Spoofing started, but no effect on target hosts
Checklist for submitting an issue to KickThemOut:
- [x] I have carefully read the README file and haven't managed to resolve my issue.
- [x] I have searched the issues of this repo and believe that this is not a duplicate.
- [x] I am running the latest version of KickThemOut.
- OS name & version: Linux Mint 19.3 Cinnamon (Linux Kernel 5.3.0-59-generic)
- Python version: Python 3.6.9
- Scapy version: Scapy 2.4.3
- Nmap version: Nmap 7.60
- Link of Gist: https://gist.github.com/reecewithnospoon/a851fe877eda77081a273d1af42e4ff5
- Description:
First of all, I just want to say I love this script, I used it frequently 2-3 years ago on a Kali Linux installation.
However, I have just installed it on my Linux Mint machine, followed all of the README instructions, and I'm successfully getting a list of hosts on my network - only, when I select targets and "spoofing started..." is displayed, nothing actually happens to the targets.
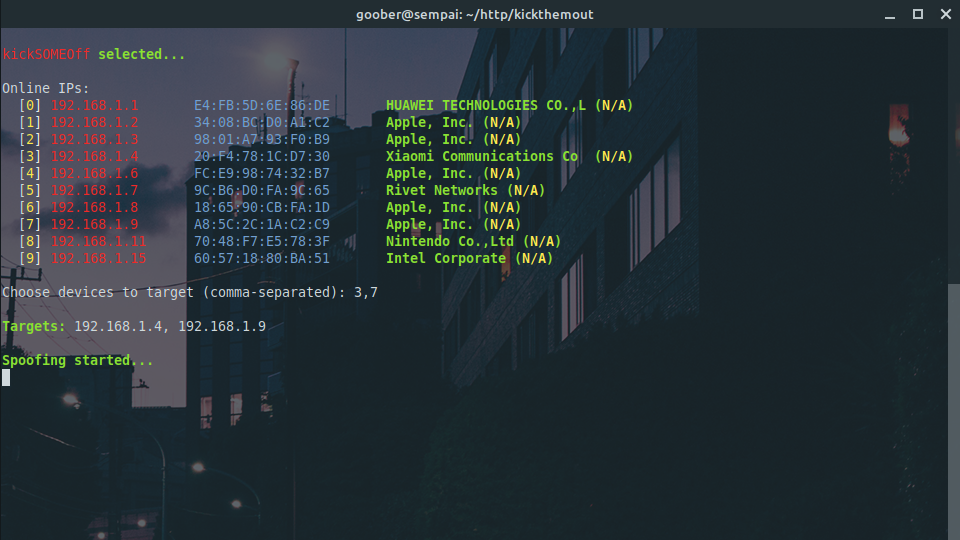
I can confirm this by targeting one of my own devices. Even after spoofing starts, the connection of the other device is undisturbed, and it can stream videos and browse websites as normal. When I used this script a few years ago, it successfully stopped the targets from receiving packets, and you could even stop everyone from reaching the internet by targeting all.
Regardless of whether it actually kicks people from the network (as it used to do years ago) I see that you have noted previously that the purpose of kickthemout is simply to give more bandwidth to the user. However, it doesn't even seem to be doing this.
Please note, this is a bare metal installation of Linux Mint, and I am not running a VM.
Hey @reecewithnospoon. Thank you for your support; it is much appreciated. Could you use a network analyzer such as Wireshark to check whether the ARP packets are being broadcasted? Thanks!
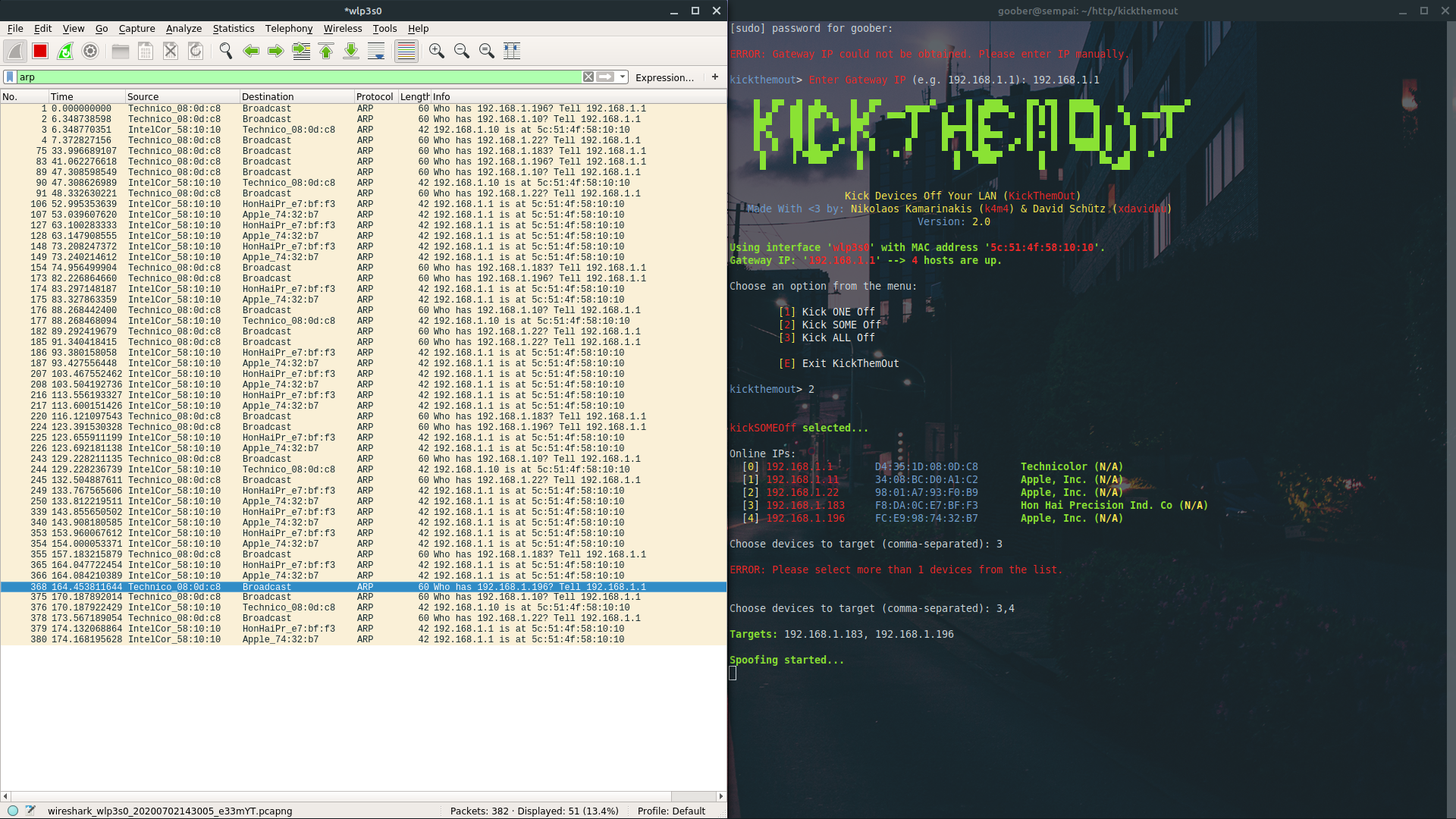
It looks like these are just regular ARP requests - as you can see from the time, they weren't occurring frequently.
Same, I have a mac Virtual Box on my PC but it doesn't tend to do any spoofing
k4m4 FIX THIS...... it doesnt work
same issue here