranges / masks from an ASN (use AS13335). I'll happily take a look, just don't see how this leads to the desired feature.
So start with AS13335 and go from there.
My experimental solution would be.. To get xq => pip3 install yq, and convert curl to fetch for freebsd?
` curl -s https://rest.db.ripe.net/search?query-string=AS13335 | xq '."whois-resources".objects.object[]."primary-key"'
{ "attribute": { "@name": "as-block", "@value": "AS13312 - AS13878" } } { "attribute": { "@name": "aut-num", "@value": "AS13335" } } { "attribute": { "@name": "organisation", "@value": "ORG-CI40-RIPE" } } { "attribute": { "@name": "nic-hdl", "@value": "CAC80-RIPE" } } { "attribute": { "@name": "nic-hdl", "@value": "CTC6-RIPE" } } `
then use organization-attribute "@value" to fetch AS-list on second query
` curl -s "http://rest.db.ripe.net/search?inverse-attribute=org&flags=no-referenced&type-filter=inetnum&source=ripe&query-string=ORG-CI40-RIPE" | xq '."whois-resources".objects.object[]."primary-key".attribute."@value"[]'
"141.101.64.0 - 141.101.127.255" "185.122.0.0 - 185.122.3.255" "188.114.96.0 - 188.114.111.255" `
Maybe with doing more research there could be way of doing single query, above is just experimenting how to get the data. And maybe ntopng has resolved it somehow.
but when I compare to ntopng steered stats.ripe.net I see naturally big difference, maybe some more recursion is needed or something. Or maybe this is just that RIPE stats decode above prefixes to /24 prefixes and smaller by BGP adds.. https://stat.ripe.net/app/launchpad/S1_13335_C13C31C4C34C9C22C28C20C15C6C7C26C29C30C14C17C2C21C33C16C10 AS Prefix Count AS13335 has 1496 IPv4 Prefixes and 1047 IPv6 Prefixes
This is how Opnsense installed ntopng-plugin shows AS13335

And how ntopng shows "AS Prefixes" via RIPE NCC, so I would say perhaps ntopng source code could be identified for better solution compared what I quickly built.

I think they use https://db-ip.com/db/download/ip-to-asn-lite for the mapping (https://github.com/ntop/ntopng/blob/d7f4b1c869e0e2301623e211fde7f655c7f9c20b/packages/FreeBSD/build.sh.in#L71), given that it's distributed under creative commons we might be able to use it license wise.
The file they offer is quite easy to parse:
1.0.0.0,1.0.0.255,13335,"Cloudflare, Inc."
1.0.4.0,1.0.7.255,38803,"Wirefreebroadband Pty Ltd"
1.0.64.0,1.0.127.255,18144,"Energia Communications,Inc."
1.0.128.0,1.0.255.255,23969,"TOT Public Company Limited"
.....
Interesting read https://www.quaxio.com/bgp/ , the lists we're actually looking for are probably https://thyme.apnic.net/current/ipv6-raw-table (ipv6) and https://thyme.apnic.net/current/data-raw-table (ipv4)
this https://github.com/opnsense/core/commit/b6f95cdea429d243f1e70f55ce817407264eb60f should be more or less it, need to merge the files on our end and publish on daily bases and needs a documentation update.
Lovely .. thank you both ❤️
Done and queued up for 22.7.2