terraform-github-actions
 terraform-github-actions copied to clipboard
terraform-github-actions copied to clipboard
Terraform apply not working as intended.
I've been running with
name: Terraform Plan
on: [pull_request]
jobs:
plan:
runs-on: ubuntu-latest
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
AWS_ACCESS_KEY_ID: ${{ secrets.ACCESS_KEY_ID }}
AWS_SECRET_ACCESS_KEY: ${{ secrets.SECRET_ACCESS_KEY }}
steps:
- name: Checkout
uses: actions/checkout@v2
- name: terraform plan
uses: dflook/terraform-plan@v1
env:
TERRAFORM_HTTP_CREDENTIALS: credentials here
with:
path: .
which seems to work just fine.
However, with the apply, the terraform http_credentials seems to fail with the following message:
No matching credentials found in TERRAFORM_HTTP_CREDENTIALS for
│ github.com/SomeModule.git
Based on this code:
name: Terraform Apply
on: [issue_comment]
jobs:
apply:
if: ${{ github.event.issue.pull_request && contains(github.event.comment.body, 'terraform apply') }}
runs-on: ubuntu-latest
name: Apply terraform plan
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
AWS_ACCESS_KEY_ID: ${{ secrets.ACCESS_KEY_ID }}
AWS_SECRET_ACCESS_KEY: ${{ secrets.SECRET_ACCESS_KEY }}
steps:
- name: Checkout
uses: actions/checkout@v2
with:
ref: refs/pull/${{ github.event.issue.number }}/merge
- name: terraform apply
uses: dflook/terraform-apply@v1
env:
TERRAFORM_HTTP_CREDENTIALS: github.com/samecredentials
with:
path: .
damn formatting
In a perfect world i'd like to:
- Have one workflow that runs validate and makes a plan to see if it works. If it works, i should be able to comment "terraform apply" but ONLY if the PR is approved by someone..
Removing the if statement and the name "apply terraform plan" makes it work...
Hello @MatiasNielsen, do you no longer get an TERRAFORM_HTTP_CREDENTIALS error?
No. Thanks for the answer though @dflook. I'm having another issue right now..
Do you know if its possible to get the "state" of the review? i only want it to apply terraform IF the pull rquest is approved by someone AND the text should be "terraform apply"
I've tried with a bunch of different if statements. if: github.event.review.state == 'approved'
but it seems to be ignored or not working correctly...
It looks like you could use this action to get the number of approving reviews.
Edit: That only works for pull_request & pull_request_review events, not issue_comment, so that won't work for you
Exactly.. I'm kinda lost and confused why i'm the only one who seems to be needing this.
I want this due to the team being used to running atlantis
I made a workaround using labels on pullrequests... Seems to work fine.
why doesn't it post my plans in my pull request?
name: Terraform Plan
on: [pull_request]
jobs:
plan:
runs-on: ubuntu-latest
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
AWS_ACCESS_KEY_ID: ${{ secrets.ACCESS_KEY_ID }}
AWS_SECRET_ACCESS_KEY: ${{ secrets.SECRET_ACCESS_KEY }}
steps:
- name: Checkout
uses: actions/checkout@v2
- name: terraform plan
uses: dflook/terraform-plan@v1
env:
TERRAFORM_HTTP_CREDENTIALS: github.com/somecredentials
with:
path: .
add_github_comment: true
I don't see any problems with that workflow, what happens when it runs? Do you see the plan in the workflow log, or does the job fail entirely?
The only time it actually posts the plan is when you create the pull request.
commits after are not posted as messages even though "add_github_comment" is set to true..
Any existing comment is updated with the new plan. If the plan hasn't changed it may be hard to tell - check the build number in the comment and the edit history.
Isn't it possible adding a new plan for every commit?
guess i could try using the json_plan_path
neither of the outputs available from the terraform plan module is as nice as the one being updated...
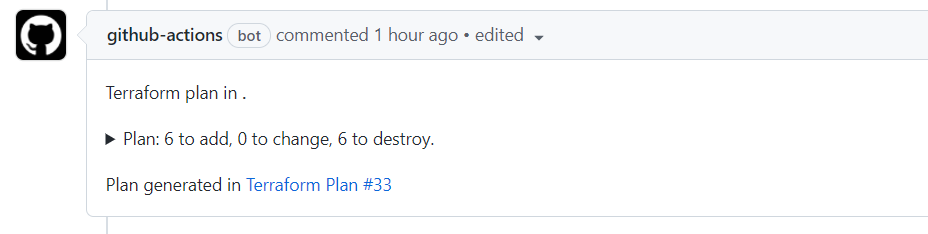
Mine looks like this:
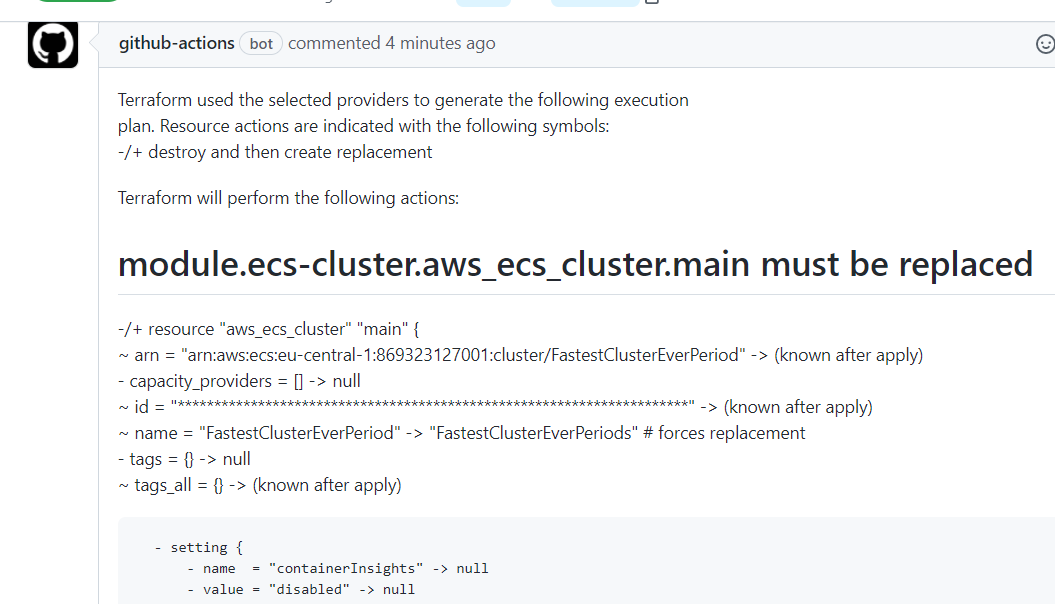 which is very lenghty in the long run.. i'd love if all messages would look like the first pic
which is very lenghty in the long run.. i'd love if all messages would look like the first pic
The comment is always kept up to date with an accurate plan. I'm not sure how useful keeping outdated plans around would be.
I want the old ones deleted and the "updated" plan at the very bottom if it makes sense.
Imagine doing 10 commits after your initial commit where the plan is actually located.
i found a solution. simply removing the comments from the bot in the plan workflow, it will create a new comment.
this is kinda strange tho..
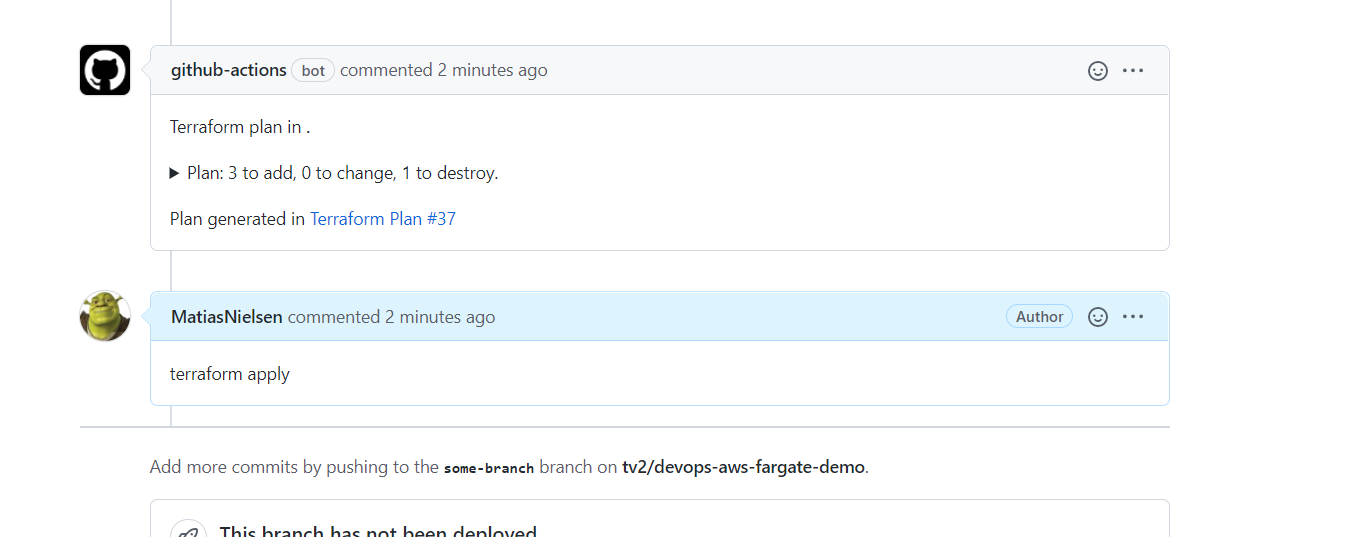
Shouldnt it post a new comment with this?
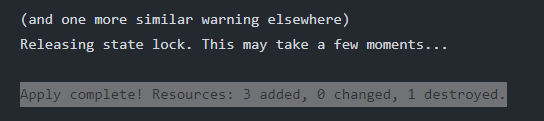
I would expect the existing comment to be updated to say 'Plan applied in Job #xxx'
Can you please enlighten me as to why the destroy doesn't post anything?
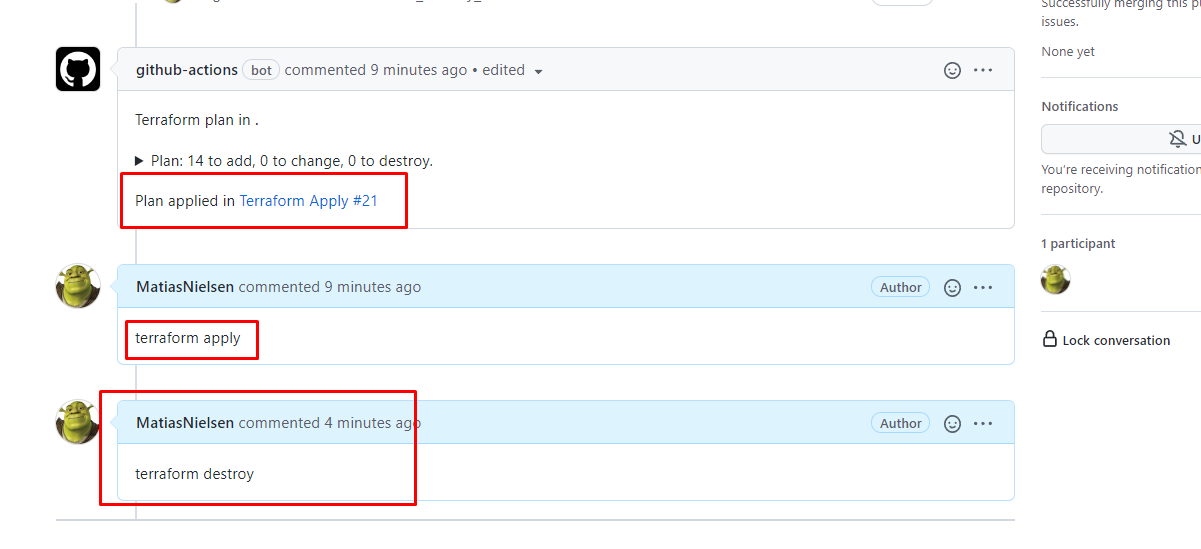
I am btw using this one from your examples;
name: Cleanup
on:
pull_request:
types: [closed]
jobs:
destroy_workspace:
runs-on: ubuntu-latest
name: Destroy terraform workspace
steps:
- name: Checkout
uses: actions/checkout@v2
- name: terraform destroy
uses: dflook/terraform-destroy@v1
with:
path: my-terraform-config
workspace: ${{ github.head_ref }}
dflook/terraform-destroy just does it. A comment isn't created as the plan isn't interesting.
Perhaps dflook/terraform-destroy and dflook/terraform-destroy-workspace could get a add_github_comment input too, and post the result of the destroy.
that is a really good idea
@dflook would know why my TF apply doesn't work? I get this error
Plan: 1 to add, 1 to change, 1 to destroy. Plan not found on PR Generate the plan first using the dflook/terraform-plan action. Alternatively set the auto_approve input to 'true' If dflook/terraform-plan was used with add_github_comment set to changes-only, this may mean the plan has since changed to include changes
also on merge, the `Terraform plan in . in the dev workspace With var files: dev.tfvars
Plan: 1 to add, 1 to change, 1 to destroy.
memo Plan generated in Prepare Terraform-plan #179 doesn't change to TF apply`
@MatiasNielsen how did you accomplish your "Atlantis" type workflow? I have everything working but I still don't understand how you prevent someone entering "terraform apply" in comments before a Approval is done. Could you explain or show how you did it with labels?
@Oaluyi1 Late answer, but you may want to double-check that the inputs to the terraform-apply step match exactly with the inputs to the terraform-plan step, as described in the readme. I accidentally broke the deployment workflow by just changing the label in the PR workflow. Making the labels match solved it for me.
In v1.33.0 the dflook/terraform-plan and dflook/terraform-apply actions now have a destroy input which can be used for generating and applying plans that destroy all resources, while adding the plan to a PR comment.
The dflook/terraform-destroy action is unchanged and will still immediately destroy all resources.