OLLVM_Deobfuscation
 OLLVM_Deobfuscation copied to clipboard
OLLVM_Deobfuscation copied to clipboard
OLLVM_Deobfuscation is a Python-based ollvm deobfuscation tool, which now has a perfect performance on ollvm confused C / C + + code compiled on x86 architecture based Linux platform.
OLLVM_Deobfuscation
OLLVM_Deobfuscation 是一款基于Python的OLLVM反混淆工具,目前已经能完美实现x86架构Linux平台下被ollvm混淆过的C/C++代码的反混淆,后续将逐步尝试Android SO文件的反混淆
0x01 安装
OLLVM_Deobfuscation依赖以下环境:
- 1)angr: a python framework for analyzing binaries.
- 2)BARF: A multiplatform open source Binary Analysis and Reverse engineering Framework
- 3)Z3: A high-performance theorem prover being developed at Microsoft Research.
- 4)CVC4: An efficient open-source automatic theorem prover for satisfiability modulo theories (SMT) problems.
0x02 使用
我们就以工程test文件下,经OLLVM平坦化混淆后的target_int_32_flat做反混淆测试用例,执行以下命令进行反混淆
$ workon angr
$ cd path_to_the/barf
$ python ./src/Deobfuscation.py ./test/target_int_32_flat 0x8048420
0x03 Miasm vs OLLVM_Deobfuscation
What is Miasm
Miasm是一款基于Python的逆向框架,自身具备符号执行引擎和IR中间语言语义解析功能,能解析PE / ELF 32等多种格式,并支持X86 / ARM / MIPS / SH4 / MSP430等多种平台
原理功能
Miasm和OLLVM_Deobfuscation的详细对比如下:
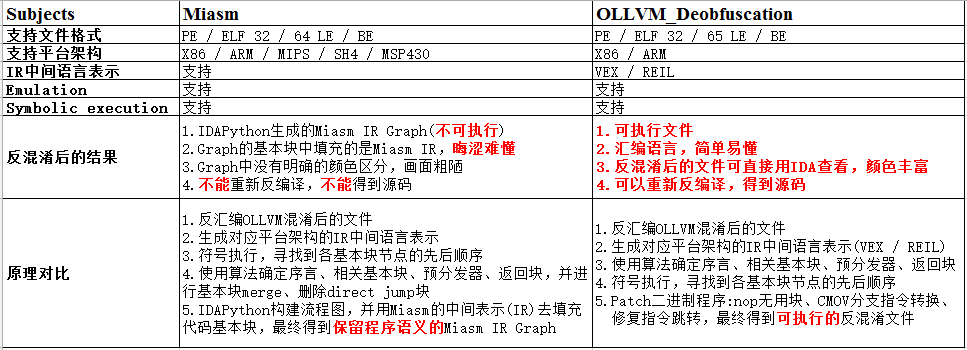
效果截图
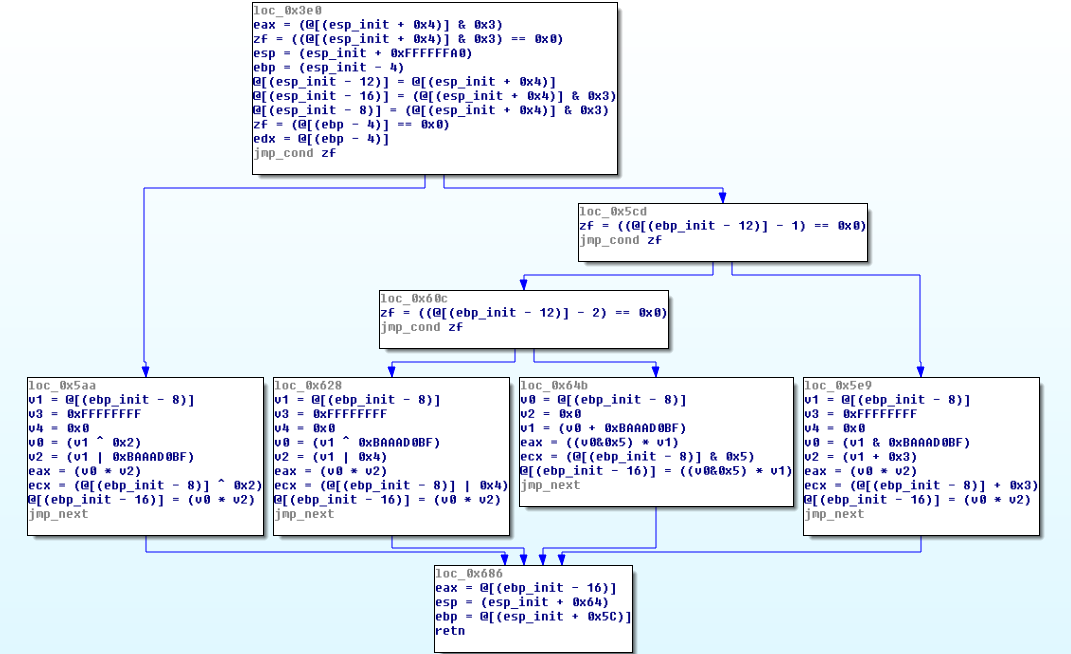
分别使用Miasm和OLLVM_Deobfuscation对target_int_32_flat进行反混淆,其反混淆效果截图如下所示:
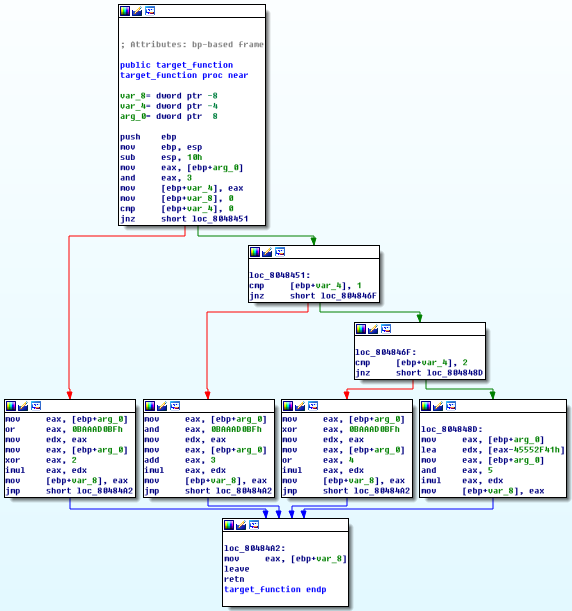
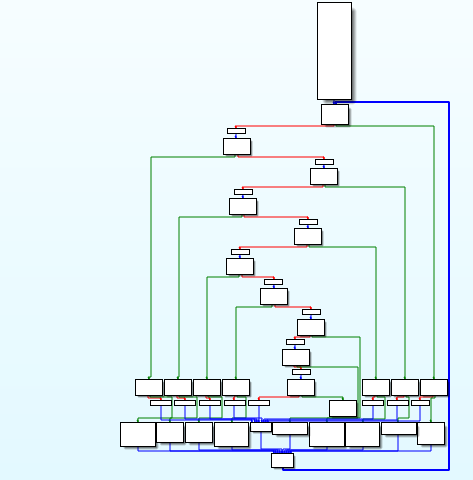
 (c)Miasm反混淆效果截图
(c)Miasm反混淆效果截图
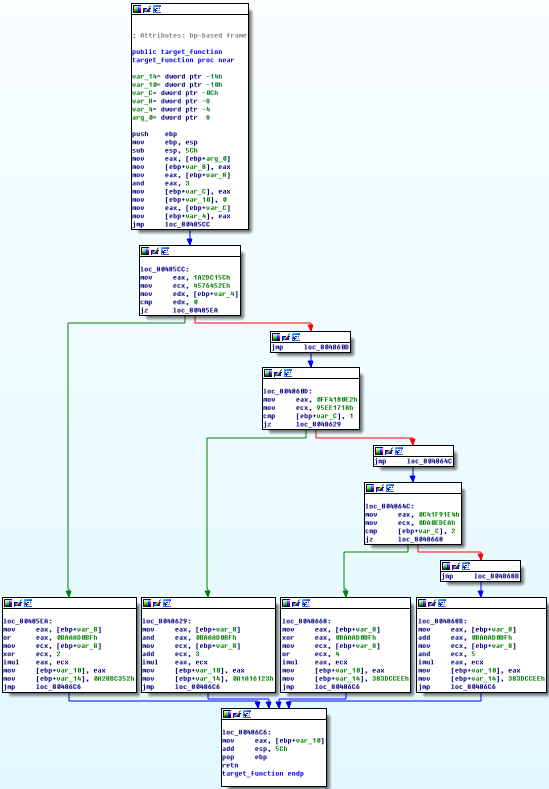
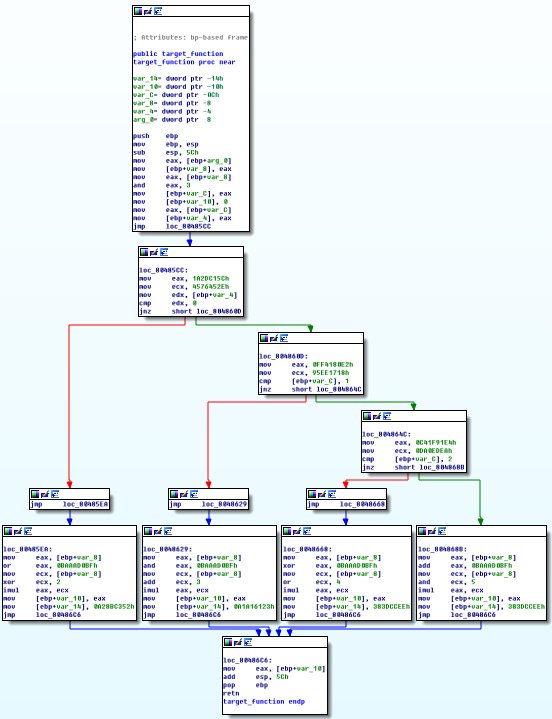
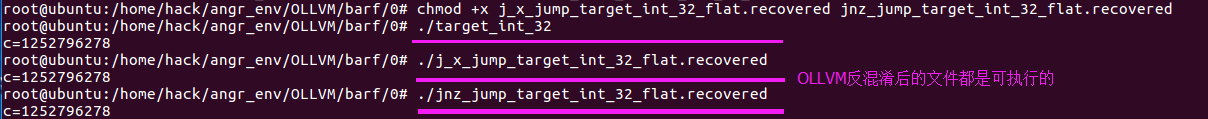 (f)OLLVM_Deobfuscation反混淆文件运行截图
(f)OLLVM_Deobfuscation反混淆文件运行截图
0x04 Reference
- [1]Deobfuscation: recovering an OLLVM-protected program: https://blog.quarkslab.com/deobfuscation-recovering-an-ollvm-protected-program.html
- [2]反混淆:恢复被OLLVM保护的程序: http://www.freebuf.com/articles/terminal/130142.html
- [3]angr API documentation: http://angr.io/api-doc/
- [4]angr-doc: https://github.com/angr/angr-doc/blob/master/docs/states.md
- [5]BARF : Binary Analysis and Reverse engineering Frameworkhttps://github.com/programa-stic/barf-project