terraform-provider-cloudflare
 terraform-provider-cloudflare copied to clipboard
terraform-provider-cloudflare copied to clipboard
Feature: custom configuration for disk_encryption in cloudflare_device_posture_rule resource
Current Terraform and Cloudflare provider version
Terraform v1.1.6
- provider registry.terraform.io/cloudflare/cloudflare v3.14.0
Description
Disk encryption input argument right now only accept require_all boolean parameter. So it is either enable disk encryption posture check to be enforcing for all drives(including: USB, EFI, backup disks and etc) or makes it permissive.
Obviously if there will be usb drive plugged into computer which will not be encrypted the check will fail in enforcing mode. Same goes for EFI or a boot partition which most of the users(especially linux users) leave unencrypted because there is no secret data there. It also simplifies installation and configuration process when you install an operating system.
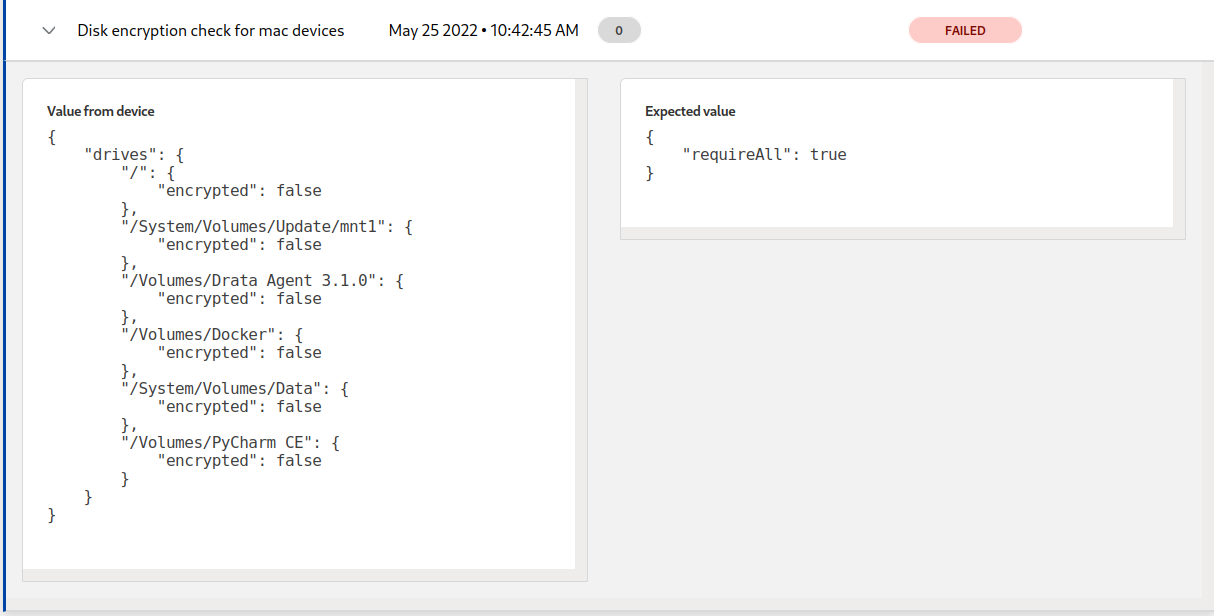
Mac os device example which fails disk encryption checks:
Linux device example which fails disk encryption checks:
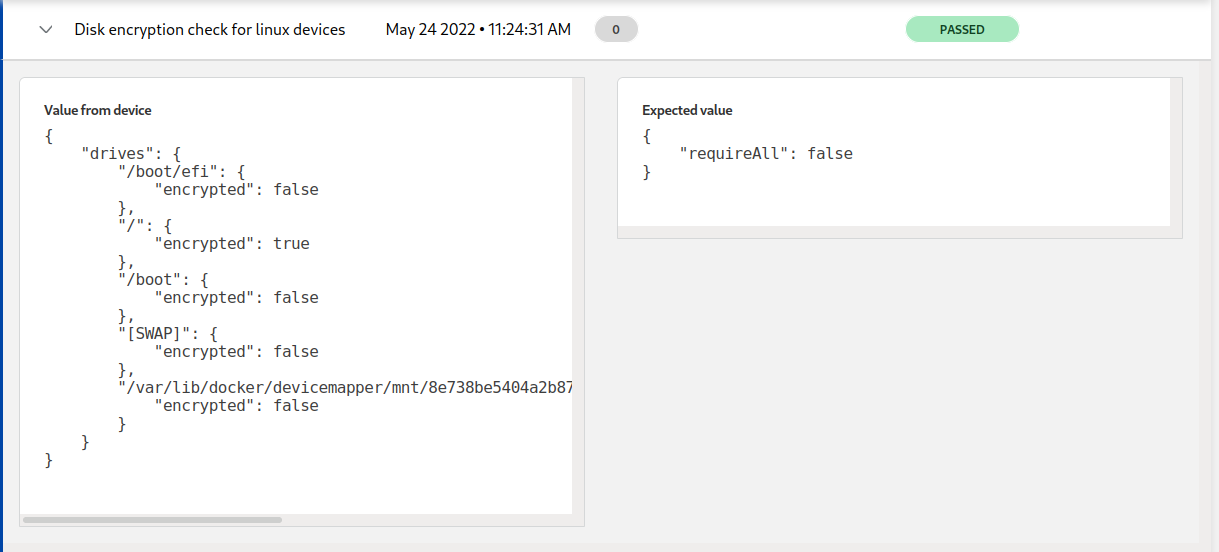
As you can see there is no real value to enforce disk encryption checks for ALL devices because it will simply not work without a filter.
Also looks like API documentation is very outdated on that matter: https://api.cloudflare.com/#device-posture-rules-create-device-posture-rule It does not mention anything about disk encryption type while terraform does support it and UI as well,
I am not sure if this repository is a correct place to lodge this feature request because looks like it should go to a cloudflare API repository itself which looks like internal project. If that's the case please move it to the relevant space.
I know its a big change from backend perspective but it will bring a huge value for cloudflare customers. I am happy to participate in a development process and deliver this feature if this is possible to do.
Use cases
It would be really useful to use result of disk encryption status from device posture rule in cloudflare zero trust policy. For example we can allow/deny access to specific internal resource if disk is encrypted/not encrypted. It will allow us(and other companies as well) to achieve highest level of security and potentially obtain different certifications.
Policy example:
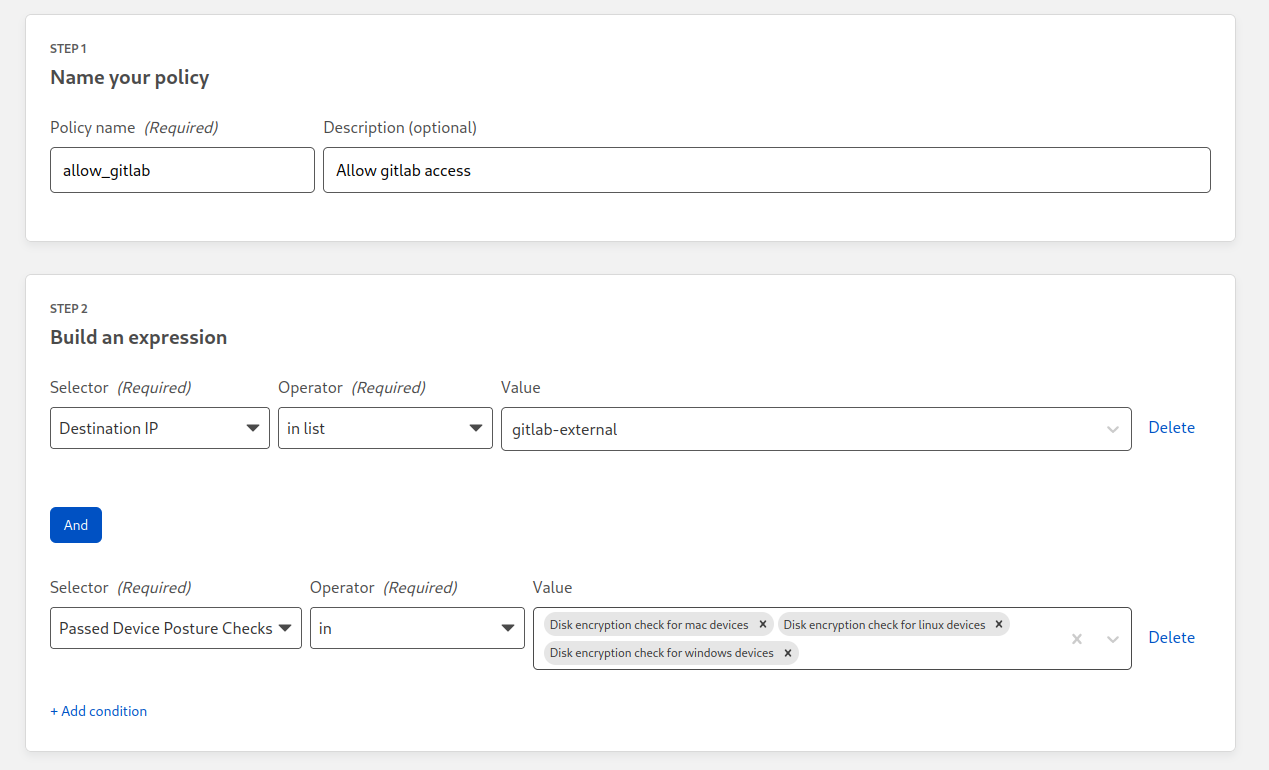
Potential Terraform configuration
I suggest it should support 2 modes: inclusive and exclusive. Looks like the same pattern is already used in split tunnel configuration and domain fallback sections for zero trust.
These 2 modes should be mutually exclusive. Examples:
...
resource "cloudflare_device_posture_rule" "mac_devices_disk_encryption" {
account_id = var.account_id
name = "Disk encryption check for mac devices"
type = "disk_encryption"
description = "Disk encryption check for mac devices"
schedule = "24h"
match {
platform = "mac"
}
input {
mode = "exclude"
devices = [
"/var/lib/docker/*",
"[SWAP]",
"/boot",
]
}
}
resource "cloudflare_device_posture_rule" "linux_devices_disk_encryption" {
account_id = var.account_id
name = "Disk encryption check for linux devices"
type = "disk_encryption"
description = "Disk encryption check for linux devices"
schedule = "24h"
match {
platform = "linux"
}
input {
mode = "include"
devices = [
"/",
"/backup",
]
}
}
This way we can filter out which mount points we do care about.
References
No response