okta-aws-cli
 okta-aws-cli copied to clipboard
okta-aws-cli copied to clipboard
Multiple AWS environments support for non-Admin level user
It appears that the API call to GET /api/v1/apps is not permitted for non-admin users even if the OIDC native app has been granted okta.apps.read grant.
Regardless of that GET /api/v1/groups/me/appLinks and GET /api/v1/users/me/groups (each requires grant okta.users.read.self) is probably a more accurate way to determine what AWS Fed apps are assigned to a user directly or by group instead of just looking at all apps in GET /api/v1/apps.
However, the OAuth grant okta.users.read.self also seems to be useful for Admin only users. I'm still looking for an alternatives
Okta internal reference: https://oktainc.atlassian.net/browse/OKTA-574636
GET /api/v1/users/${userId}/appLinks
https://developer.okta.com/docs/reference/api/users/#get-assigned-app-links
"Fetches appLinks for all direct or indirect (via group membership) assigned applications"
Shouldn't need to look at groups
Need to confirm, seems to indicate admin-only for API calls https://developer.okta.com/docs/guides/implement-oauth-for-okta/main/ https://developer.okta.com/docs/guides/create-an-api-token/main/#privilege-level
Hello
Is this related to this error ?
Error: fetching SSO web token received API response "400 Bad Request", error: "invalid_grant", description: "The target audience app must be configured to allow the client to request a 'web_sso_token'."
I get it when a non-admin Okta user try to connect to the app.
@QuentinBtd does it work for as an admin user and not a regular user? Or it doesn't work at all?
If it works with an admin user, but not a regular user I'd expect to see an error like:
Open the following URL to begin Okta device authorization for the AWS CLI
https://yourorg.okta.com/activate?user_code=ABCDEFGH
Error:
There aren't any AWS Federation Applications associated with OIDC App "0oa4xzzzzzzzzzzzzzzz".
Check if it has "okta.apps.read" scope and is the allowed web SSO client for an AWS
Federation app. Or, invoke okta-aws-cli including the client ID of the
AWS Federation App with --aws-acct-fed-app-id FED_APP_ID
@QuentinBtd Your error "The target audience app must be configured to allow the client to request a 'web_sso_token'." looks to me you don't have the settings correct on your OIDC Native App, they'll look something like:
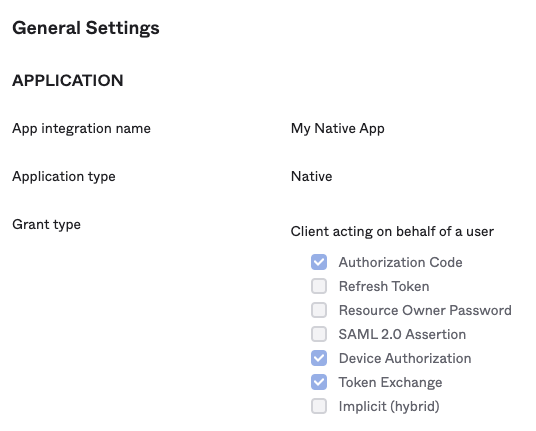
@monde It works perfectly for me, with an Okta admin role.
I have the error with a regular user.
The same parameters as yours are configured in my OIDC Native App.
okta.apps.read is granted in the API scopes.
For your information, our AWS Integration is configured to use SAML as Sign On Method.
Hello @monde
I just retry it with me (okta admin), it always works. But with a regular okta user who has two application in assignments:
- AWS application
- OIDC application
I have this error in debug with --debug-api-calls option
Error:
There aren't any AWS Federation Applications associated with OIDC App "My_OIDC_App_ID".
Check if it has "okta.apps.read" scope and is the allowed web SSO client for an AWS
Federation app. Or, invoke okta-aws-cli including the client ID of the
AWS Federation App with --aws-acct-fed-app-id FED_APP_ID
I created an administrator profile with permission to see the details of both applications. I assigned this profile to my user and then tried to connect again with okta-aws-cli. It worked.
Hello @monde
I just retry it with me (okta admin), it always works. But with a regular okta user who has two application in assignments:
- AWS application
- OIDC application
I have this error in debug with
--debug-api-callsoptionError: There aren't any AWS Federation Applications associated with OIDC App "My_OIDC_App_ID". Check if it has "okta.apps.read" scope and is the allowed web SSO client for an AWS Federation app. Or, invoke okta-aws-cli including the client ID of the AWS Federation App with --aws-acct-fed-app-id FED_APP_IDI created an administrator profile with permission to see the details of both applications. I assigned this profile to my user and then tried to connect again with okta-aws-cli. It worked.
I just realized that I forgot to use the --aws-acct-fed-app-id option. Everything works better with it.
And thanks for the v1.0.0 ! ❤️
@monde do you have an idea when this will be addressed? I do not think my org is going to allow us to use the admin hack mentioned in the README to support non-admin users
@jefftaylor-okta can you speak on the non-admin multi org functionality? I know that it will take effort on the Okta core side.
Any update here @monde @jefftaylor-okta? Our company is now constantly rescheduling the upgrade due to the "admin hack" does not match our security policies.
Do we have any updates on this? Is this still an issue people are dealing with?
This hack is extremely obnoxious as we deal with users. This is over a year old, any idea when it's going to get prioritized?
GET /api/v1/users/{userId}/appLinks is an option for non-admin listing of apps:
https://developer.okta.com/docs/api/openapi/okta-management/management/tag/User/#tag/User/operation/listAppLinks
However, experimenting with it I see that is only returning directly assigned "amazon_aws" apps, not any that are assigned by group.
checkout v2.2.0 release https://github.com/okta/okta-aws-cli/releases/tag/v2.2.0
non-Admin users seemly supported if OIDC app has okta.users.read.self scope granted
https://github.com/okta/okta-aws-cli?tab=readme-ov-file#non-admin-users