gateway-api
 gateway-api copied to clipboard
gateway-api copied to clipboard
Add a conformance Test for HTTPS listener with multiple TLS certs
What type of PR is this? /kind feature
What this PR does / why we need it: Add a conformance Test for HTTPS listener with multiple TLS certs
Which issue(s) this PR fixes:
Fixes #1330
Does this PR introduce a user-facing change?: NONE
The committers listed above are authorized under a signed CLA.
- :white_check_mark: login: ksankeerth / name: Shankeerthan Kasilingam (0ed6b4886e742bfb141c49fcba5b7eb212bad2bc)
Welcome @ksankeerth!
It looks like this is your first PR to kubernetes-sigs/gateway-api 🎉. Please refer to our pull request process documentation to help your PR have a smooth ride to approval.
You will be prompted by a bot to use commands during the review process. Do not be afraid to follow the prompts! It is okay to experiment. Here is the bot commands documentation.
You can also check if kubernetes-sigs/gateway-api has its own contribution guidelines.
You may want to refer to our testing guide if you run into trouble with your tests not passing.
If you are having difficulty getting your pull request seen, please follow the recommended escalation practices. Also, for tips and tricks in the contribution process you may want to read the Kubernetes contributor cheat sheet. We want to make sure your contribution gets all the attention it needs!
Thank you, and welcome to Kubernetes. :smiley:
Hi @ksankeerth. Thanks for your PR.
I'm waiting for a kubernetes-sigs member to verify that this patch is reasonable to test. If it is, they should reply with /ok-to-test on its own line. Until that is done, I will not automatically test new commits in this PR, but the usual testing commands by org members will still work. Regular contributors should join the org to skip this step.
Once the patch is verified, the new status will be reflected by the ok-to-test label.
I understand the commands that are listed here.
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository.
[APPROVALNOTIFIER] This PR is NOT APPROVED
This pull-request has been approved by: ksankeerth
Once this PR has been reviewed and has the lgtm label, please assign shaneutt for approval by writing /assign @shaneutt in a comment. For more information see:The Kubernetes Code Review Process.
The full list of commands accepted by this bot can be found here.
Approvers can indicate their approval by writing /approve in a comment
Approvers can cancel approval by writing /approve cancel in a comment
/ok-to-test
@tokers Thanks for your comments. I have fixed them. Will you be able to review the PR?
I am a bit confused. Multi certs are
Implementation-specificper the spec. How can we have a conformance tests for something Implementation-specific?
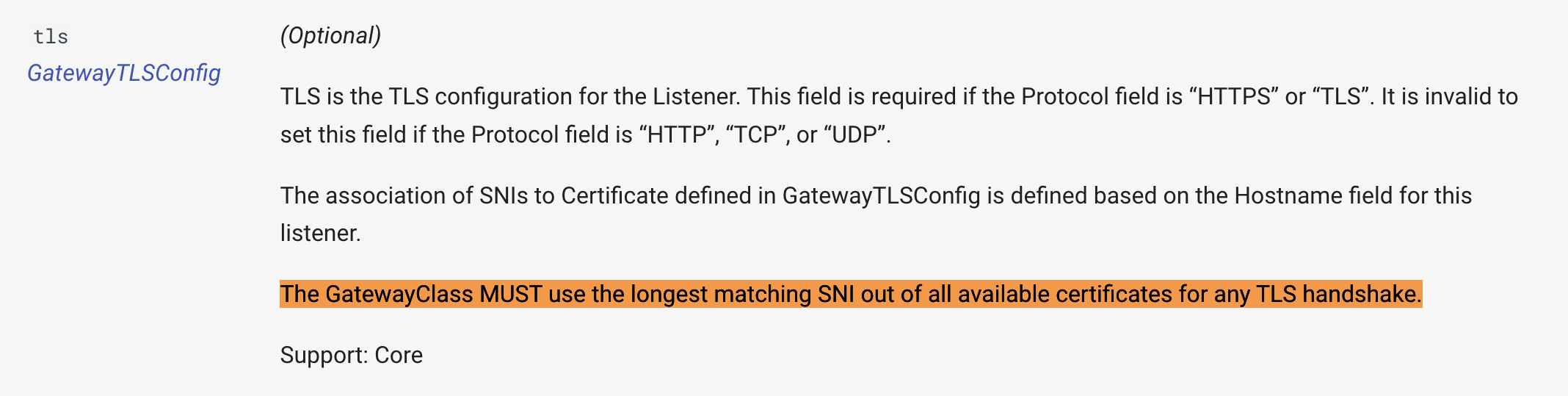
@howardjohn Not sure my understanding is correct. But in the document, It says when multiple certs are configured, GW should use the longest matching SNI. (It's under support: core). I think the longest SNI matching falls under support core but more than one secret refs fall under Implementation specific
https://gateway-api.sigs.k8s.io/references/spec/#gateway.networking.k8s.io/v1beta1.GatewayTLSConfig
But supporting multiple certs are under support: Implementation specific
Rebased
This feels like an example of the confusion described in https://github.com/kubernetes-sigs/gateway-api/issues/640 - we may need to revisit how support levels are specified here, and if some subset like "more than one Kubernetes Secret" should actually be Extended support with an opt-in conformance test like this, rather than entirely custom or implementation-specific.
@robscott This seems intended to address the conformance tests requested in https://github.com/kubernetes-sigs/gateway-api/issues/851#issuecomment-1201753415, thoughts on whether that GEP already covers the expected conformance sufficiently, or if we need further discussion on what level this should be?
Okay, @robscott, @shaneutt, and I discussed this one in triage, and we think that the right way forward here is a PR to move multiple certificates to Extended, then we can come back and get this one in.
/lifecycle frozen
@youngnick: The lifecycle/frozen label cannot be applied to Pull Requests.
In response to this:
Okay, @robscott, @shaneutt, and I discussed this one in triage, and we think that the right way forward here is a PR to move multiple certificates to Extended, then we can come back and get this one in.
/lifecycle frozen
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository.
@ksankeerth: PR needs rebase.
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository.
@ksankeerth it's been a bit since we've heard back from you, are you still able to continue with this PR?
@ksankeerth we haven't heard back from you in some time, we're going to mark this one as a draft for the time being since there's a few conflicts that need to be resolved. Let us know how we can help you if you're still interested in this one! And if you're not interested that's totally fine, just let us know and we'll unassign!
@shaneutt Apologies for the very late reply. I think there is some confusion in multi-tls support as Implementation specific.
https://github.com/kubernetes-sigs/gateway-api/pull/1526#discussion_r1019755797
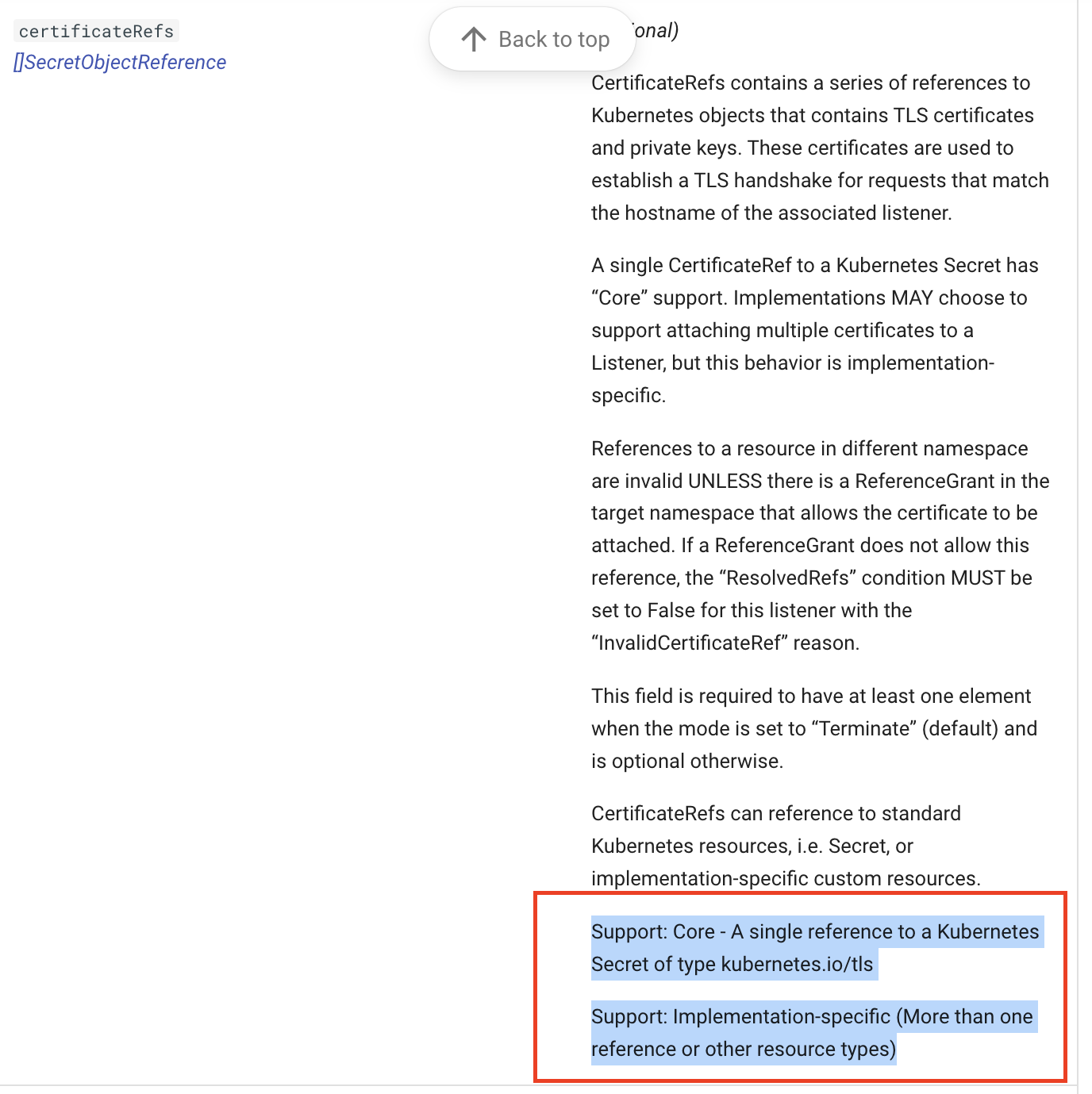
I think this is going to need some more discussion. If we say that supporting multiple TLS certificates is "Extended" support, we'll need to define how multiple TLS certs should be handled. I'm not entirely sure what that looks like today, but it could be worth getting some input from anyone currently supporting that.
One concrete change here would be to limit the scope of "Extended" support to Kubernetes TLS secrets. That would result in the following:
As per the doc,https://gateway-api.sigs.k8s.io/references/spec/#gateway.networking.k8s.io/v1beta1.Listener
TLS is the TLS configuration for the Listener. This field is required if the Protocol field is “HTTPS” or “TLS”. It is invalid to set this field if the Protocol field is “HTTP”, “TCP”, or “UDP”.
The association of SNIs to Certificate defined in GatewayTLSConfig is defined based on the Hostname field for this listener.
The GatewayClass MUST use the longest matching SNI out of all available certificates for any TLS handshake.
Support: Core
If GW has to support the longest SNI matching as core support, that indirectly means GWs have multiple certificates. However, support for multi-certificates is currently mentioned as Implementation specific. Later, I raised this PR to mark it as extended support. I believe there is no conclusion on that https://github.com/kubernetes-sigs/gateway-api/pull/1526. (Sorry If I missed any discussions on this)
"multiple certificates" feature is for multiple under a single Listener. I think the text you quoted is about having multiple by having N listeners with 1 certificate each
The Kubernetes project currently lacks enough contributors to adequately respond to all PRs.
This bot triages PRs according to the following rules:
- After 90d of inactivity,
lifecycle/staleis applied - After 30d of inactivity since
lifecycle/stalewas applied,lifecycle/rottenis applied - After 30d of inactivity since
lifecycle/rottenwas applied, the PR is closed
You can:
- Mark this PR as fresh with
/remove-lifecycle stale - Close this PR with
/close - Offer to help out with Issue Triage
Please send feedback to sig-contributor-experience at kubernetes/community.
/lifecycle stale
The Kubernetes project currently lacks enough active contributors to adequately respond to all PRs.
This bot triages PRs according to the following rules:
- After 90d of inactivity,
lifecycle/staleis applied - After 30d of inactivity since
lifecycle/stalewas applied,lifecycle/rottenis applied - After 30d of inactivity since
lifecycle/rottenwas applied, the PR is closed
You can:
- Mark this PR as fresh with
/remove-lifecycle rotten - Close this PR with
/close - Offer to help out with Issue Triage
Please send feedback to sig-contributor-experience at kubernetes/community.
/lifecycle rotten
The Kubernetes project currently lacks enough active contributors to adequately respond to all issues and PRs.
This bot triages PRs according to the following rules:
- After 90d of inactivity,
lifecycle/staleis applied - After 30d of inactivity since
lifecycle/stalewas applied,lifecycle/rottenis applied - After 30d of inactivity since
lifecycle/rottenwas applied, the PR is closed
You can:
- Reopen this PR with
/reopen - Mark this PR as fresh with
/remove-lifecycle rotten - Offer to help out with Issue Triage
Please send feedback to sig-contributor-experience at kubernetes/community.
/close
@k8s-triage-robot: Closed this PR.
In response to this:
The Kubernetes project currently lacks enough active contributors to adequately respond to all issues and PRs.
This bot triages PRs according to the following rules:
- After 90d of inactivity,
lifecycle/staleis applied- After 30d of inactivity since
lifecycle/stalewas applied,lifecycle/rottenis applied- After 30d of inactivity since
lifecycle/rottenwas applied, the PR is closedYou can:
- Reopen this PR with
/reopen- Mark this PR as fresh with
/remove-lifecycle rotten- Offer to help out with Issue Triage
Please send feedback to sig-contributor-experience at kubernetes/community.
/close
Instructions for interacting with me using PR comments are available here. If you have questions or suggestions related to my behavior, please file an issue against the kubernetes/test-infra repository.