terraform-provider-cloudflare
 terraform-provider-cloudflare copied to clipboard
terraform-provider-cloudflare copied to clipboard
when creating cloudflare_api_token with permission for logs Write on the zone level, permission is assigned on the account level
Confirmation
- [X] My issue isn't already found on the issue tracker.
- [X] I have replicated my issue using the latest version of the provider and it is still present.
Terraform version
0.14.8
Affected resource(s)
cloudflare_api_token
Terraform configuration files
resource "cloudflare_api_token" "zone_tokens" { for_each = local.zonemap name = "${each.key}-key" policy { permission_groups = [ data.cloudflare_api_token_permission_groups.all.permissions["Logs Write"], ] resources = { "com.cloudflare.api.account.${var.account_id}" = "" } } policy { permission_groups = [ data.cloudflare_api_token_permission_groups.all.permissions["DNS Write"], data.cloudflare_api_token_permission_groups.all.permissions["Access: Apps and Policies Write"], data.cloudflare_api_token_permission_groups.all.permissions["SSL and Certificates Write"], data.cloudflare_api_token_permission_groups.all.permissions["Zone Settings Write"], data.cloudflare_api_token_permission_groups.all.permissions["Zone Write"], data.cloudflare_api_token_permission_groups.all.permissions["Firewall Services Write"], data.cloudflare_api_token_permission_groups.all.permissions["Page Rules Write"], data.cloudflare_api_token_permission_groups.all.permissions["Workers Routes Write"], data.cloudflare_api_token_permission_groups.all.permissions["Logs Write"], ] resources = { "com.cloudflare.api.account.zone.${each.value}" = "" } } }
Debug output
No response
Panic output
No response
Expected output
token created with permissions for Logs Write on the zone level
Actual output
token created with permissions for Logs Write on the account level
Steps to reproduce
execute the code above
Additional factoids
in the api docs for permissions : https://developers.cloudflare.com/api/tokens/create/permissions logs write, like many others exists on both account and zone level, all work fine with the exception of the logs write so far.
References
No response
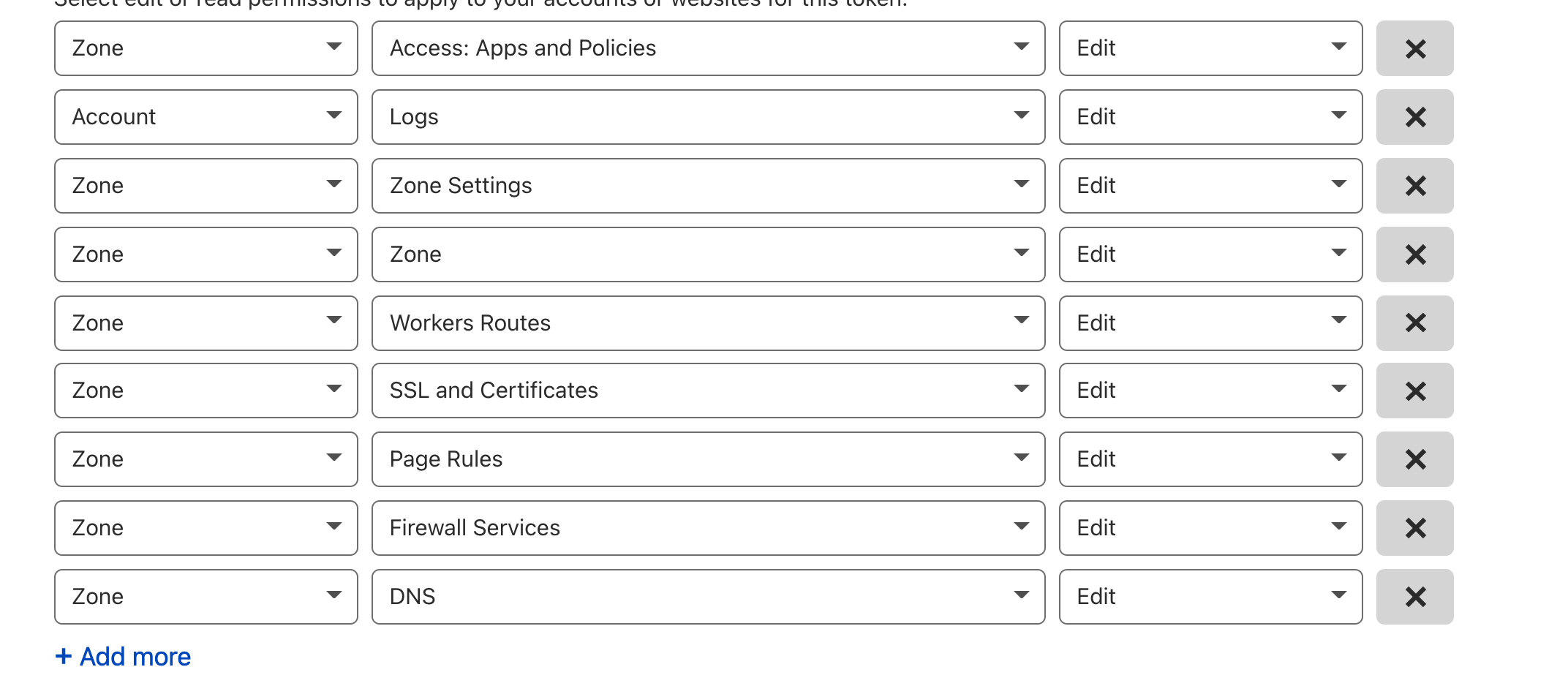
here is the proper screenshot, where even when account level log write is added separately, zone level log write still saves it as account level log write:
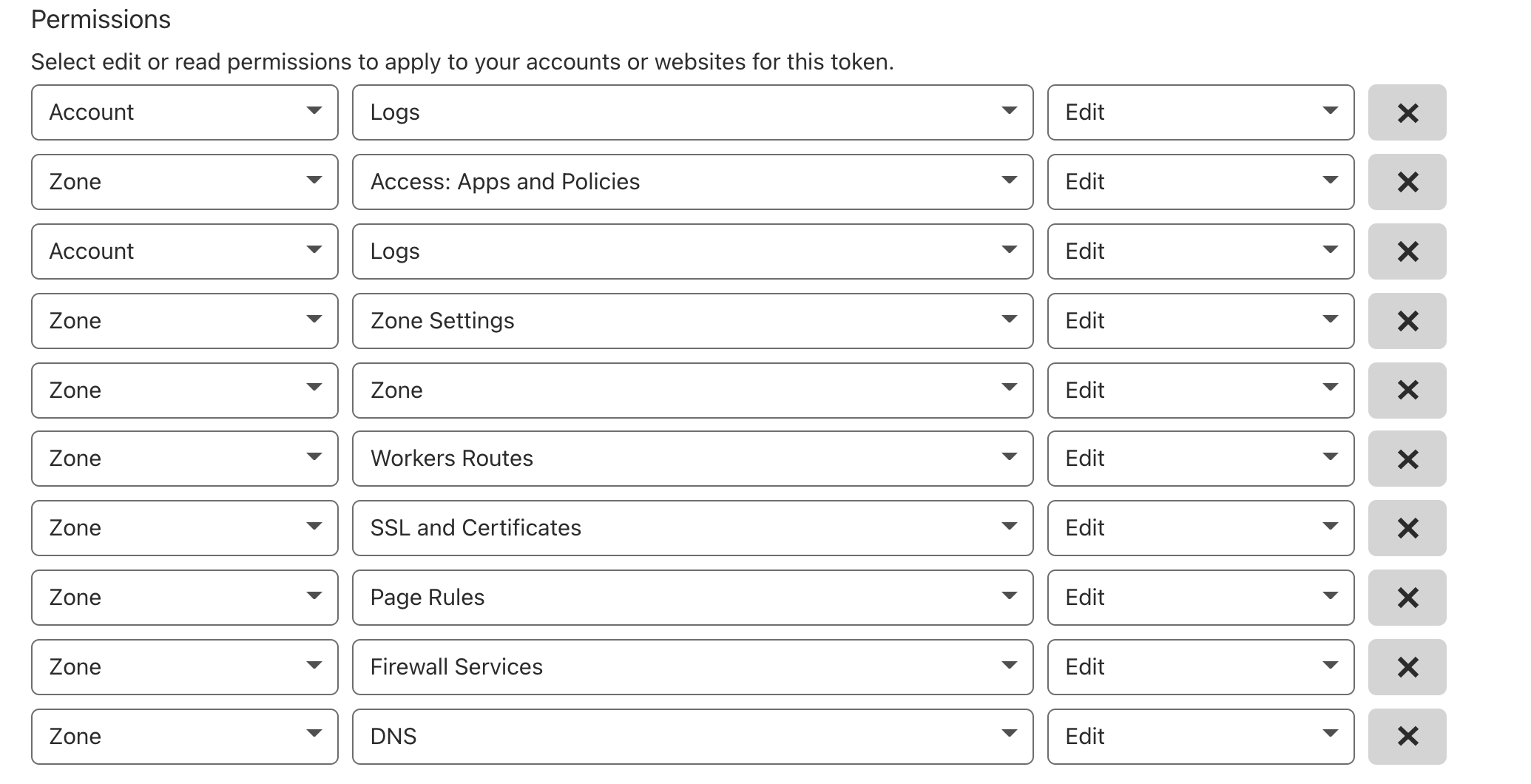
on another note, when i correct the key in the UI afters its created in terraform by changing one of those account:logs write to zone:logs write, that part of the key functions as expected
Hey, first of all if you want to use Logs Write permission only on the zone, you should remove the account level permission:
policy {
permission_groups = [
data.cloudflare_api_token_permission_groups.all.permissions["Logs Write"],
]
resources = {
"com.cloudflare.api.account.${var.account_id}" = ""
}
}
Second, you are right about UI. Even after removing above permission, UI shows Logs Write on the account level. But opening dev tools in your browser or using CF rest api will show you that permissions are done just right.
tl:dr It is UI bug and thus not related to terraform provider.
hi @jacobbednarz , any plans to get this fixed?
they are not done right since when i try to use it, it fails with permission error, until i get into UI and fix it there manually. then things works, but i run the module again, it reverts it to the state where its assigned to account 2 times
From: Uroš @.> Sent: Tuesday, May 11, 2021 8:44 AM To: cloudflare/terraform-provider-cloudflare @.> Cc: vital4ik @.>; Author @.> Subject: Re: [cloudflare/terraform-provider-cloudflare] when creating cloudflare_api_token with permission for logs Write on the zone level, permission is assigned on the account level (#1004)
Hey, first of all if you want to use Logs Write permission only on the zone, you should remove the account level permission:
policy { permission_groups = [ data.cloudflare_api_token_permission_groups.all.permissions["Logs Write"], ] resources = { "com.cloudflare.api.account.${var.account_id}" = "" } }
Second, you are right about UI. Even after removing above permission, UI shows Logs Write on the account level. But opening dev tools in your browser or using CF rest api will show you that permissions are done just right.
tl:dr It is UI bug and thus not related to terraform provider.
— You are receiving this because you authored the thread. Reply to this email directly, view it on GitHubhttps://na01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fcloudflare%2Fterraform-provider-cloudflare%2Fissues%2F1004%23issuecomment-838408988&data=04%7C01%7C%7C2752b395cd084866a03f08d9147a80a1%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637563338638535417%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=RqfrgxdiVD7wng8Z8eQiZlQS66m%2Bq4VbVKEi10wMn8o%3D&reserved=0, or unsubscribehttps://na01.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fnotifications%2Funsubscribe-auth%2FABYWEM7PGCBM3ZX3VLSDIZ3TNERCLANCNFSM4ZZ72O2Q&data=04%7C01%7C%7C2752b395cd084866a03f08d9147a80a1%7C84df9e7fe9f640afb435aaaaaaaaaaaa%7C1%7C0%7C637563338638545370%7CUnknown%7CTWFpbGZsb3d8eyJWIjoiMC4wLjAwMDAiLCJQIjoiV2luMzIiLCJBTiI6Ik1haWwiLCJXVCI6Mn0%3D%7C1000&sdata=QDhVQHMWuw8HDR0D1hoCyUL0YTdDNM3d4KFA8tNB2m0%3D&reserved=0.
Hey, first of all if you want to use
Logs Writepermission only on the zone, you should remove the account level permission:policy { permission_groups = [ data.cloudflare_api_token_permission_groups.all.permissions["Logs Write"], ] resources = { "com.cloudflare.api.account.${var.account_id}" = "" } }Second, you are right about UI. Even after removing above permission, UI shows Logs Write on the account level. But opening dev tools in your browser or using CF rest api will show you that permissions are done just right.
tl:dr It is UI bug and thus not related to terraform provider.
the issue is, even if i remove the account part, and only assign it on the zone level it still assigns it on the account level:
policy {
permission_groups = [
data.cloudflare_api_token_permission_groups.all.permissions["DNS Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Access: Apps and Policies Write"],
data.cloudflare_api_token_permission_groups.all.permissions["SSL and Certificates Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Zone Settings Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Zone Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Firewall Services Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Page Rules Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Workers Routes Write"],
data.cloudflare_api_token_permission_groups.all.permissions["Logs Write"],
]
resources = {
"com.cloudflare.api.account.zone.${each.value}" = "*"
}
this still assigns it on the account level only. after i run this, i have to manually go and fix this in UI for each zone separately
I think it's because of the current wrong structure of cloudflare_api_token_permission_groups data source.
The code that creates the map for data source depends on the objects returned by the Permission Group List API like following.
for _, v := range permissions {
permissionDetails[v.Name] = v.ID
ids = append(ids, v.ID)
}
However, some permission group objects share names but have different IDs because they have different levels. e.g) zone, account
# Response of GET user/tokens/permission_groups
...
{
"id": "3e0b5820118e47f3922f7c989e673882",
"name": "Logs Write",
"description": "Grants write access to logpush jobs",
"scopes": [
"com.cloudflare.api.account.zone"
]
},
{
"id": "96163bd1b0784f62b3e44ed8c2ab1eb6",
"name": "Logs Write",
"description": "Grants write access to logpush jobs",
"scopes": [
"com.cloudflare.api.account"
]
},
{
"id": "1e13c5124ca64b72b1969a67e8829049",
"name": "Access: Apps and Policies Write",
"description": "Grants write access to Cloudflare Access account resources",
"scopes": [
"com.cloudflare.api.account"
]
},
{
"id": "959972745952452f8be2452be8cbb9f2",
"name": "Access: Apps and Policies Write",
"description": "Grants write access to Cloudflare Access zone resources",
"scopes": [
"com.cloudflare.api.account.zone"
]
},
...
any ETA on when this can be fixed plz?
This functionality has been released in v3.29.0 of the Terraform Cloudflare Provider.
Please see the Terraform documentation on provider versioning or reach out if you need any assistance upgrading.
For further feature requests or bug reports with this functionality, please create a new GitHub issue following the template. Thank you!