amplify-cli
 amplify-cli copied to clipboard
amplify-cli copied to clipboard
amplify import auth - imported cognito user pool - aws-exports.js missing oauth values?
Before opening, please confirm:
- [X] I have installed the latest version of the Amplify CLI (see above), and confirmed that the issue still persists.
- [X] I have searched for duplicate or closed issues.
- [X] I have read the guide for submitting bug reports.
- [X] I have done my best to include a minimal, self-contained set of instructions for consistently reproducing the issue.
- [X] I have removed any sensitive information from my code snippets and submission.
How did you install the Amplify CLI?
npm
If applicable, what version of Node.js are you using?
14.20.0
Amplify CLI Version
9.2.1
What operating system are you using?
Mac
Did you make any manual changes to the cloud resources managed by Amplify? Please describe the changes made.
Cognito pool that we connected to our Amplify app was pre-existing, and we just imported it using amplify import auth. Not sure if that counts as manual change or not, but here is info in any case.
Amplify Categories
auth
Amplify Commands
Not applicable
Describe the bug
We have an Amplify project that we started, all goes rather well, and we have to integrate federated auth with existing Cognito pool. Logically, we connected the Cognito pool to our Amplify app, and did amplify import auth and that part went okay, we see that Cognito pool is connected etc. Now here's the thing that's not really going well, and I can't figure out how to do it:
In our Cognito pool we have App Client for which we want to use the Hosted UI for logging in (as Cognito is Auth with custom provider). Here's the screenshot (some values random) of Cognito App Client Hosted UI:
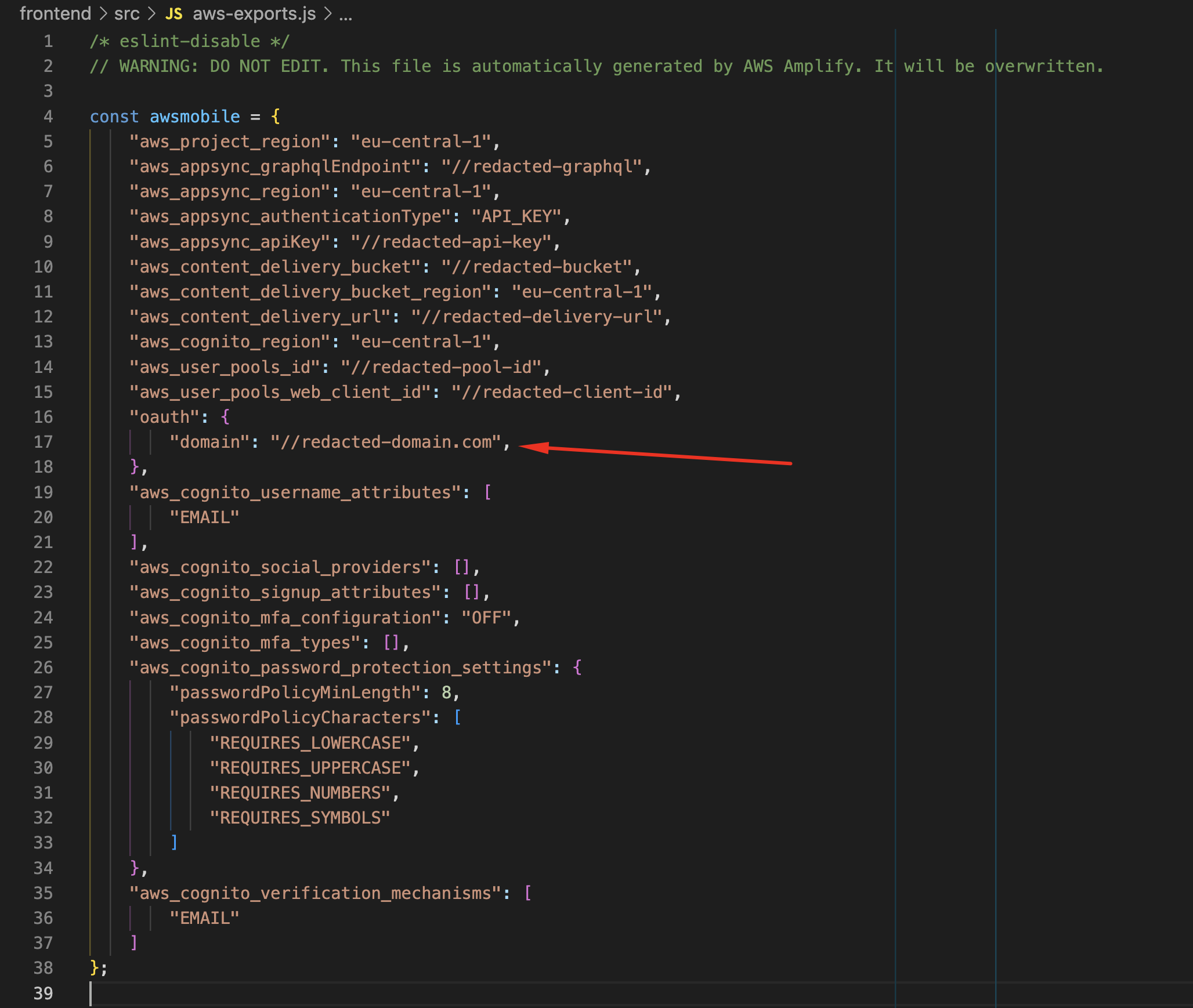
As you can see where I highlighted with arrow, oauth properties are missing completely, all of them except the domain ... If I add them manually like this, then FederatedSignIn works no problem:

As this matches exactly the values from Cognito App Hosted UI properties, FederatedSignIn works ...
Now here's the thing, what I've did is hardcoding / changing values into file that is not supposed to be manually changed. I'm wondering, what can be done to get these values properly populated based on the values that are in Cognito App Hosted UI, basically that I get in aws-exports.js exactly what I manually added, but being generated by Amplify CLI itself.
Any ideas?
Expected behavior
aws-exports.js should contain all the oauth properties generated.
Reproduction steps
I'm not sure if these are easily reproducible, but let's try ...
-
Create a completely fresh Amplify app (not going to cover that from scratch in steps ...)
-
In AWS console create Cognito pool
-
Fill it out with some users
-
Under App Integration -> App client list -> Create App Client
-
Fill out details for Hosted UI setting, adding redirect URL 4.1. Identity Provider field needs to be custom provider (and not Cognito) 4.2 OAuth 2.0 grant types - Set to "Authorization code grant" 4.3 OpenID Connect scopes - Set to "aws.cognito.signin.user.admin", "email", "OpenID", "profile"
-
Save changes
Connect Cognito Pool to your newly created app by using this guide I guess (https://docs.amplify.aws/cli/auth/import/)
Expectations are that in aws-exports.js file "oauth" property contains all the scopes, redirectUrl and other properties.
GraphQL schema(s)
No response
Project Identifier
No response
Log output
# Put your logs below this line
Additional information
No response
Hello @petar-prog91, thank you for reaching out. I was unable to reproduce on creating a Cognito resource on the console and the importing the resource. on additional testing I was able to reproduce the issue by utilizing the following steps.
- Create a cognito user pool with oauth attributes.
- Run
amplify import authand select the user pool. - update the user pool on the console.
Could you please let us know if there were any changes made after the user pool was imported. I observed the inconsistency in attributes in my amplify application as well.
As a workaround I utilized amplify remove auth to a imported Cognito resource and then ran amplify import auth to add the resource with the updated attributes.
hi @ykethan - so to give you the answer to what you asked:
- First time we had ran
amplify import auth- resources have not been changed. Hosted UI values of the app haven't been imported on the first import at all. - We tried doing
amplify remove authand then importing again, but that didn't bring correct properties / attributes either. - Changing of the Cognito Pool directly wasn't done, but once we noticed that things are missing, we started changing things on Cognito Hosted UI properties (have in mind that these are apps that are using Custom Provider with OpenID & Oauth) - maybe that's where the key issue lies?
- Overall - I would have also expected that if the infrastructure resource changes in the cloud, that these changes get registered by amplify CLI and let me know that we need to pull those updates. Mainly because, Cognito pools in our case are maintained by Terraform templates.
Hope this clarifies it a bit! Let me know if you have any more questions.
Hello @petar-prog91, thank you for the information. I was able to replicate the behaviour using Custom Provider with OpenID. Marking this as bug.
I would have also expected that if the infrastructure resource changes in the cloud, that these changes get registered by amplify CLI and let me know that we need to pull those updates. Mainly because, Cognito pools in our case are maintained by Terraform templates.
This would make a great feature request, I went ahead and created as issue on the Amplify CLI repository. Please refer to https://github.com/aws-amplify/amplify-cli/issues/10939. Please feel free in adding any information.
Great @ykethan thanks for the response and confirmation! For now we have an workaround (a bit hardcoding things), but looking forward to having this bug fixed :)
Also nice that you took my expectations for a feature request, appreciate it.
Hi @petar-prog91
Currently we don't support Custom Identity providers in amplify-cli. The only supported providers are:
'COGNITO', 'Facebook', 'Google', 'LoginWithAmazon', 'SignInWithApple'
I can take this a FR to support Custom identity providers as well.
As a workaround you can try post-push hook to update values in aws-exports.js
Had a very similar issue. Solved it by doing amplify remove auth, amplify push, amplify import auth, amplify push. If you don't do a push between remove and import, several oauth values such as scope and responseType will be missing and signin will fail.
Hi @akshbhu,
I can take this a FR to support Custom identity providers as well. As a workaround you can try
post-pushhook to update values inaws-exports.js
Was just trying this but it appears as though updating in post-push happens after the values are sent back to Amplify via amplify push. Am i missing something here? Would love to be able to manually override for now, but can't get it working via code.