userscripts
 userscripts copied to clipboard
userscripts copied to clipboard
CSP fallback doesn't work since Safari 16 upgrade
On both my Twitter userscript, and the sample userscript given in this template, the CSP fallback no longer works — it seems because the effectiveDirective has changed from script-src to script-src-elem:
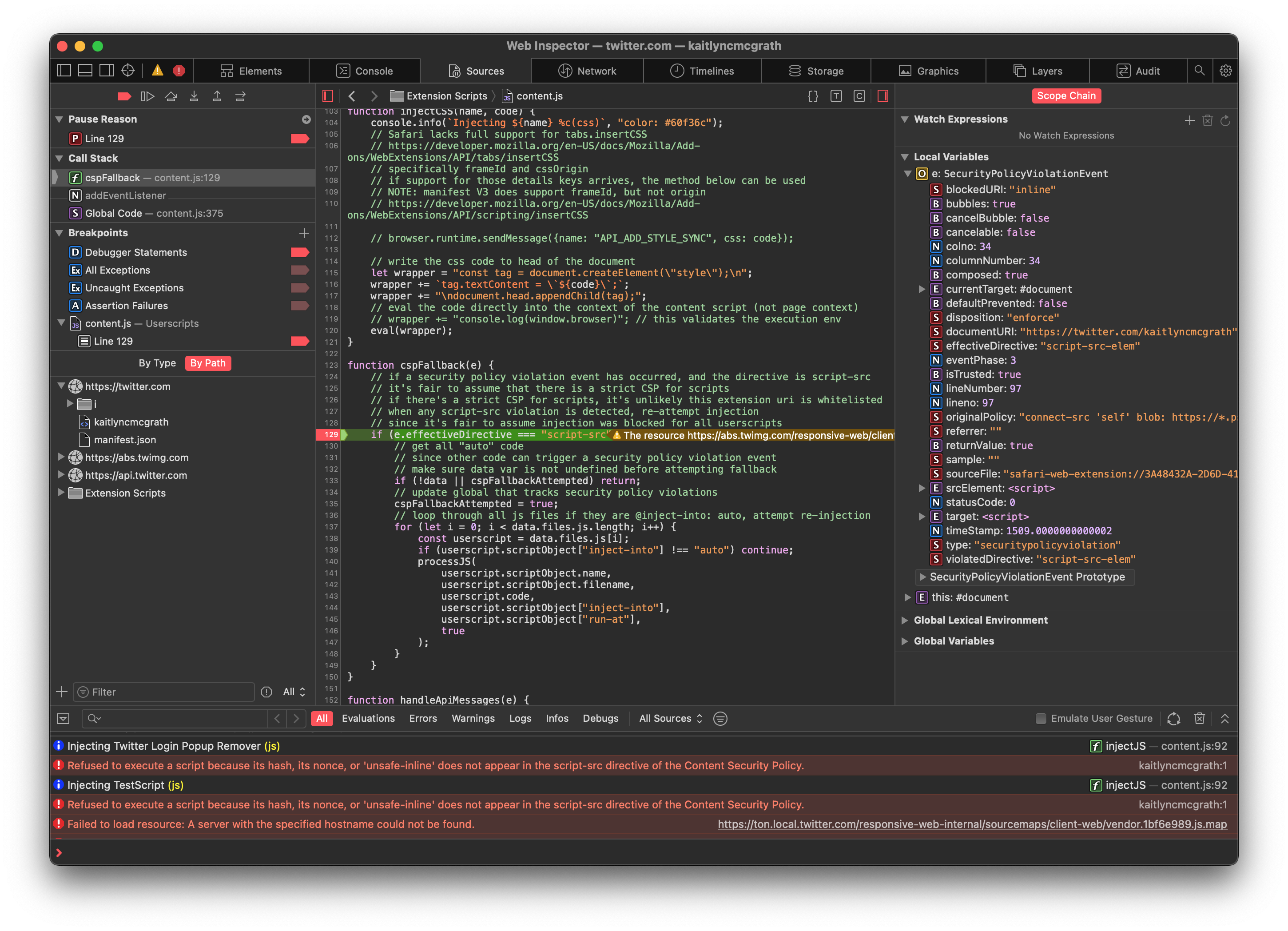
I admit I don't know CSP basically at all, but the MDN documentation seems to suggest that script-src-elem falls back to script-src, so maybe a simple extra if condition in content.js would fix it?
This is Twitter's CSP for me:
Content-Security-Policy: connect-src 'self' blob: https://*.pscp.tv https://*.video.pscp.tv https://*.twimg.com https://api.twitter.com https://api-stream.twitter.com https://ads-api.twitter.com https://aa.twitter.com https://caps.twitter.com https://pay.twitter.com https://sentry.io https://ton.twitter.com https://twitter.com https://upload.twitter.com https://www.google-analytics.com https://accounts.google.com/gsi/status https://accounts.google.com/gsi/log https://app.link https://api2.branch.io https://bnc.lt wss://*.pscp.tv https://vmap.snappytv.com https://vmapstage.snappytv.com https://vmaprel.snappytv.com https://vmap.grabyo.com https://dhdsnappytv-vh.akamaihd.net https://pdhdsnappytv-vh.akamaihd.net https://mdhdsnappytv-vh.akamaihd.net https://mdhdsnappytv-vh.akamaihd.net https://mpdhdsnappytv-vh.akamaihd.net https://mmdhdsnappytv-vh.akamaihd.net https://mdhdsnappytv-vh.akamaihd.net https://mpdhdsnappytv-vh.akamaihd.net https://mmdhdsnappytv-vh.akamaihd.net https://dwo3ckksxlb0v.cloudfront.net https://media.riffsy.com https://*.giphy.com https://media.tenor.com https://c.tenor.com ; default-src 'self'; form-action 'self' https://twitter.com https://*.twitter.com; font-src 'self' https://*.twimg.com; frame-src 'self' https://twitter.com https://mobile.twitter.com https://pay.twitter.com https://cards-frame.twitter.com https://accounts.google.com/ https://client-api.arkoselabs.com/ https://iframe.arkoselabs.com/ https://recaptcha.net/recaptcha/ https://www.google.com/recaptcha/ https://www.gstatic.com/recaptcha/; img-src 'self' blob: data: https://*.cdn.twitter.com https://ton.twitter.com https://*.twimg.com https://analytics.twitter.com https://cm.g.doubleclick.net https://www.google-analytics.com https://maps.googleapis.com https://www.periscope.tv https://www.pscp.tv https://media.riffsy.com https://*.giphy.com https://media.tenor.com https://c.tenor.com https://*.pscp.tv https://*.periscope.tv https://prod-periscope-profile.s3-us-west-2.amazonaws.com https://platform-lookaside.fbsbx.com https://scontent.xx.fbcdn.net https://scontent-sea1-1.xx.fbcdn.net https://*.googleusercontent.com https://imgix.revue.co; manifest-src 'self'; media-src 'self' blob: https://twitter.com https://*.twimg.com https://*.vine.co https://*.pscp.tv https://*.video.pscp.tv https://dhdsnappytv-vh.akamaihd.net https://pdhdsnappytv-vh.akamaihd.net https://mdhdsnappytv-vh.akamaihd.net https://mdhdsnappytv-vh.akamaihd.net https://mpdhdsnappytv-vh.akamaihd.net https://mmdhdsnappytv-vh.akamaihd.net https://mdhdsnappytv-vh.akamaihd.net https://mpdhdsnappytv-vh.akamaihd.net https://mmdhdsnappytv-vh.akamaihd.net https://dwo3ckksxlb0v.cloudfront.net; object-src 'none'; script-src 'self' 'unsafe-inline' https://*.twimg.com https://recaptcha.net/recaptcha/ https://www.google.com/recaptcha/ https://www.gstatic.com/recaptcha/ https://client-api.arkoselabs.com/ https://www.google-analytics.com https://twitter.com https://app.link https://accounts.google.com/gsi/client https://appleid.cdn-apple.com/appleauth/static/jsapi/appleid/1/en_US/appleid.auth.js 'nonce-ZTRhNjk1MDQtZDQ4Ni00MTMyLTg2YmItMWFlODBmOTE1ZWE1'; style-src 'self' 'unsafe-inline' https://accounts.google.com/gsi/style https://*.twimg.com; worker-src 'self' blob:; report-uri https://twitter.com/i/csp_report?a=O5RXE%3D%3D%3D&ro=false
System Information:
macOS or iOS version: macOS 11.7 Userscripts version: Userscripts Safari Version 4.2.3 (59) Safari version: Version 16.0 (16614.1.25.9.10, 16614) Is this issue related to script injection? Yes, sort of Did the test script (pasted above) successfully run on your machine? Nope
@joedrew thanks for reporting this
seems to suggest that script-src-elem falls back to script-src, so maybe a simple extra if condition in content.js would fix it?
That sounds like it can work
Also if you could share a simplified example of the userscript that is failing that would be useful. I really just need the metadata, so the content of the code could be a simple console.log statement.
Yep, this one fails:
// ==UserScript==
// @name TestScript
// @description This is your new file, start writing code
// @match <all_urls>
// @exclude-match *://*.google.com/*
// @noframes
// ==/UserScript==
console.log(`This is a test script - ${window.location.href}`);
(Note that I'm going to any random Twitter page, e.g. https://twitter.com/drewgrof, while logged out.)
should be resolved in https://github.com/quoid/userscripts/commit/ad38891a1d70c43f2358e134473efd5ee83c5eb6