PESCMS-Ticket
 PESCMS-Ticket copied to clipboard
PESCMS-Ticket copied to clipboard
Vulnerability Report: rXss
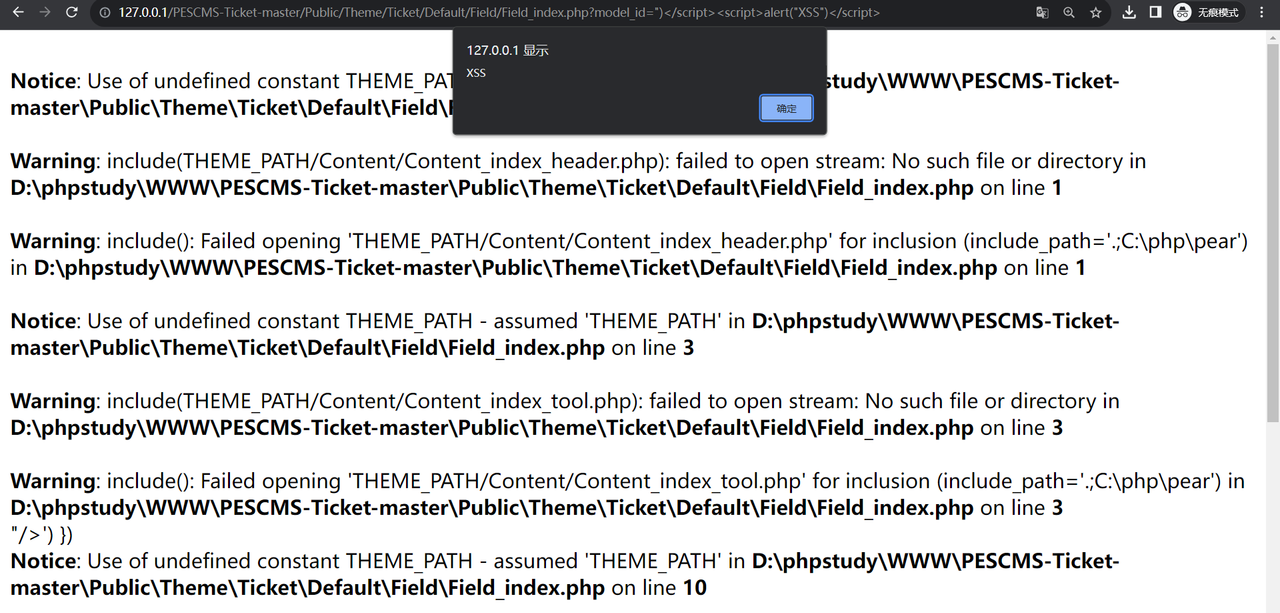
I found a rXss vulnerability in the latest version of PESCMS Ticket, 'model_id' and 'back_url' input was not safely sanitized.
- Impact: The attacker can execute a HTML/JS Code (the attacker can stealing cookies,etc..)
- Environment: Windows 10/PHP 7.0.12
- File path: Vulnerable files in './PESCMS-Ticket-master/Public/Theme/Ticket/Default/Field/Field_index.php' line 6
$(function(){
$("input[name=keyword]").after('<input type="hidden" name="model_id" value="<?=$_GET['model_id']?>"/><input type="hidden" name="back_url" value="<?=$_GET['back_url'] ?? ''?>"/>')
})
- POC: Field_index.php?model_id=")
Field_index.php?back_url=")

AFFECTED VERSION:<= v1.3.20
感谢反馈,上述问题将于1.3.21版本修复。 Thank you, it will fix in v1.3.21