meilisearch-migration
 meilisearch-migration copied to clipboard
meilisearch-migration copied to clipboard
Retrieve current version of Meilisearch doesn't work when no key is provided
Description
To update Meilisearch with this script, it needs to get the current version of the instance. It does this through a query and a cut command:
current_meilisearch_version=$(
curl -X GET 'http://localhost:7700/version' --header "Authorization: Bearer $MEILISEARCH_MASTER_KEY" -s --show-error |
cut -d '"' -f 12
)
Expected behavior The version must be retrieved in this format: X.X.X, even if no API key is provided (given that the current Meilisearch is running without a master key)
Current behavior
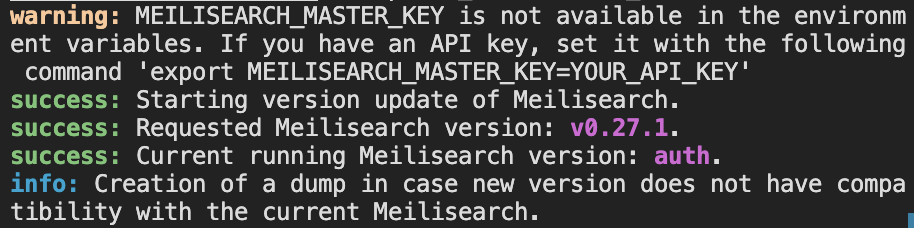
The script works fine when a MEILISEARCH_MASTER_KEY is set, but when no master key is specified, the script does not work:
Screenshots or Logs
Seconded. I don't want all my browsing traffic going through Google-controlled servers. I certainly don't want it to "initially" be an option followed by "later" being a requirement or even a default.
This doesn't have anything to do with security. This is all about control, harvesting data, and ensuring Google's position as the advertising leader on the internet.
I feel as if Google is literally taunting policy makers, politicians, privacy groups. How could such an inane thought process, be exhibited?
This demonstrates how out of touch Google is, or alternatively, its sheer audacity. Google is the single greatest threat to privacy that has ever existed. Ever.
Insane!
This, in it's entirety, should be shut down today. I will be writing the FCC about this as well.
Make sure you report this repo as a phishing kit to Github, because that's exactly what it is: google's phishing kit.
Hi folks, thanks for your input. This feature tunnels traffic through two proxies (one run by Google, one by another company). That ensures that Google cannot see browsing data even if it were logging data on the proxy - which it isn't. All traffic is encrypted onion-style between Chrome and the proxies, so the Google proxy has no information about what websites are being browsed. Additionally, we're using blinded authentication tokens to minimize access to user identifiers at the proxies. So to recap, all the Google proxy can see is that an unknown client at a specific IP is using the proxy system. No information about websites visited or ads loaded is available.
Even after having read the above comment by @DavidSchinazi , as they say, the devil is in the details. Unless there is a way to see exactly what the agreement is between Google and the intermediary, both legal (hah) and technical (hahahahaha), and how it is enforced (rofl), its just PR-speak.
As @dfskoll has already pointed out, there will be no way, for an unsuspecting user, to know Google has not MITM'd a connection.
Lets ignore the technical details for a bit and see where this leads: with this feature, google will have a veto on anyone building a competing tracking system.
-- written in FF
I'm not buying @DavidSchinazi's comment.
Even if you provided public copies of the contracts and signed assurances, I still don't want my data going through those servers.
"Trust us" is "black box" security.
Regardless, the first hop is always going to know who I am. I don't care if it gets obfuscated by multiple hops only knowing the IP of the previous proxy.
See also Apple's two-hop proxy feature: https://support.apple.com/en-us/102602.
A few comments on some previous comments:
- I don't trust Apple either.
- However, to my knowledge, Apple does not have a business unit that generates profits by collecting data on its users and supplying it to advertisers. If anyone is looking for an anti-trust reason to break up Google, this feature in Chrome would be Exhibit A.
- If Google really cared about privacy, it would make Chrome directly support TOR and let users enable it if they wished, using the existing TOR infrastructure that is not under Google's control.
That ensures that Google cannot see browsing data
If the first proxy is owned by Google, it ensures no such thing. If the second proxy is owned by Google, it also ensures no such thing.
Either proxy can MITM the connection. And also, who is the "other company" and why should we trust it?
@DavidSchinazi - Stop. Implementing. Moats. For. Google's. Ad. Business. This is not a privacy feature, this is anticompetitive BS.
All traffic is encrypted onion-style between Chrome and the proxies, so the Google proxy has no information about what websites are being browsed.
- Law enforcement has entered the chat
So you're saying if Google received a subpoena because someone was browsing child pornography, there's no way you could/would assist law enforcement?
Yeah, right.
So you're saying if Google received a subpoena because someone was browsing child pornography, there's no way you could/would assist law enforcement?
Not that that's acceptable, and law enforcement should be involved.
But it starts the slippery slope. Getting traffic when a murder happens is also probably a good thing.
Hey--let's also go after people who skip child support.
Then it's people who drive more than 5 MPH over the speed limit.
If the tool is there, governments will start out by saying they will only use it to catch the "worst of the worst"...and over time they'll keep moving the goalposts.
EDIT: I mean...anyone remember when you could order a rifle from a mail-order catalog? You certainly can't do that in the US now.
To address some of the technical points made here:
- Neither proxy can MITM the client-origin connection because that connection uses TLS/QUIC end-to-end. These properties come from the WebPKI and are independent of the IP Protection feature. The certificate in use is visible from the Chrome UI, and so is the list of root certificate authorities.
- Google isn't able to trace a given connection back to a user as the information just isn't there. That's true regardless of who would want to do it.
- Neither proxy can MITM the client-origin connection because that connection uses TLS/QUIC end-to-end. These properties come from the WebPKI and are independent of the IP Protection feature. The certificate in use is visible from the Chrome UI, and so is the list of root certificate authorities.
Google owns Chrome and Google owns the proxy. There's an inherent conflict there. If Google wanted to, it could make the Chrome UI say anything it chooses.
- Google isn't able to trace a given connection back to a user as the information just isn't there. That's true regardless of who would want to do it.
Google can determine the original IP, which is what this whole thing is supposed to hide.
Why do not not simply add support for TOR directly into Chrome and leave it at that? Then people who want to hide their IP can just enable TOR.
@DavidSchinazi would it be possible to have a more technical spec with Diagrams of what your planning traffic routing decision tree for one would be nice.
- How would a user know if traffic is or is not being proxied.
- Following up on this point how would one know if Google or it's partners are stopping traffic to a site or url?
- Who would have say on who is or is not allowed to see something?
- How will a company know
- How would complaints be handled SLA, decision body, etc.
I personally have many reservations on this giving Google this much control on a user and it's data is not my cup of tea. As honest as the teams/individual think they are being, Google is not known to play with things that are not in there interest. So I will ask the dumbest question I know will be ignored if we are planning to cut tracking and identification how will ad-sense work from that point on because we said Google will not be tracking users.
All traffic is encrypted onion-style between Chrome and the proxies, so the Google proxy has no information about what websites are being browsed.
Please do not try to imply that this has anything to do with Tor. There's a reason why Tor makes a random selection of hops, and doesn't just route everything through two big servers 'run by independent organizations'. This approach is absolutely not equivalent to that.
Google owns Chrome. So what's to prevent it from installing its own root certificate and MITMing all of your web browsing?
What's to prevent it from doing literally anything? Why MITM when the browser itself can just steal all your data itself?
What's to prevent it from doing literally anything? Why MITM when the browser itself can just steal all your data itself?
Nothing, I guess. I'm coming around to the belief that this technology is mostly to give Google a monopoly on tracking and making it harder for anyone else to compete.
(Though, getting data via a proxy makes it harder to detect something nefarious. If the browser were exfiltrating data to Google during normal browsing, the unusual traffic would be detectable.)
Google tried to undermine the users privacy way too often in the past years - always pretending to protect users.
To give you an incomplete list:
- Privacy Sandbox (exclusive access to tracking for google)
- Manifest V3 (severely disabling adblockers)
- FLoC (getting data for targeting directly on your machine)
- Web Environment Integrity (block site access if adblockers are in use)
- Device Integrity Attestation
Also noticing the additional force youtube put up in the fight against adblockers, it's pretty clear where this is going to: More ads, less blocking, more insights and control of the user. And everything exclusively for google.
You lost my trust when you removed "Don't be evil" from your code of conduct.
This proposal has way too many possibilities for abuse. You should bury it.
Wait until Google throttles the traffic through it's proxy that it deems to be "misinformation" like it did with YouTube during Covid or damaging to it's bottom line.
Time to use a different browser and deGoogle the environment. Enough monopoly.
Chrome, YouTube, Android, Gmail... Got to find alternatives now.
Wait until Google throttles the traffic through it's proxy that it deems to be "misinformation" like it did with YouTube during Covid or damaging to it's bottom line.
Good point but wait! Doesn't this mean that the American government can now access people's traffic legally using the very Patriot Act?
Regardless of where this data is going or coming from (even globally), now you're going through Google's server which means more US government control over the entire world.
I think everyone should start using other Br~~ave~~owsers and other networks ~~⊥0Я~~