jfinal_cms
 jfinal_cms copied to clipboard
jfinal_cms copied to clipboard
jfinal cms是一个java开发的功能强大的信息咨询网站,采用了简洁强大的JFinal作为web框架,模板引擎用的是beetl,数据库用mysql,前端bootstrap框架。支持oauth2认证、帐号注册、密码加密、评论及回复,消息提示,网...
Administrator login is required. The default account password is admin:admin123 ## admin/videoalbum/list There is a SQLI vul in background mode.The route is as following 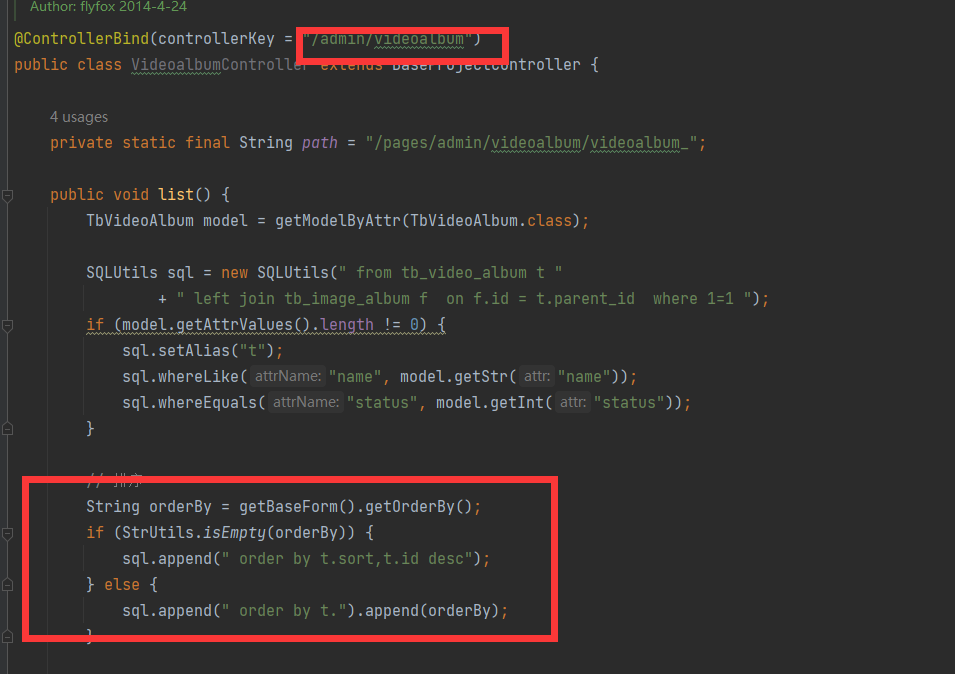 vulnerable argument passing is as...
Administrator login is required. The default account password is admin:admin123 ## admin/article/list There is a SQLI vul in background mode.The route is as following  vulnerable argument passing is as...
first you can use the URL http://your IP/jfinal_cms/system/menu/list then you can use the shell ''' sqlmap -u http://your IP/jfinal_cms/system/menu/list --thread 8 --batch --smart --random-agent --data "form.orderColumn=*&form.orderAsc=&attr.name=&totalRecords=31&pageNo=1&pageSize=20&length=10" --cookie "your cookie" '''...
you can use the route /jfinal_cms/system/role/list then use sqlmap attack the interface like this : 
the route is /jfinal_cms/system/user/list   
CVE-2022-33113 - Jfinal CMS v5.1.0 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the keyword text field under the publish blog module. ---------...
Description: Jfinal CMS v5.1.0 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the keyword text field under the publish blog module. Fixed in...
There is a stored XSS vulnerability in JFinal_cms 's publish blog module. An attacker could insert malicious XSS code into the content of the blog post. When users and administrators...
There is a stored XSS vulnerability in JFinal_cms 's publish blog module. An attacker could insert malicious XSS code into the post title. When users and administrators view the blog...
There is a stored XSS vulnerability in JFinal_cms 's publish blog module. An attacker can insert malicious XSS code into the keyword field. When the user views the content of...
