[JENKINS-76080] webhook response: HTTP ERROR 400 No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility).
HTTP ERROR 400 No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility).
| URI: | /github-webhook/ |
|---|---|
| STATUS: | 400 |
| MESSAGE: | No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility). |
| SERVLET: | Stapler |
Powered by Jetty:// 12.0.22
Â
Originally reported by claus_lee, imported from: webhook response: HTTP ERROR 400 No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility).
- assignee:
 lanwen
lanwen
- status: Open
- priority: Minor
- component(s): github-plugin
- resolution: Unresolved
- votes: 1
- watchers: 6
- imported: 2025-12-08
Raw content of original issue
<html>
<head>
<meta http-equiv="Content-Type" content="text/html;charset=ISO-8859-1"/>
<title>Error 400 No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility).</title>
</head>
<body><h2>HTTP ERROR 400 No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility).</h2>
<table>
<tr><th>URI:</th><td>/github-webhook/</td></tr>
<tr><th>STATUS:</th><td>400</td></tr>
<tr><th>MESSAGE:</th><td>No valid signature found. Ensure webhook is configured with a supported signature algorithm (SHA-256 recommended, SHA-1 for legacy compatibility).</td></tr>
<tr><th>SERVLET:</th><td>Stapler</td></tr>
</table>
<hr/><a href="https://jetty.org/">Powered by Jetty:// 12.0.22</a><hr/>
Â
</body>
</html>
1 attachment
 clementvalot:
clementvalot:
- Original comment link
Raw content of original comment:
It seems like, since a recent update, Jenkins responds with error 400 when a secret is not provided in the GitHub hook. Adding a secret circumvents this issue.
I couldn't find anything related to this in the release notes so it feels like a regression
It seems like, since a recent update, Jenkins responds with error 400 when a secret is not provided in the GitHub hook. Adding a secret circumvents this issue.
I couldn't find anything related to this in the release notes so it feels like a regression
wavded:
- Original comment link
Raw content of original comment:
I am encountering the same issue. Trying to workaround it but not having any luck. I use the github branch plugin, all incoming webhooks are 400s for me with that error page.
I am encountering the same issue. Trying to workaround it but not having any luck. I use the github branch plugin, all incoming webhooks are 400s for me with that error page.
wavded:
- Original comment link
Raw content of original comment:
I was looking in the wrong spot. I had to update the Github -> Advanced -> Shared Secret field in global configuration.
I was looking in the wrong spot. I had to update the Github -> Advanced -> Shared Secret field in global configuration.
 timja:
timja:
- Original comment link
Raw content of original comment:
Likely caused by https://github.com/jenkinsci/github-plugin/pull/438
Likely caused by https://github.com/jenkinsci/github-plugin/pull/438
 hybridprogrammer:
hybridprogrammer:
- Original comment link
Raw content of original comment:
According to the Github docs the X-Hub-Signature headers should only be sent when the webhook contains a secret. I was only able to recreate the error when the payload contained X-Hub-Signature headers and a Github -> Advanced -> Shared Secret settings existed with no shared secret set, see screen shot. This would be an invalid configuration.
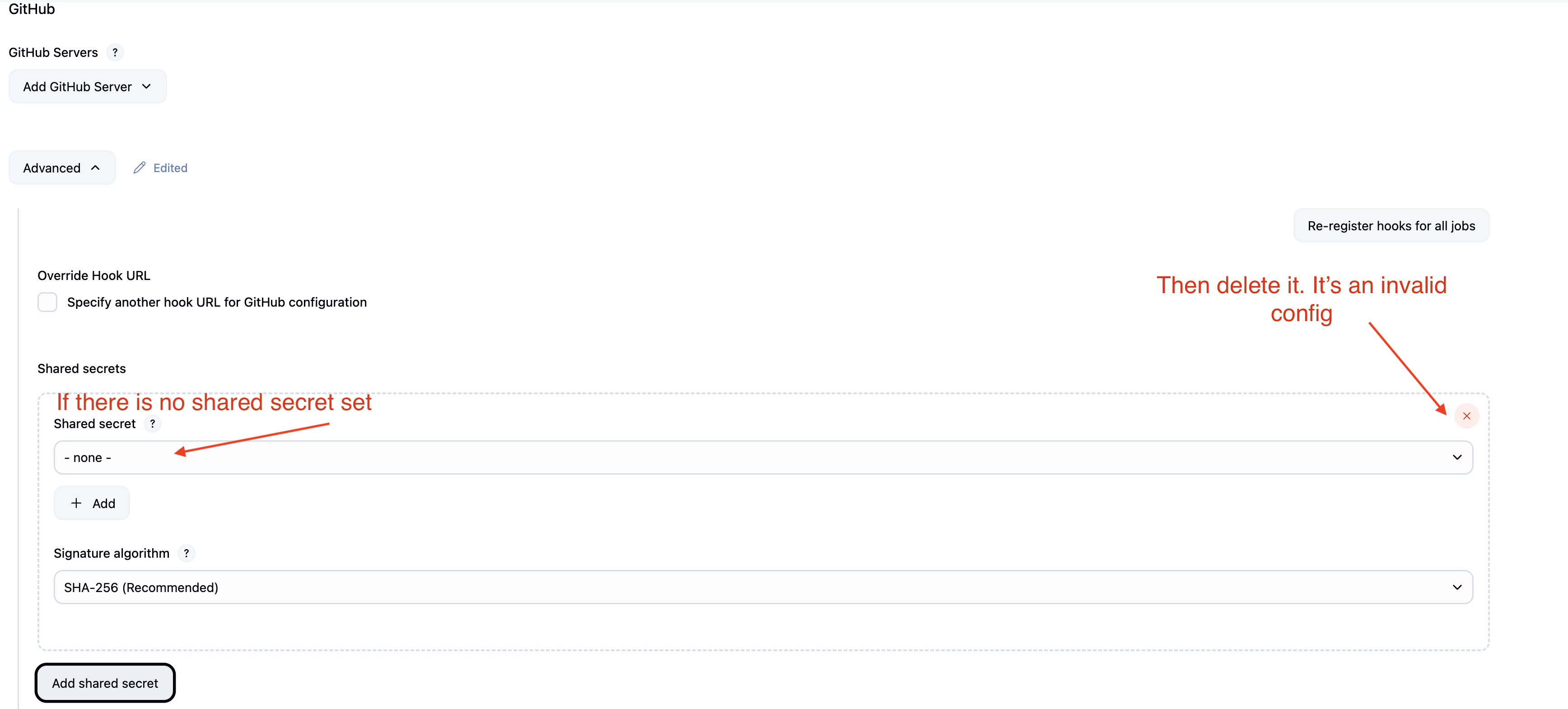
The other option is to configure a shared secret by creating a random secure string by clicking the Add button and choosing Jenkins Credential. Domain: Global Credentials, Kind: Secret Text. Put your secure string in the Secret field and assign it an ID and Description. The description is what is displayed in the drop down menu above when you select the shared secret.
After you add the secret you need to update your webhook config on github's side.
According to the Github docs the X-Hub-Signature headers should only be sent when the webhook contains a secret. I was only able to recreate the error when the payload contained X-Hub-Signature headers and a Github -> Advanced -> Shared Secret settings existed with no shared secret set, see screen shot. This would be an invalid configuration.
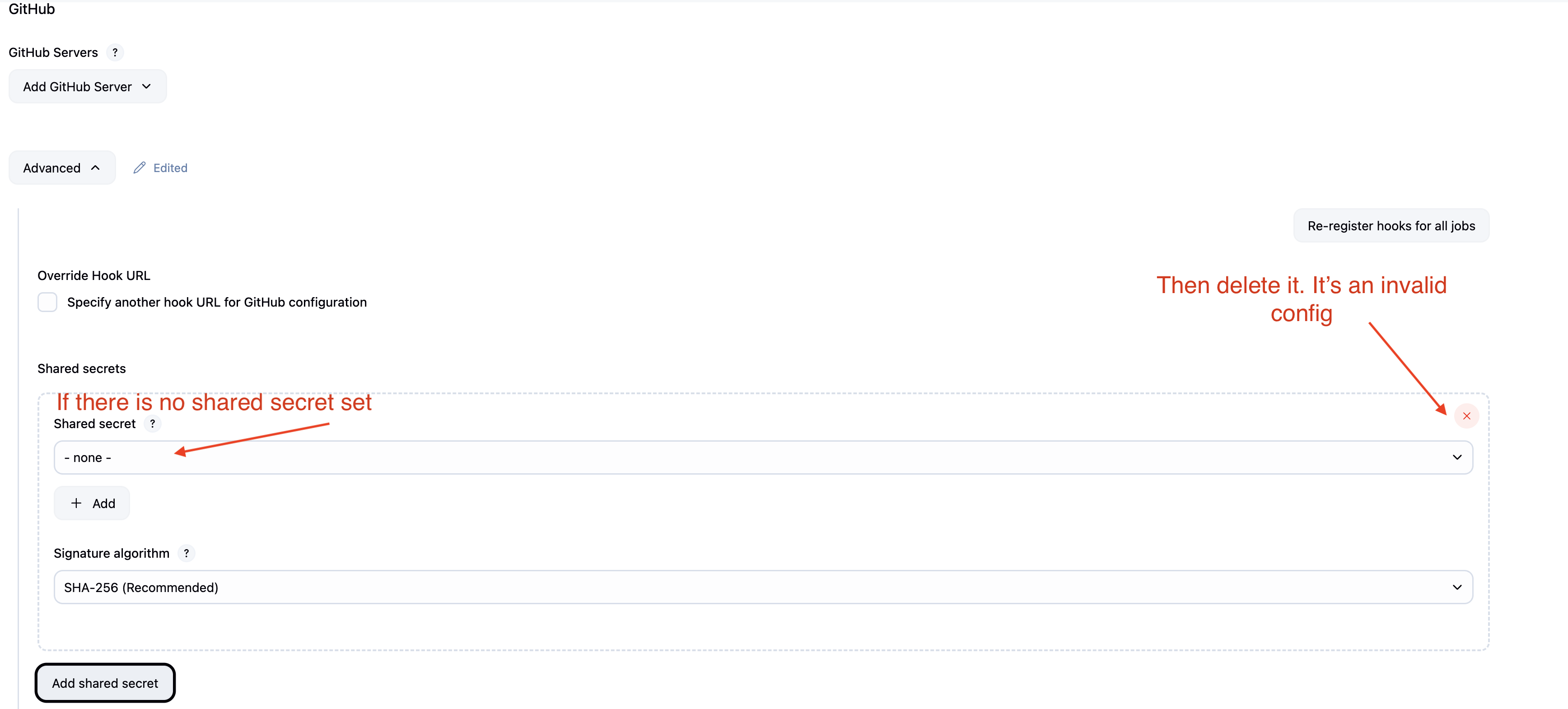
The other option is to configure a shared secret by creating a random secure string by clicking the Add button and choosing Jenkins Credential. Domain: Global Credentials, Kind: Secret Text. Put your secure string in the Secret field and assign it an ID and Description. The description is what is displayed in the drop down menu above when you select the shared secret.
After you add the secret you need to update your webhook config on github's side.