mozilla-aws-cli

mozilla-aws-cli copied to clipboard
Add user access revocation support
In the case where a user's access is revoked by the IdP, this tool should notice this and revoke the associated AWS rights.
Or maybe this should happen through another pathway not controlled on the users endpoint (e.g. an integration directly between the IdP and AWS that notices a revocation and actively invalidates outstanding STS credentials.)
https://hackmd.io/-gy2I9uKR_SS1Rdv6BnX8g?view
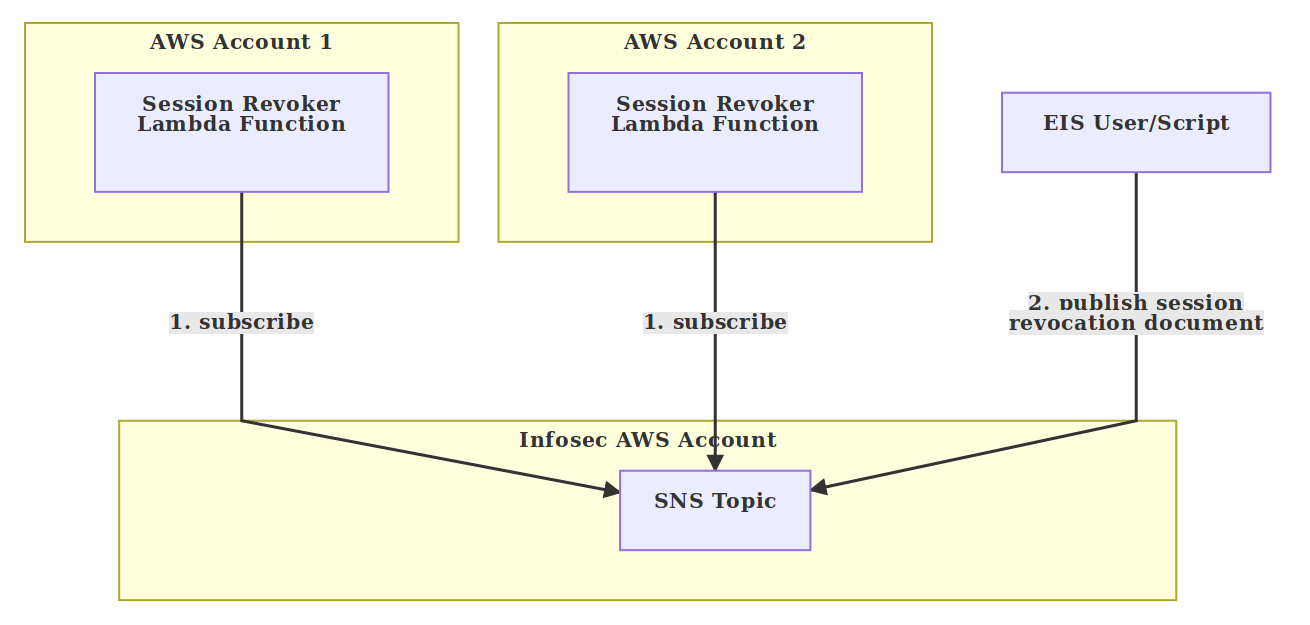
Session revocation document
{
"groups": [
"team_opsec",
"team_hr"
],
"time": "30 minutes ago",
"action": "revoke"
}
groups: A list of group namestime: A datetime parseable by pythondateparseraction: Eitherrevokeorcleanup
Session Revoker Lambda Function Logic
- Parse session revocation document
- Fetch all IAM role in the AWS account
- Iterate over the trust policies for each policy associated with each IAM role
- Check if the trust policy trusts the Mozilla federated identity provider. If it does not, move on to the next IAM role
- Check the conditions to see if they contain any of the groups listed in the
groupskey of the session revocation document - If the trust policy does not contain any of the groups move on to the next IAM role
- Modify the role and add an inline policy which denies all actions (
*:*) where theaws:TokenIssueTimeis less than thetimevalue in the session revocation document - Create a CloudWatch/EventBridge Rule to clean up the deny policy
- The name of the rule contains a GUID that the function generates
- The time of the CloudWatch Rule's schedule expression should be duration of the maximum session length of an STS credential, in the future. So if the max STS session was 3 days, the schedule expression would be 3 days in the future
- The CloudWatch Rule invokes the session revoker lambda function passing it a document like
{ "groups": [ "team_opsec", "team_hr" ], "rule_id": "the GUID generated", "action": "cleanup" }
Session Revoker Lambda Function Clean Up Logic
When the session revoker lambda function runs with the cleanup action it does the following steps
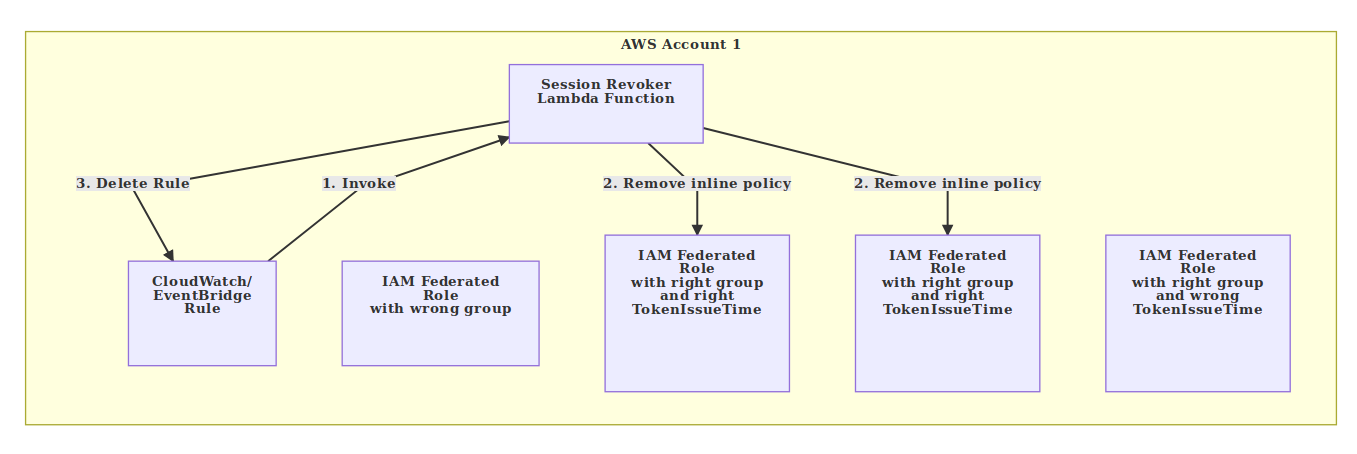
- Fetch all IAM role in the AWS account
- Iterate over the inline policies for all the roles, checking if the policy is a revokation policy (contains a
aws:TokenIssueTimecondition anddeny) - Checks if the TokenIssueTime is older than the maximum STS session length, if so delete the inline policy, if not do nothing
- Finally the lambda function deletes the CloudWatch/EventBridge rule that triggered it using the GUID in
rule_idto identify the correct rule
Seems like good fodder for a cloudwatch event that periodically scans auth0 and revokes any outstanding tokens.