terraform-provider-keycloak
 terraform-provider-keycloak copied to clipboard
terraform-provider-keycloak copied to clipboard
Terraform provider for Keycloak
Missing documentation about the resource `keycloak_attribute_to_role_identity_provider_mapper` in [official docs](https://registry.terraform.io/providers/mrparkers/keycloak/latest/docs). P.S. The resource by itself is working 👍 .
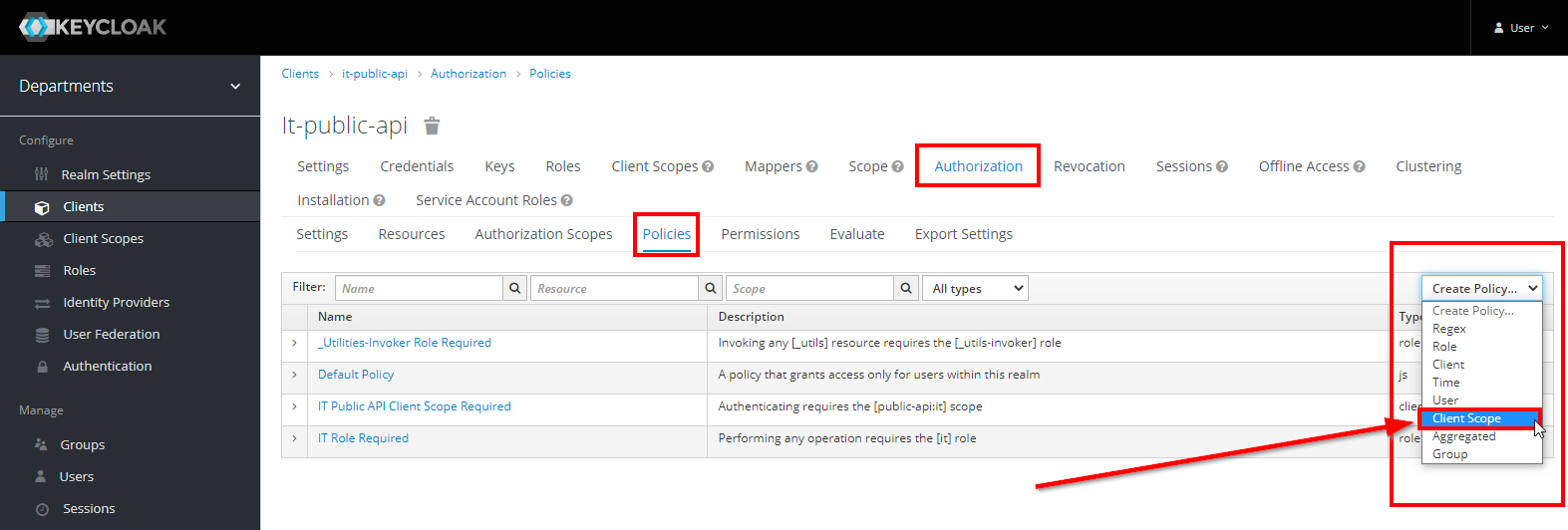 I'm pretty new to using this Terraform provider but I've found that I can easily create `role` authorization policies but cannot seem to find a way to create/manage `client-scope`...
Solves https://github.com/mrparkers/terraform-provider-keycloak/issues/928 What has been changed : - new `ExcludeIssuerFromAuthResponse` attribute in the client - the resource schema is updated with `ExcludeIssuerFromAuthResponse` attribute - the datasource `openid_client` also returns this...
Currently only the realm roles are allowed to be added, however some of the client roles could be found in a fresh installation, taking this as an example: The last...
# Problem Can we set client roles using tf resource keycloak_default_roles ? i get the following error when creating an default role with client roles present. ``` keycloak_default_roles.default_roles: Creating... ╷...
This feature introduces the capability to create and manage custom Realm keystores within Keycloak. Currently, this provider only supports configuring keystores defined in the Keycloak core, leaving out those defined...
It seems as if "Login Settings" block in Realm session settings is missing. The two fields "login timeout", and "login action timeout" are not seen in docs, or I am...
... but only realm roles instead. My use case: In a development instance of the Keycloak I want all users in a custom realm to assume the role `realm-management/realm-admin`, where...
When Keycloak is deployed with an administration hostname different from the base one (for example to whitelist admin accesses), the provider should use the base URL for client credentials authentication...
The LDAP user federation supports connection pooling. It can be enabled using the GUI:  It could be supported in the keycloak_ldap_user_federation resource and data source.
