jupyterlab-google-drive
 jupyterlab-google-drive copied to clipboard
jupyterlab-google-drive copied to clipboard
Can JupyterLab get itself verified by Google to avoid a Security Checkup advisory?
I expect folks are already aware that JupyterLab's Google Drive integration triggers a "Security Checkup" advisory from Google. Is there someway to help Google "verify" Jupyter's "developer's information"?
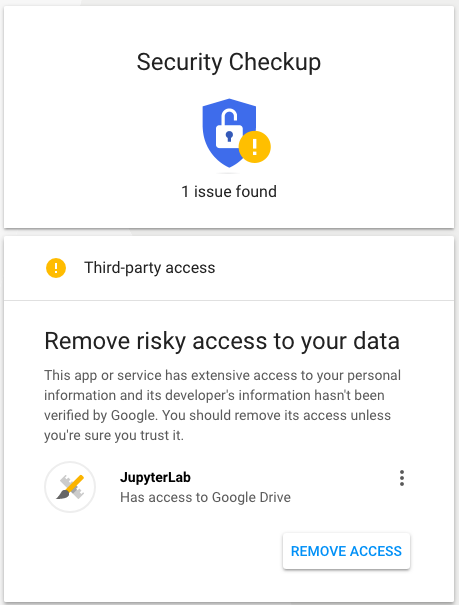
Yeah, a week or two ago Google increased their verification requirements for existing applications. Even worse, new users can't log in using the default CLIENT_ID at all right now.
Unfortunately, I think we can't get verified by them: part of the verification procedure involves actually demonstrating that you own the URL that is used to access Google Drive. Since the default credentials are keyed to localhost, it is not really possible to demonstrate that it really is JupyterLab that is trying to access a user's account.
Ultimately, that is probably correct (it would be quite easy for somebody malicious to impersonate JupyterLab), but it certainly makes things more difficult at the moment. I think the way forwards us probably to recommend that new users/deployments make their own credentials, rather than distributing a default set that are easy to impersonate.
What do you think @danielballan? As part of this, I'd like to make sure that the instructions for setting up your own credentials are as explicit and simple as possible, so I'd particularly be interested in your feedback there.
Just tried to connect to GDrive from my Jupyterlab server (SciPy'18 sprints!), and it throws a more nasty error than @danielballan observed:
 I thought I'll leave this comment here to keep everyone in the loop.
I thought I'll leave this comment here to keep everyone in the loop.
Have you guys seen https://github.com/gsuitedevs/PyDrive? Maybe useful, but requires user's credentials in a local file ~/.config/client_secrets.json obtained via https://console.cloud.google.com/.
I think the way forwards us probably to recommend that new users/deployments make their own credentials, rather than distributing a default set that are easy to impersonate. What do you think @danielballan? As part of this, I'd like to make sure that the instructions for setting up your own credentials are as explicit and simple as possible, so I'd particularly be interested in your feedback there.
Sorry for the long lag -- I'm digging myself out of GH notification bankruptcy. :-D
Yes, I think that's a good approach and would be happy to review/coauthor documentation on this.
Hi @danielballan, thanks for the input. I have made a first pass at making the instructions for creating your own credentials more prominent, but it could probably use more work. If you have any suggestions, I'd love to hear them.
Thanks, @ian-r-rose. I went looking for those instructions and I found this PR which looks relevant but possibly too old for be what you are talking about here. Can you point me in the right direction?