next-auth
 next-auth copied to clipboard
next-auth copied to clipboard
Configuring Issuer without Discovery isn't possible
Description 🐜
I am trying to configure a custom OAuth Provider without using Issuer discovery (the reason being due to some unhealthy internal DNS shenanigans I need to use URLs different from the ones in the discovery metadata document).
However, I am running into this error: https://next-auth.js.org/errors#callback_oauth_error jwks_uri must be configured on the issuer TypeError: jwks_uri must be configured on the issuer
[next-auth][error][CALLBACK_OAUTH_ERROR]
https://next-auth.js.org/errors#callback_oauth_error jwks_uri must be configured on the issuer TypeError: jwks_uri must be configured on the issuer
at assertIssuerConfiguration (C:\projekte\ifp\ui\node_modules\openid-client\lib\helpers\assert.js:17:11)
at Issuer.getKeyStore (C:\projekte\ifp\ui\node_modules\openid-client\lib\helpers\issuer.js:22:3)
at Issuer.queryKeyStore (C:\projekte\ifp\ui\node_modules\openid-client\lib\helpers\issuer.js:83:38)
at Client.validateJWT (C:\projekte\ifp\ui\node_modules\openid-client\lib\client.js:1046:34)
at Client.validateIdToken (C:\projekte\ifp\ui\node_modules\openid-client\lib\client.js:763:60)
at Client.callback (C:\projekte\ifp\ui\node_modules\openid-client\lib\client.js:484:18)
I configured jwks_uri (which the types don't actually allow on the custom Provider, I think the types are wrong here) as well as jwks_endpoint), and neither one is used.
The reason for this seems to be: https://github.com/nextauthjs/next-auth/blob/227ff2259fa8dd3335b3e0a3b01c762c0240d201/src/core/lib/oauth/client.ts#L22
In the non-discovery case, only 4 properties are passed to the oidc-client Issuer constructor, and jwks_uri isn't one of them.
Is this a bug in your own project?
No
How to reproduce ☕️
Try constructing any OIDC custom provider without using the wellKnown property.
Screenshots / Logs 📽
No response
Environment 🖥
System: OS: Windows 10 10.0.19043 CPU: (8) x64 Intel(R) Core(TM) i7-8550U CPU @ 1.80GHz Memory: 2.27 GB / 15.85 GB Binaries: Node: 16.13.1 - C:\Program Files\nodejs\node.EXE Yarn: 1.22.11 - ~\AppData\Roaming\npm\yarn.CMD npm: 8.3.0 - C:\Program Files\nodejs\npm.CMD Browsers: Chrome: 97.0.4692.71 Edge: Spartan (44.19041.1266.0), Chromium (96.0.1054.62) Internet Explorer: 11.0.19041.1202 npmPackages: next: 12.0.7 => 12.0.7 next-auth: ^4.0.6 => 4.0.6 react: 17.0.2 => 17.0.2
Contributing 🙌🏽
Yes, I am willing to help solve this bug in a PR
Is anyone still looking into this issue?
I am also using a custom Oauth provider and running into the same issue "jwks_uri must be configured on the uri" The provider has not configured encryption on the client - how can I bypass this?
I am using: "next": "^12.2.2", "next-auth": "^4.10.0", "react": "^18.2.0 pnpm 7.0.0
any update on this?? I'm getting the same error, and I cant find anything on documentation.
Same issue with Salesforce provider:
[next-auth][error][CALLBACK_OAUTH_ERROR]
https://next-auth.js.org/errors#callback_oauth_error jwks_uri must be configured on the issuer TypeError: jwks_uri must be configured on the issuer
at assertIssuerConfiguration (/home/craig.crawford/salesforce-demo/node_modules/openid-client/lib/helpers/assert.js:17:11)
at Issuer.getKeyStore (/home/craig.crawford/salesforce-demo/node_modules/openid-client/lib/helpers/issuer.js:22:3)
at Issuer.queryKeyStore (/home/craig.crawford/salesforce-demo/node_modules/openid-client/lib/helpers/issuer.js:83:38)
at Client.validateJWT (/home/craig.crawford/salesforce-demo/node_modules/openid-client/lib/client.js:1033:34)
at Client.validateIdToken (/home/craig.crawford/salesforce-demo/node_modules/openid-client/lib/client.js:743:60)
at Client.callback (/home/craig.crawford/salesforce-demo/node_modules/openid-client/lib/client.js:486:18)
at processTicksAndRejections (/home/craig.crawford/salesforce-demo/lib/internal/process/task_queues.js:96:5)
at async oAuthCallback (/home/craig.crawford/salesforce-demo/node_modules/next-auth/core/lib/oauth/callback.js:114:16)
at async Object.callback (/home/craig.crawford/salesforce-demo/node_modules/next-auth/core/routes/callback.js:50:11)
at async NextAuthHandler (/home/craig.crawford/salesforce-demo/node_modules/next-auth/core/index.js:186:28) {name: 'OAuthCallbackError', code: undefined, stack: 'TypeError: jwks_uri must be configured on the…/node_modules/next-auth/core/index.js:186:28)', message: 'jwks_uri must be configured on the issuer'}
export const authOptions: NextAuthOptions = {
debug: process.env.NODE_ENV === 'development' || process.env.NODE_ENV === 'test',
// Configure one or more authentication providers
providers: [
SalesforceProvider({
idToken: true,
issuer: "https://login.salesforce.com",
clientId: process.env.SF_ID,
clientSecret: process.env.SF_SECRET,
authorization: {
params: {
scope: "api id web full refresh_token",
},
},
}),
],
callbacks: {
async signIn({ user, account, profile, email, credentials }) {
if (!profile) return false;
user.id = profile.user_id as string
user.email = profile.email
user.image = profile.picture as string
user.name = profile.name
return true;
},
async redirect({ url, baseUrl }) { return baseUrl },
// async session({ session, token, user }) { return session },
async jwt({ token, user, account, profile, isNewUser }) {
if (account && account.provider) {
if (!token[account.provider]) {
token[account.provider] = {};
}
if (account.access_token) {
(token[account.provider] as any).accessToken = account.access_token;
}
if (account.refresh_token) {
(token[account.provider] as any).refreshToken = account.refresh_token;
}
}
return token;
}
}
}
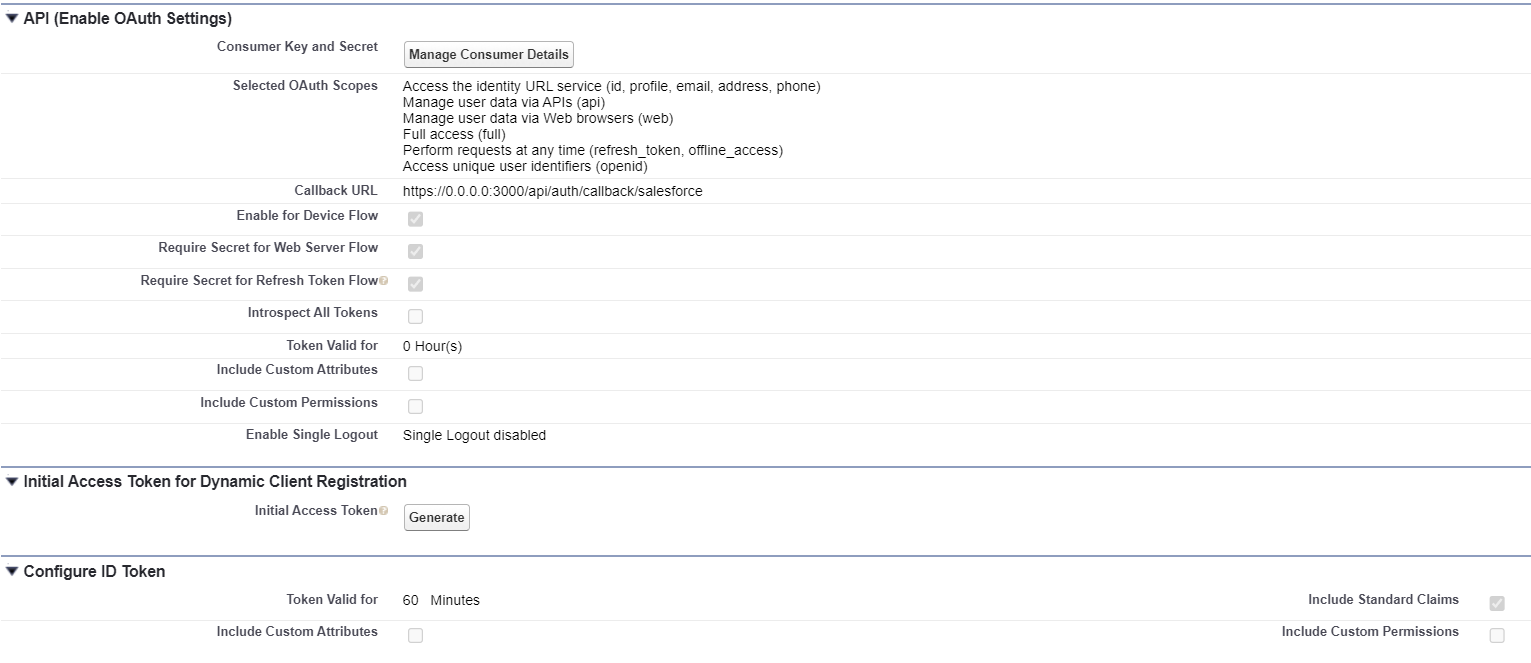
Removing full from scope and setting idToken: false seems to work, however and login is successful...
Additionally, when setting wellKnown: "https://login.salesforce.com/.well-known/openid-configuration", the result is:
stack: 'TypeError: Cannot read properties of undefined (reading 'toString')
at getProfile (/home/craig.crawford/salesforce-demo/node_modules/next-auth/core/lib/oauth/callback.js:178:39)
at async oAuthCallback (/home/craig.crawford/salesforce-demo/node_modules/next-auth/core/lib/oauth/callback.js:141:27)
at async Object.callback (/home/craig.crawford/salesforce-demo/node_modules/next-auth/core/routes/callback.js:50:11)
at async NextAuthHandler (/home/craig.crawford/salesforce-demo/node_m…-auth/next/index.js:59:32
at async Object.apiResolver (/home/craig.crawford/salesforce-demo/node_modules/next/dist/server/api-utils/node.js:184:9)
at async DevServer.runApi (/home/craig.crawford/salesforce-demo/node_modules/next/dist/server/next-server.js:403:9)
at async Object.fn (/home/craig.crawford/salesforce-demo/node_modules/next/dist/server/base-server.js:493:37)
at async Router.execute (/home/craig.crawford/salesforce-demo/node_modules/next/dist/server/router.js:222:36)'
According to SalesForce, this URL is "OpenID Connect discovery endpoint".
To make this work I had to set on the provider (copied from SalesForce provider but modified to use at_hash instead of user_id)
profile(profile) {
return {
id: profile.sub,
name: null,
email: null,
image: profile.picture
};
},
and in callbacks:
async signIn({ user, account, profile, email, credentials }) {
if (!profile) return false;
user.id = profile.sub as string
user.email = profile.email
user.image = profile.picture as string
user.name = profile.name
return true;
},
I have no idea if this is the right way to do this, but it seems to work 🤷 (for SalesForce provider at least). I'm not sure why it won't work so easily out of the box...
same issue I created a custom config with Ping
I tried this patch , which is working for me with Ping. please test with your config: https://github.com/xmlking/svelte-starter-kit/blob/main/patches/%40auth__core%400.2.4.patch