userscripts
 userscripts copied to clipboard
userscripts copied to clipboard
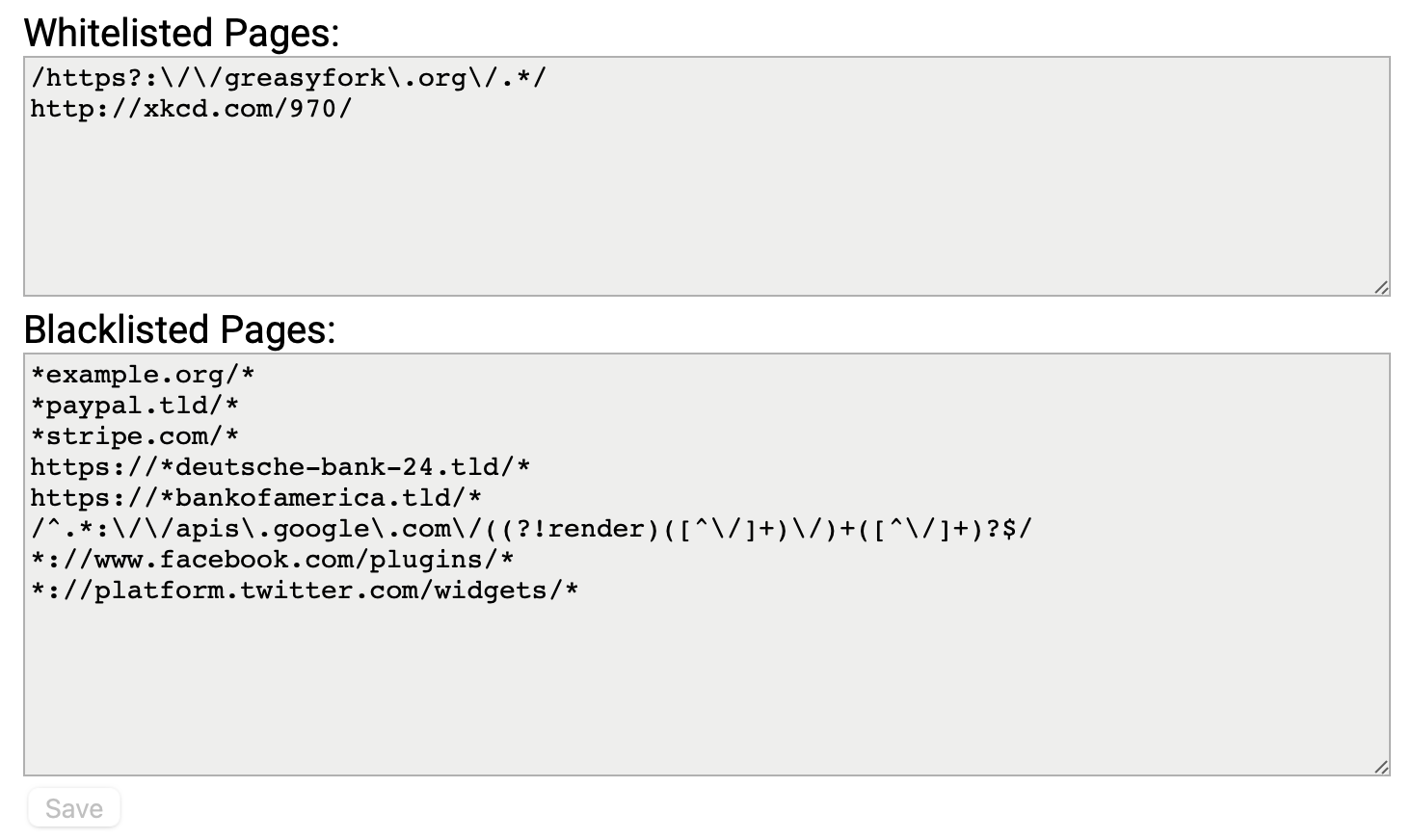
Clarify acceptable blacklist values
System Information:
macOS version:
12.4 (21F79)
Userscripts version:
Userscripts Safari Version 4.2.0 (52)
Safari version:
Version 15.5 (17613.2.7.1.8)
Is this issue related to script injection?:
not sure, probably
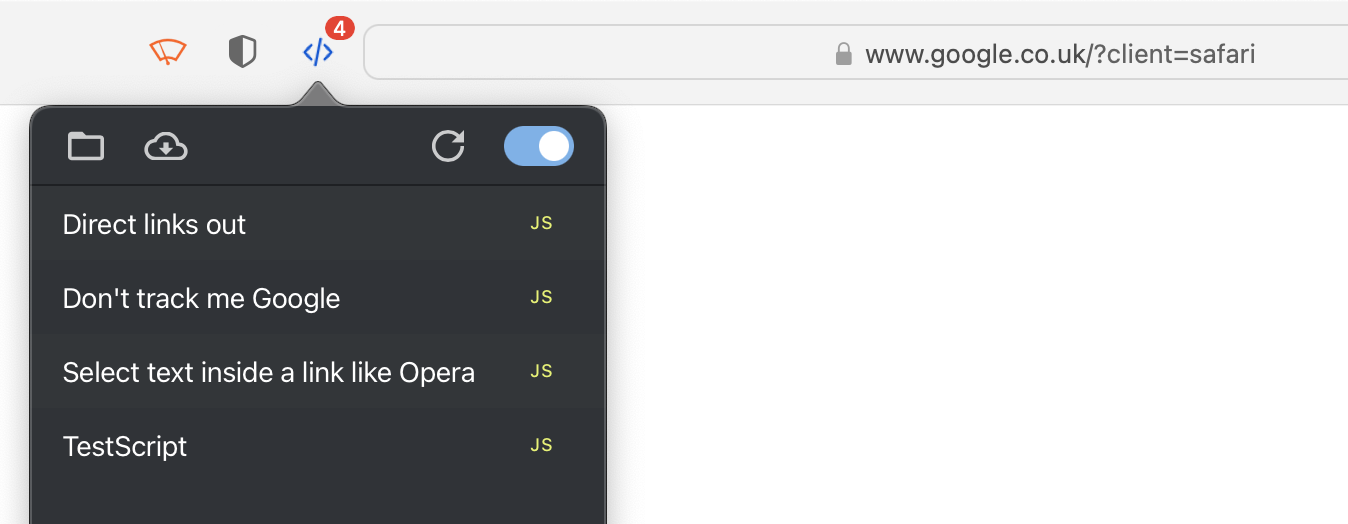
Did the test script (pasted above) successfully run on your machine?
Yes, here's the output: "This is a test script - https://www.google.co.uk/?client=safari"
Bug description:
When I go to https://www.google.co.uk or https://my.internet.banking.com , userscripts ignore Global Blacklist setting and continue to run on blacklisted domains.
My Global Blacklist setting: google.co.uk, *google.co.uk/*, *.co.uk, *.co.uk/*, *.co.uk*, my.internet.banking.com
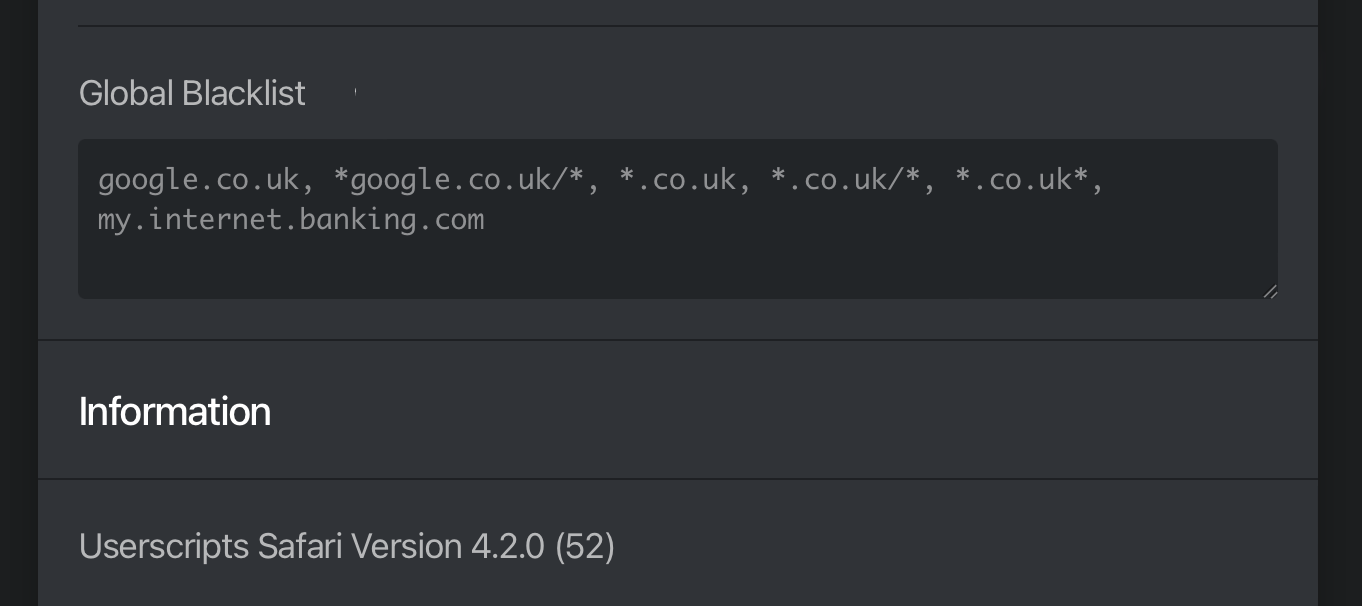
Expected behaviour: no scripts should be run / executed on any page/domain/url that matches the global blacklist.
Actual behaviour: all scripts ignore the "global blacklist" setting and continute to run there, introducing potential security issue.
@alfuken
It looks like you are using invalid match patterns
The readme should probably clarify that patterns in the blacklist must abide by the rules as @match and regex (@include) patterns aren't valid.
@quoid
I think maybe you should put the readme hash link next to that setting, as I believe most users (non-scripters) are not familiar with it. In fact, many user script authors also get the syntax of @match wrong, they misunderstand @match metadata or confuse it with @include, so we may need to indicate its syntax documentation more prominently.
As an enhancement and a friendlier measure, perhaps we can also use a script to check the input box that is about to be saved and prompt the user whether the input is valid.
@ACTCD good ideas
I updated the title of this issue to better reflect what needs to be done
The readme should probably clarify that patterns in the blacklist must abide by the rules as
@matchand regex (@include) patterns aren't valid.
Not only readme, but in UI as well.
Thanks for clarifying it, guys. Using that reference to @match spec I got it working alright. But I hope you can imagine the shock I had when it did not work at first, especially considering that there is no indication whatsoever that I'm doing it wrong ;)
Could be a good idea to include some example blacklist values, like Tampermonkey does: